picoCTF-2023-部分wp
web
findme
访问页面,是一个登录的页面,账号密码test/test!
抓包看到跳转到一个页面,
(/images/2023picoctf/image-20230327162639364.png)
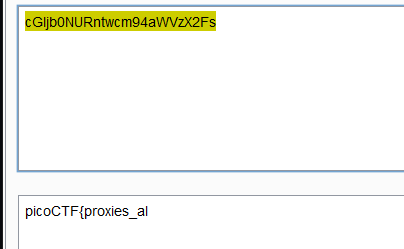
访问这个/next-page/id=cGljb0NURntwcm94aWVzX2Fs
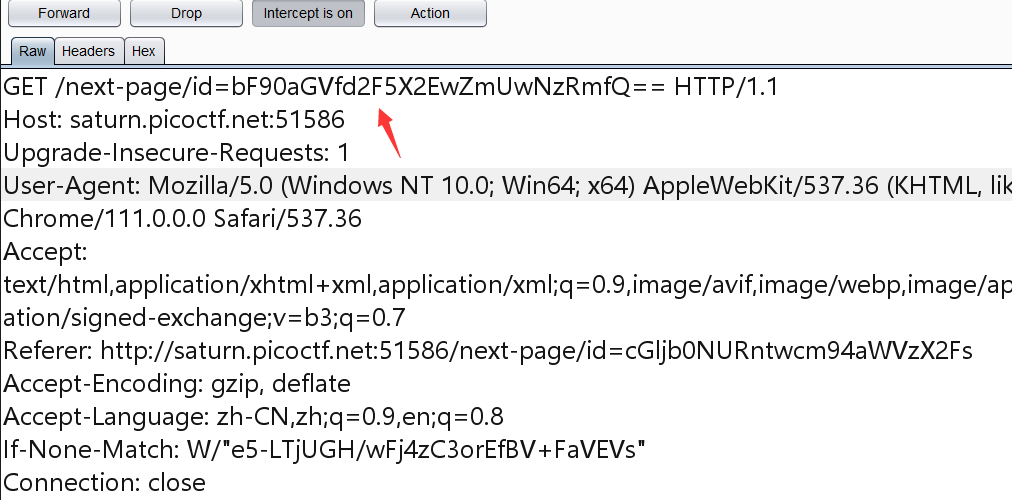
抓包,中间又会跳转一个页面,直接跳出来一个页面,看到有一个id,好像是base64,直接拼接
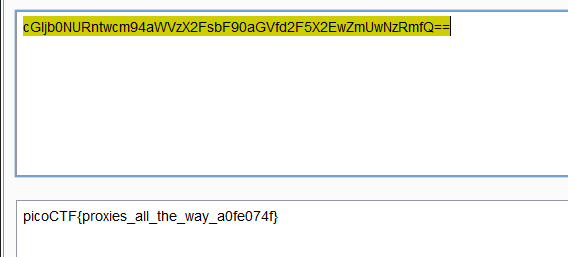
flag:picoCTF{proxies_all_the_way_a0fe074f}
chrono
How to automate tasks to run at intervals on linux servers?
机翻:如何自动执行任务以在 Linux 服务器上定期运行?
给了账号密码端口,直接连上去
定时任务的命令 crontab ,执行crontab -l 发现没有,crontab的文件目录在/etc/下 以cron开头,
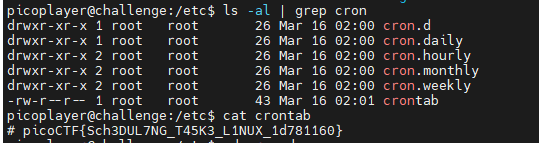
在 challenge目录下也有flag
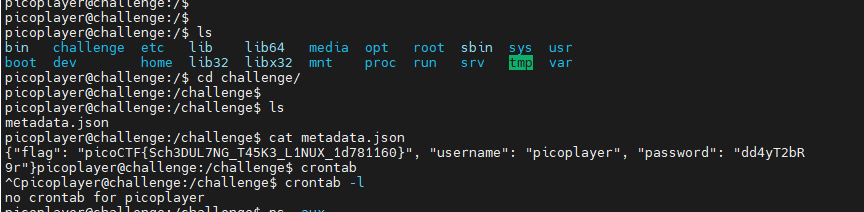
flag:{“flag”: “picoCTF{Sch3DUL7NG_T45K3_L1NUX_1d781160}”, “username”: “picoplayer”, “password”: “dd4yT2bR
hideme
Every file gets a flag.
The SOC analyst saw one image been sent back and forth between two people. They decided to investigate and found out that there was more than what
机翻一下:每个文件都有一个标志。
SOC 分析师看到一张图像在两个人之间来回发送。 他们决定展开调查,发现事情远不止于此
直接下载一张图片
foremost 有一个zip包
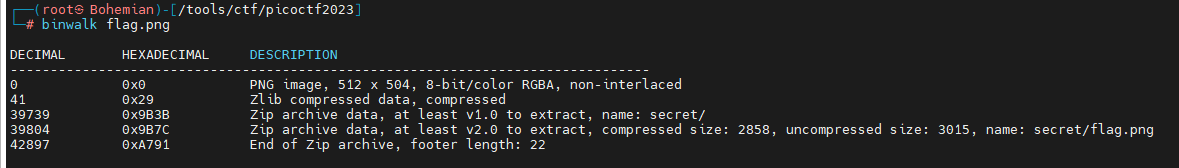
ristretto flag.png
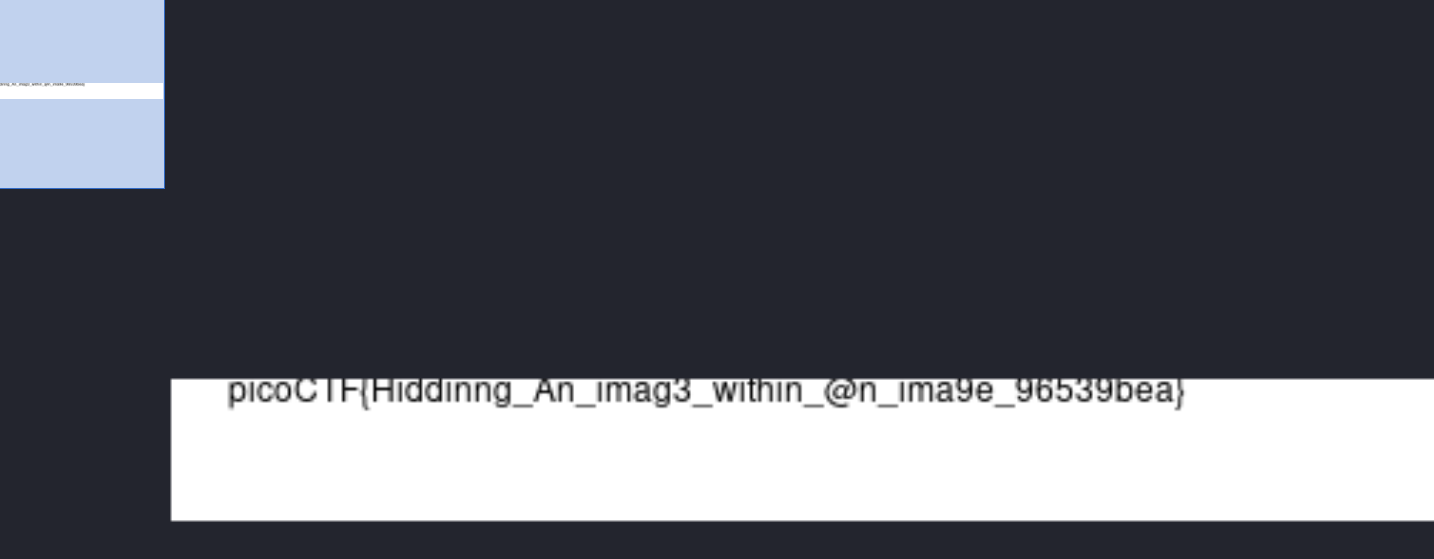
flag:pIcoCTF{Hiddinng_An_imag3_within_@n_ima9e_96539bea}
MatchTheRegex
正则匹配
输入框输入东西,
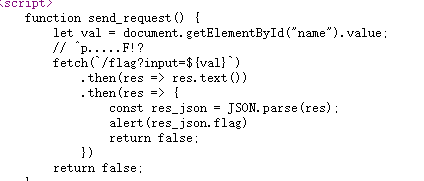
p开头 F结尾
| ^n | 匹配任何开头为 n 的字符串。 |
|---|---|
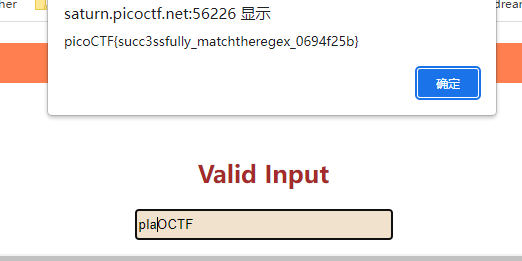
flag:picoCTF{succ3ssfully_matchtheregex_0694f25b}
SOAP
money-ware
Flag format: picoCTF{Malwarename}The first letter of the malware name should be capitalized and the rest lowercase.Your friend just got hacked and has been asked to pay some bitcoins to 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX. He doesn’t seem to understand what is going on and asks you for advice. Can you identify what malware he’s being a victim of?
标记格式:picoCTF{Malwarename}
恶意软件名称的首字母应大写,其余字母小写。
您的朋友刚刚被黑客入侵,并被要求向 1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX 支付一些比特币。 他似乎不明白发生了什么,并向你征求意见。 你能确定他是哪种恶意软件的受害者吗?
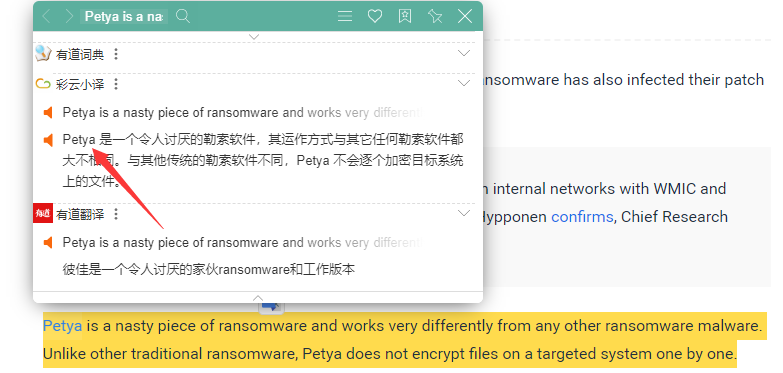
flag:picoCTF{Petya}
repetitions
下载文件,拖到ida
base64 多解几次
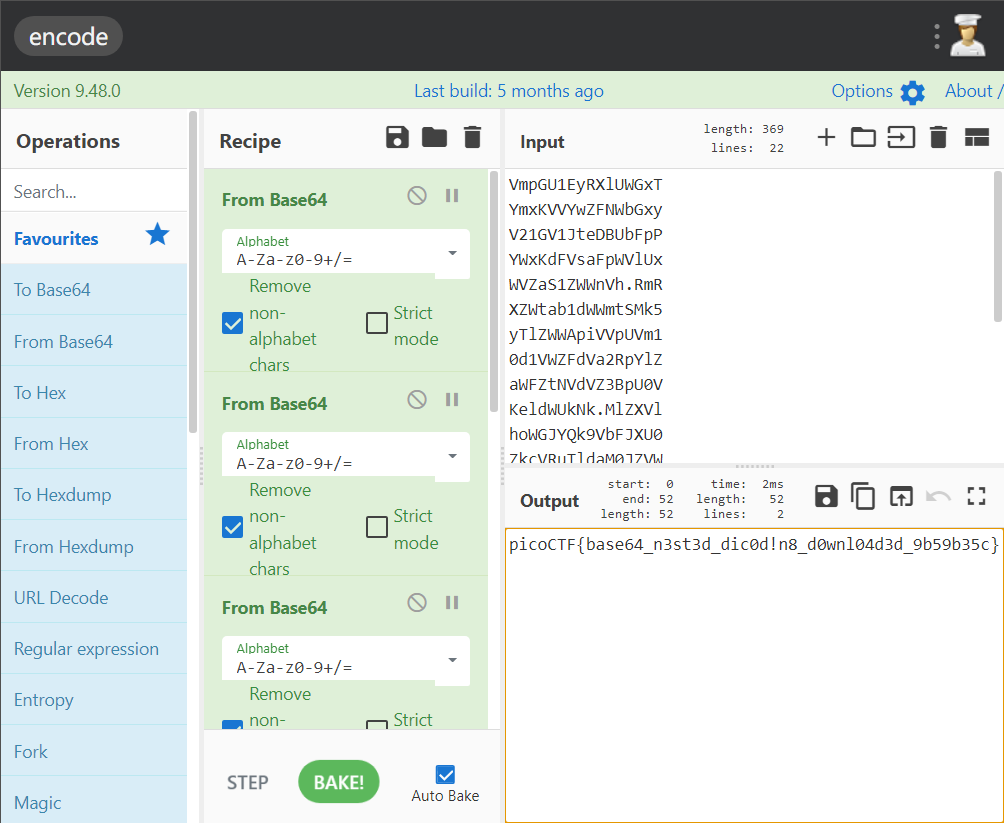
flag:picoCTF{base64_n3st3d_dic0d!n8_d0wnl04d3d_9b59b35c}
rule
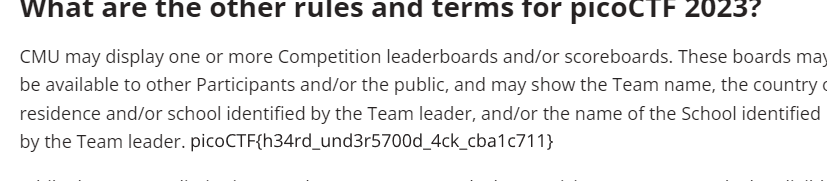
flag:picoCTF{h34rd_und3r5700d_4ck_cba1c711}
FindAndOpen
下载pacp包,中间有个base解一下
这个是下面压缩包的密码
再解一下,就可以了
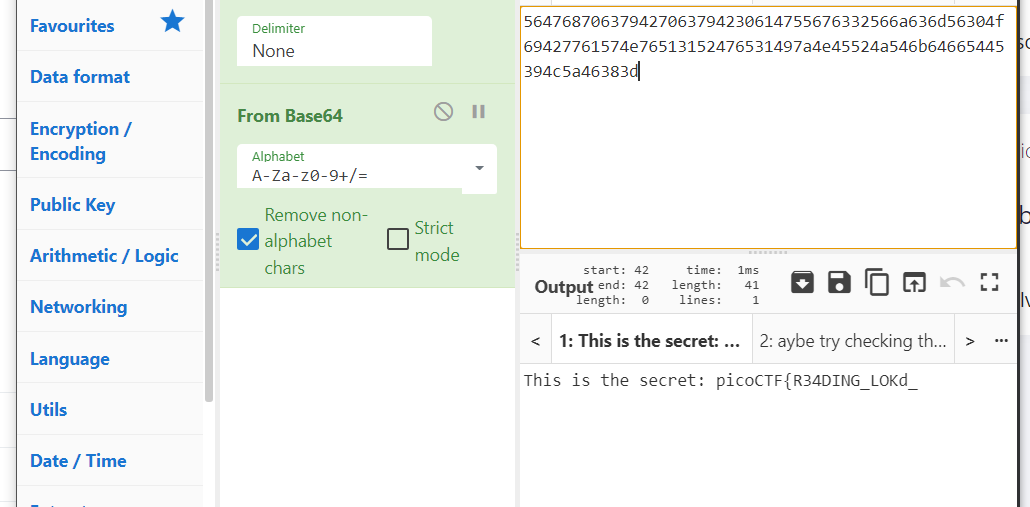
picoCTF{R34DING_LOKd_fil56_succ3ss_419835ef}
Reverse
reverse
直接拖到ida里
safe opener2
直接拖到ida
timer
拖到Androidkill里
找到buildconfig文件即可
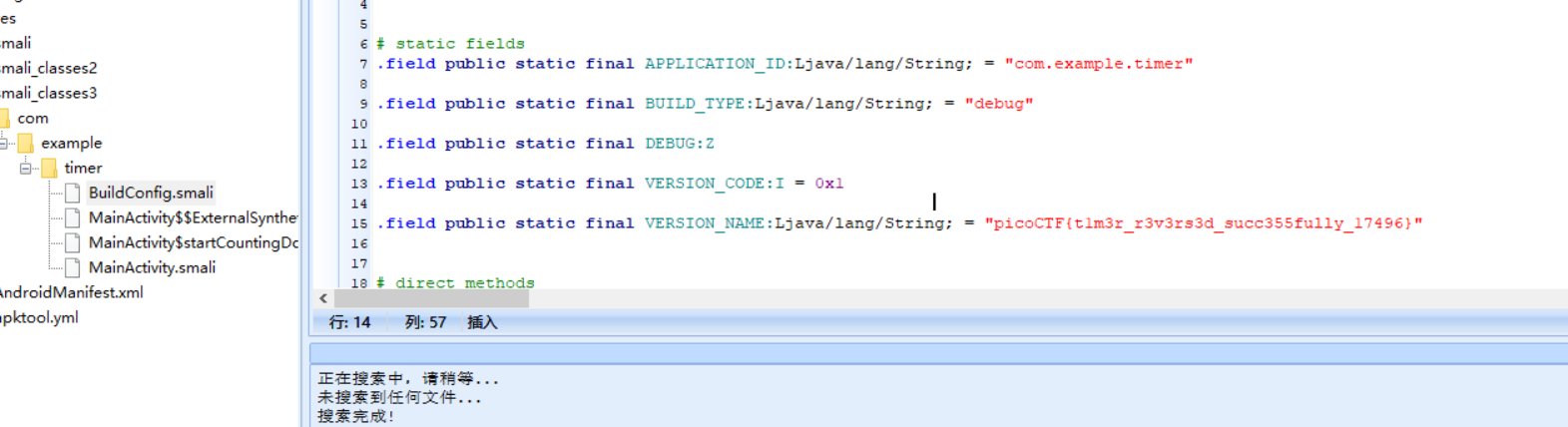
flag:picoCTF{t1m3r_r3v3rs3d_succ355fully_17496}